Hi everyone,
some days ago I discovered OpenWRT and I am pretty impressed about all the possibilities! Unfortunately I could not bring my setup to run, which I dream of for some time. I am new to this forum and would appreciate any kind of help! And yes, I'm a noob (yet)!
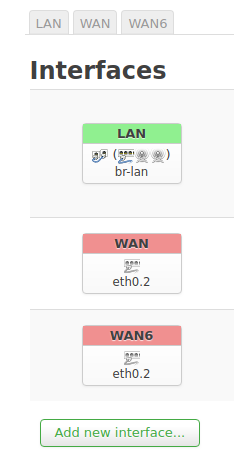
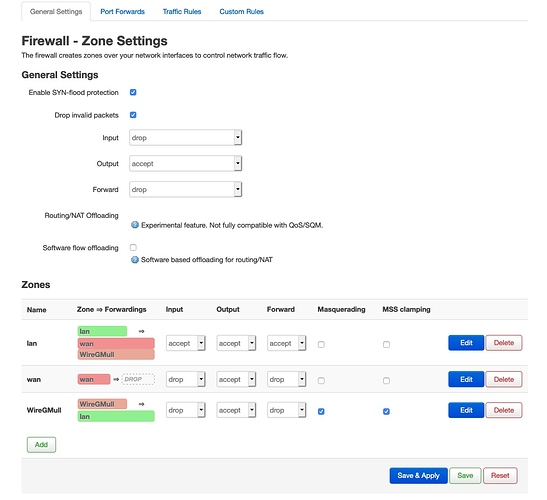
All I want is the typical setup described in many posts here, nevertheless nobody seems to have my exact problem (it seems real problems start afterwards like here, where this setup seems to be the point of start... LAN access in Wireguard tunnel). I want a Mullvad client (Wireguard) running on the router (mine is a TL-WRD3600) and in addition a Wireguard server to be connected to my smartphone when I am not at home.
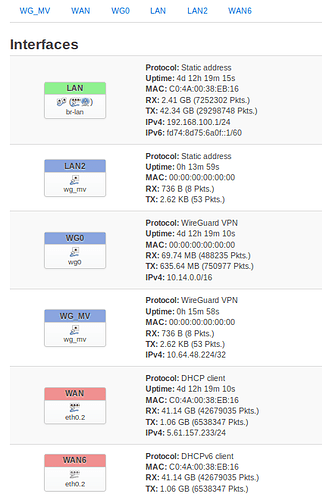
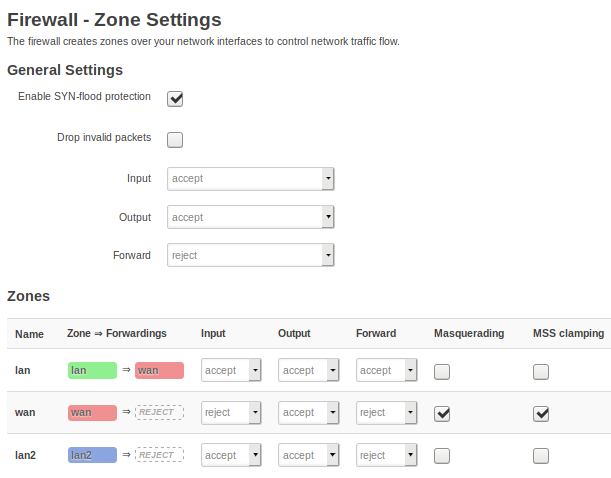
The thing is, both interfaces run absolutely flawless. I configured the Mullvad client as in their OpenWRT guide (https://mullvad.net/en/guides/running-wireguard-router/), but placed it (as suggested in some posts in this forum) in the WAN firewall zone (first WG interface) to keep it simple.
I also added the server in the LAN zone and I am able to connect to it from my phone (second WG interface).
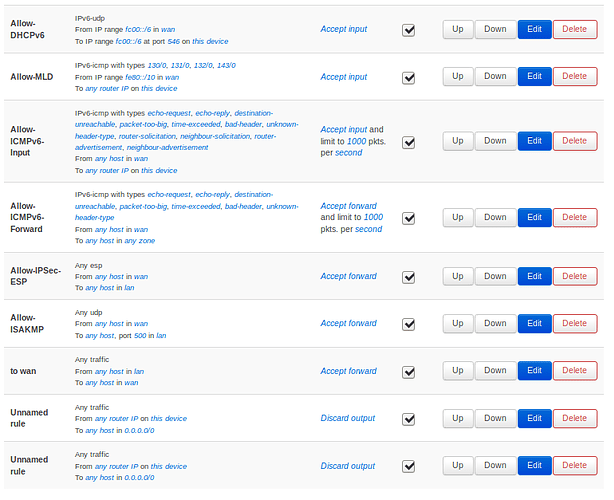
I did not add any rules, nor firewall zones nor anything else. Nevertheless I added the adblocker module which is also working fine (also with both interfaces).
BUT: in the moment I enable the Mullvad client, I can not surf via my Android phone anymore. I can not reach my local IPs, nor the router or the internet at all. Surfing directly from LAN works perfectly nevertheless and I see that the traffic goes over Mullvad servers (by their page "Am I Mullvad").
Is there anything special I have to add? Something like: "Ongoing traffic over the Wireguard server shall be routed to the Mullvad client"?
I really appreciate your work here and thank you in advance! Please tell me if this is the wrong place for this question or if you need more information!
Best regards!


 )
)