So my config is as follows.
I have a main router with openwrt fully set and working with VLANs and everything.
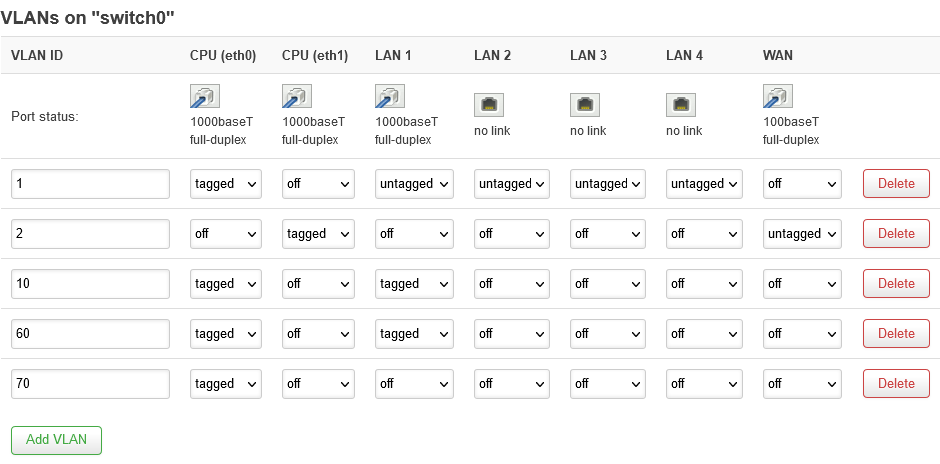
I have a VLAN aware switch connected to port 1 of this router:
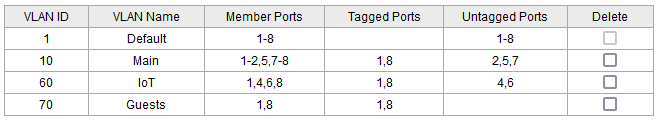
I want to create an almost dumb AP with openwrt and connect it on the switch (port 8 of the switch used by the dumb AP).
For the dumb AP I am using a flashed Mi 4A with OpenWrt 21.02.0-rc3 r16172-2aba3e9784.
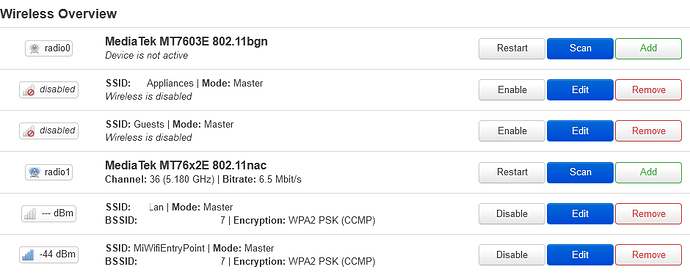
What I want is to have the ability to have separate SSIDs which will take packets and tag them so I can pass them to the main router and provide networking.
I am new to all this so whatever I do I seem to end up just locking myself out.
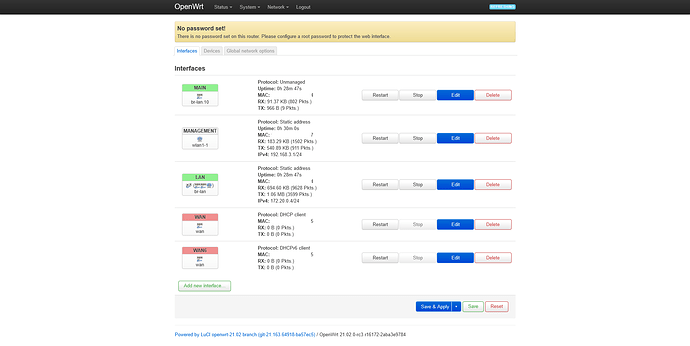
By default openwrt has these as physical devices:
wan, eth0, lan1, lan2, br-lan(lan1, lan2) and wlan1.
lan1, lan2 and wan are seen as switch ports and eth0 as the switch I suppose.
And interfaces:
wan and wan6 with DHCP and lan on the br-lan device.
I have created one more wlan1-1 ph. device with a management interface with a static ip and separate mac (assigned to a separate SSID) just so every time I lock myself out of the device I don't have to debrick it.
I want to create three SSIDs (Main (5Ghz), IoT(2.4Ghz), Guests(2.4Ghz)) and with probably a dumb(unmanaged?) interface just pass the traffic to lan after tagging it accordingly (Main->VLAN10, IoT->VLAN60, Guest->VLAN70) so it passes tagged through the switch to the main router etc.
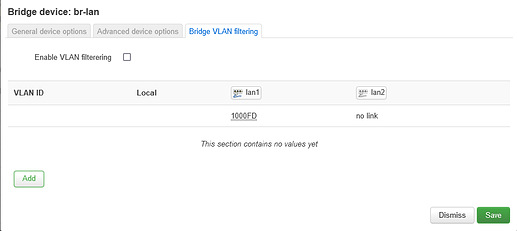
The problem is that I don't even have a switch menu on my installation. I only have the option to enable VLAN on the bridge physical device, create subdevices (f.e.: br-lan.10) but there I am doing something completely wrong and I cannot get it to work.
I tried a lot of different configurations with separate bridges and all and nothing worked. Even if I enable VLAN on the bridge I immediately lose access to the router.
Some side notes: The firewall daemon is disabled. DCHP is supposed to operate on the main router for all the VLANs as I have interfaces there giving IPs. I suppose I should take more of my info from:
https://forum.openwrt.org/t/mini-tutorial-for-dsa-network-config
but I cannot practically and successfully apply it to my case.
Any help would be greatly appreciated (I am HIGHLY beyond my comfort zone fiddling with these network settings).