Update from 2021-05-31:
- Option
ifnamewas renamed todevice - This tutorial is valid for 21.02-rc2 (or newer) and recent snapshots
Introduction
DSA stands for Distributed Switch Architecture and is Linux kernel subsystem for network switches. It's an upstream replacement for OpenWrt's swconfig framework and many new routers use DSA drivers instead of swconfig drivers.
In DSA each switch port is a separated Linux interface. It means ip / ifconfig command will show interfaces like lan1, lan2, wan, etc.
DSA switch ports can be used as standalone interfaces (common solution for WAN) or can be bridged using Linux bridge interface. In the later case switch will still be able to route traffic on the hardware level so it won't affect performance.
Each port can be part of maximum of one bridge only.
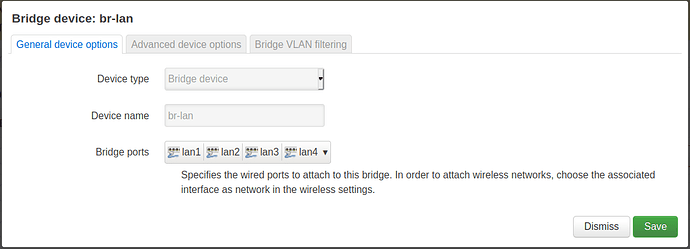
Simple ports bridging
In the simplest scenario switch ports are simply bridged using Linux bridge interface and OpenWrt configures that interface with an IP protocol.
In such case all devices connected to bridged ports can communicate each other and router itself.
Example:
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
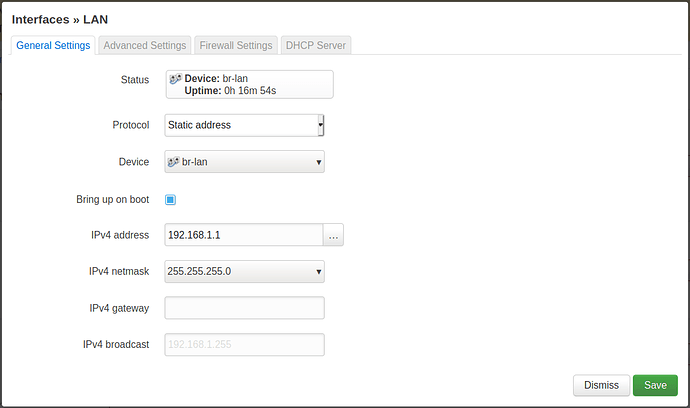
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
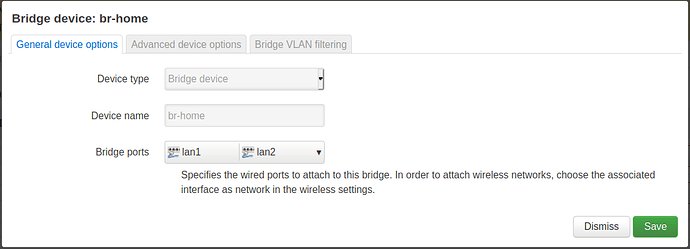
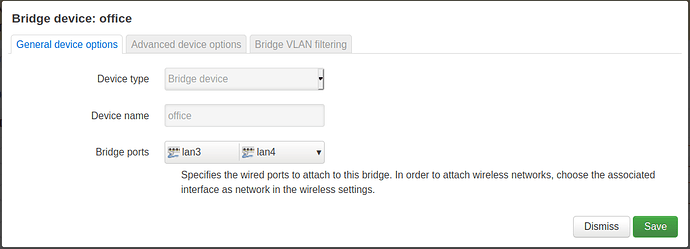
Multiple networks (using bridges)
A switch can be setup to group selected ports into separated networks by using multiple bridge interfaces. With separated firewall zones devices connected to different port groups won't be able to communicate each other.
Example:
config device
option name 'br-home'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
config device
option name 'office'
option type 'bridge'
list ports 'lan3'
list ports 'lan4'
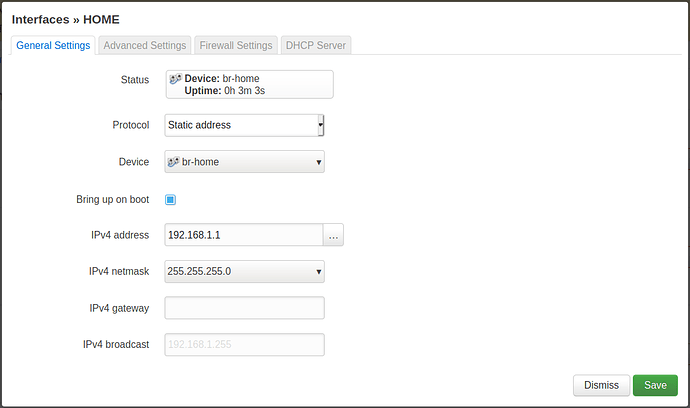
config interface 'home'
option device 'br-home'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
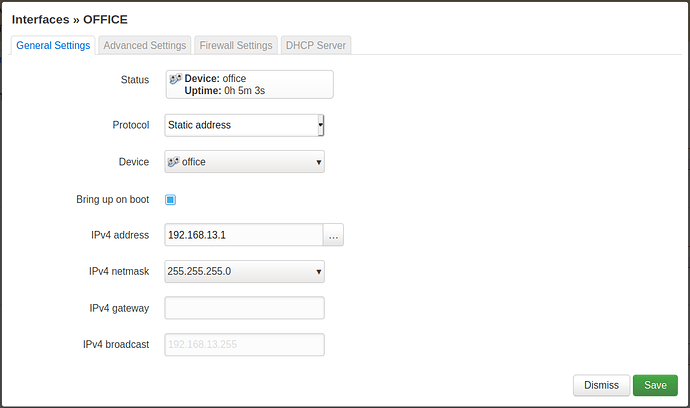
config interface 'office'
option device 'office'
option proto 'static'
option ipaddr '192.168.13.1'
option netmask '255.255.255.0'
Multiple networks (using VLANs)
Ports can also be separated (grouped) using single bridge with multiple VLANs. That requires assigning interfaces to correct software VLANs.
Example:
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
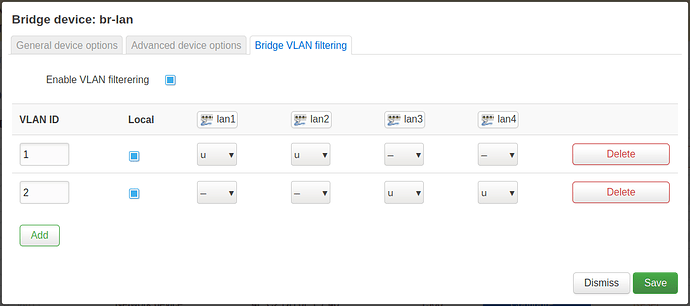
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1'
list ports 'lan2'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan3'
list ports 'lan4'
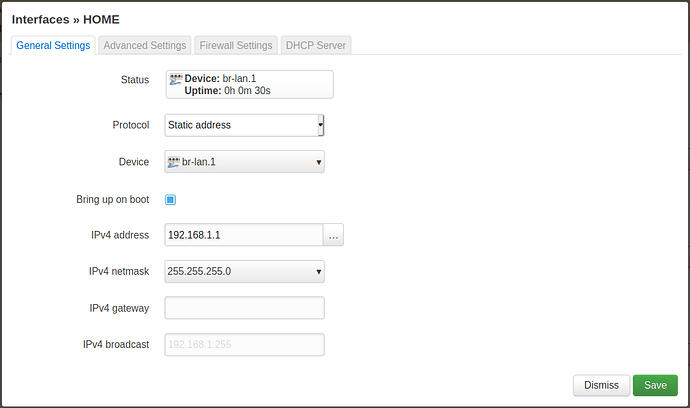
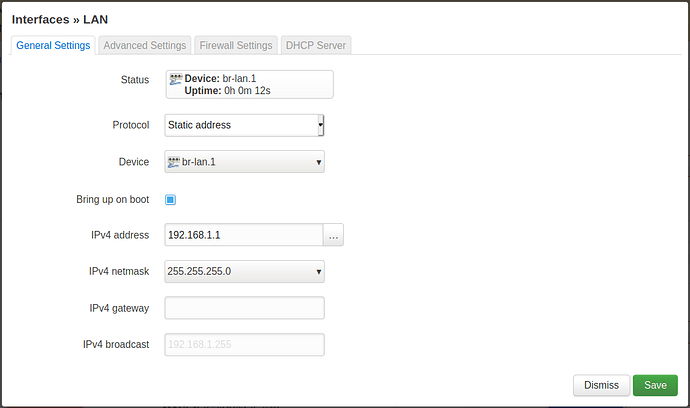
config interface 'home'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
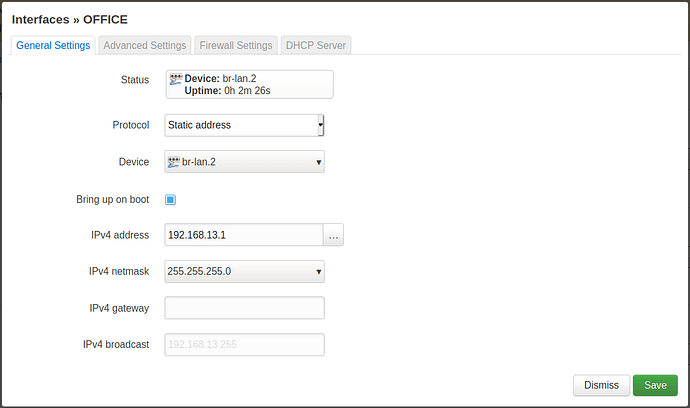
config interface 'office'
option device 'br-lan.2'
option proto 'static'
option ipaddr '192.168.13.1'
option netmask '255.255.255.0'
VLAN tagged traffic
With proper bridge VLAN configuration it's also possible for selected port to use VLAN tagged traffic. It also requires assigning OpenWrt interface to the correct software VLAN.
Example:
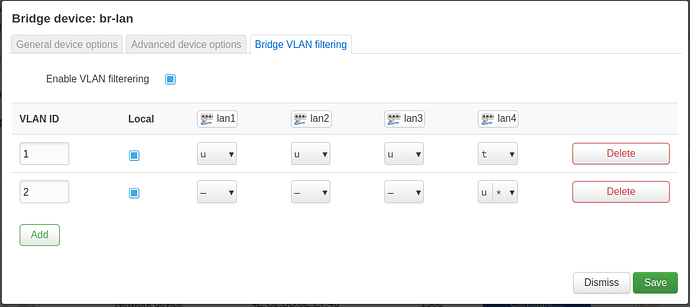
Port lan4 uses tagged packets for VLAN 1 and has PVID 2.
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config bridge-vlan
option device 'br-lan'
option vlan '1'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4:t'
config bridge-vlan
option device 'br-lan'
option vlan '2'
list ports 'lan4:u*'
config interface 'lan'
option device 'br-lan.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'