Hi,
recently I decided that I wanted to separate my private and work devices on my home/work from home network and give guests their own WiFi with access to internet only.
As it's the first time I set up VLANs with separate firewall zones and traffic rules I would love for you to sanity check my settings and maybe give me feedback on how to simplify things and tips on best practices.
It's step 7 below that I'm especially eager to get your opinion on.
When I first set up the OpenWRT router using a RPi 4B (eth0) with a TP-Link UE300 (eth1) I only had a basic 8 port unmanaged switch and a Fritzbox I reconfigured as AP and connected to the RPi via the switch.
A couple of days ago I got a ZyXel GS1200-8HP and NWA50AX.
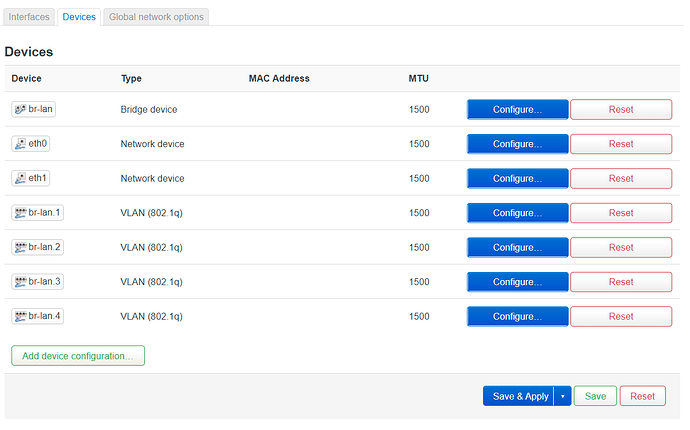
Here is how I went about changing from a single lan zone to separate VLANs:
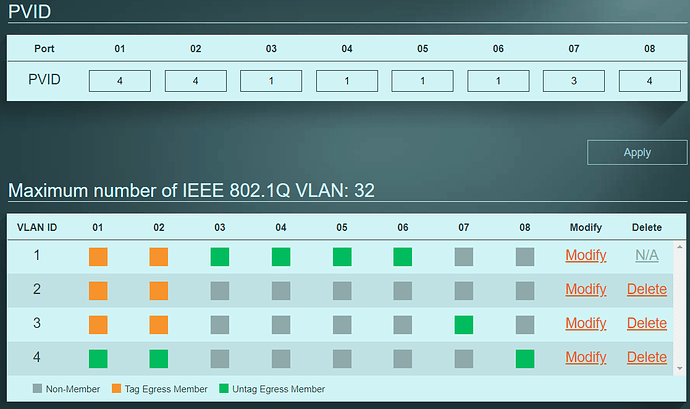
- First I connected the managed switch to my old switch and logged into its webinterface to confirm the default configuration was set to all ports in VLAN 1 untagged, PVID 1 and management VID 1.
- Then I followed the Mini tutorial for DSA network config and enabled VLAN filtering on the existing "br-lan" bridge device making it a trunk with VLAN IDs 1-3 tagged and ID 4 untagged+primary. As to not lock myself out of the router I did not click "Save & Apply" until after step 3 was complete.
EDIT: To clarify: I chose to set VLAN filtering on the bridge device because I found it to be convenient to see the VIDs and their tagging settings all in one place and because LuCI generated and named the necessary VLAN devices automatically for me.
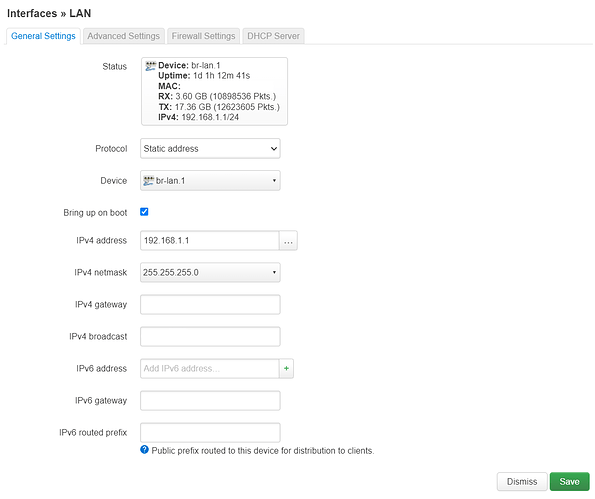
- Changed the existing "lan" interfaces device setting from "br-lan" to "br-lan.1" and only now clicked "Save & Apply".
- Set the switches port configuration of ports 1 (router) and 2 (AP) the same as the "br-lan" in step 2 and the rest of the ports untagged members of the desired VLANs with their PVIDs in the untagged VLAN.
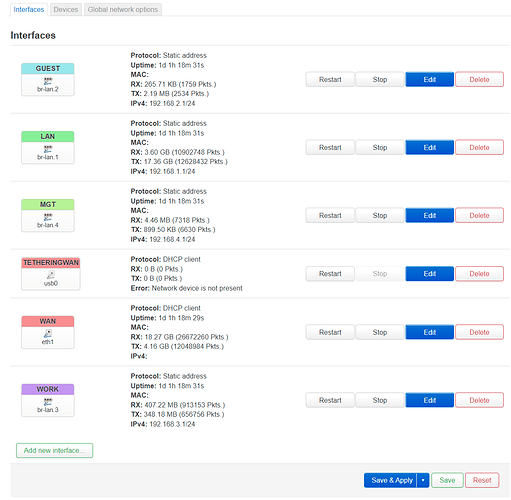
- Added interfaces for the guest (br-lan.2), work (br-lan.3) and management (br-lan.4) VLANs, each with their own firewall zone and DHCP server and to keep it simple with their IP address ranges corresponding to their VLAN IDs, eg. guest 192.168.2.1/24 and so on.
- Connected the AP to switch port 2 and set it up with SSIDs on separate VLANs as needed.
- At first I configured the new firewall zones "guest" and "work" identical to "lan", which was automatically configured as "accept/accept/accept" at first set up of the router.
But this gave devices on guest not only access to the internet but also to the router.
So as per How to block luci access to pubblic vlan? I changed them to "reject/accept/reject" and "lan" and "mgt" to forward reject though I'm not sure if the latter is needed.
Then I added traffic rules to allow DHCP and DNS access for "guest" and "work" and also blocked access to the modems webinterface while I was at it.
Screenshot of firewall zones. The forward from lan to mgt is meant to be only temporary, see step 8 below.
- After everything was up and running and I had tested the forward from "lan" to "mgt" was working I changed the switch's and AP's IP address to DHCP client and their management VLAN IDs from 1 to 4 and set static leases in the 192.168.4.0/24 range on the router.