Here is what I did:
So what did I do:
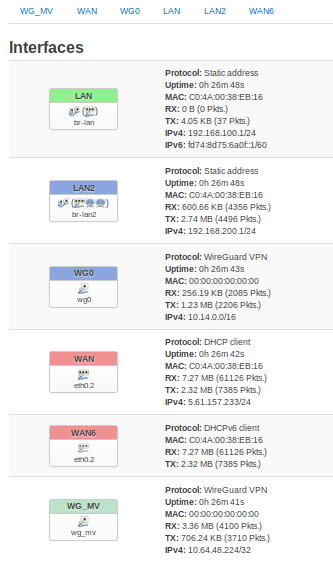
1: add a Wireguard tunnel to your phone like described here. My interface name is wg0.
Rboot and figure out that the tunnel works. There are many differnt tutorial for that. Let's say read on when it works.
2: add a Wireguard interface for Mullvad following this guide:
Important: do not acctivate "Route Allowed IPs", ignore DNS stuff for the beginning. Coming to DNS leaks is something for later.
Interface name for me is wg_mv.
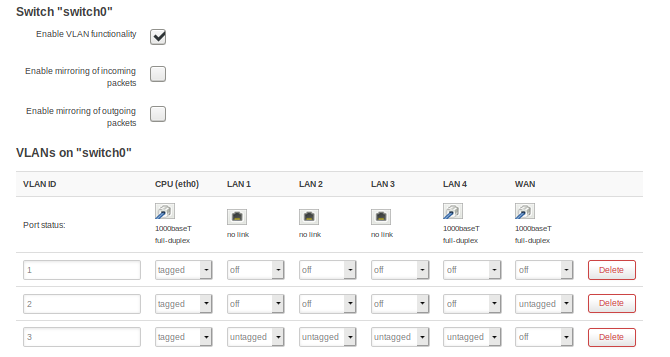
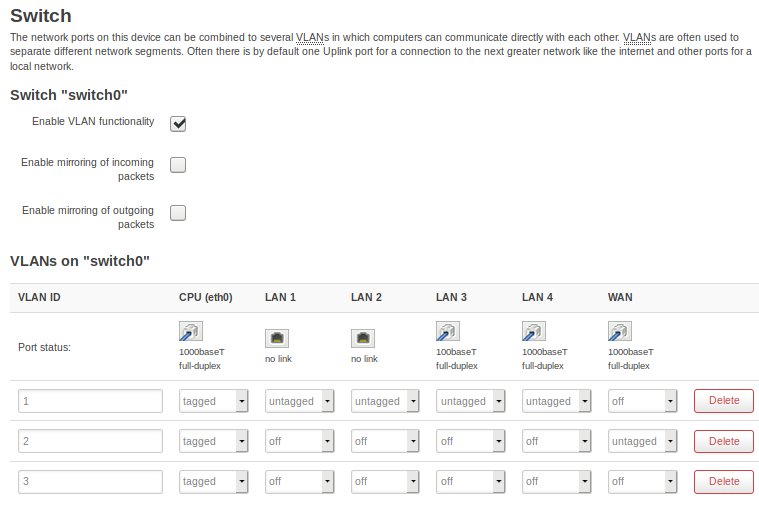
3: add a new VLAN (Network/Switch) by clicking on "Add". Set eth0 on tagged, rest off
4:add new interface "lan2", configured as "lan", with different IPv4 range (for example my LAN starts at 192.168.100.1, lan2 at 192.168.200.1).
Configure DHCP that both ranges do not collide (when using my IPs let it as it is, since it will give addresses from 100 to 250).
Under Physical settings: set "bridged interface", choose new VLAN eth0.3 as interface.
5: add following rules in /etc/config/network
config rule
option in 'lan2'
option dest '0.0.0.0/0'
option priority '2'
option lookup '2'
config rule
option in 'wg0'
option dest '0.0.0.0/0'
option priority '3'
option lookup '2'
config route
option interface 'wg_mv'
option target '0.0.0.0'
option netmask '0.0.0.0'
option table '2'
Change interface names fitting to yours, when not using mine. "wg0" is the "phone tunnel" (server), "wg_mv" the one for mulvlad (client).
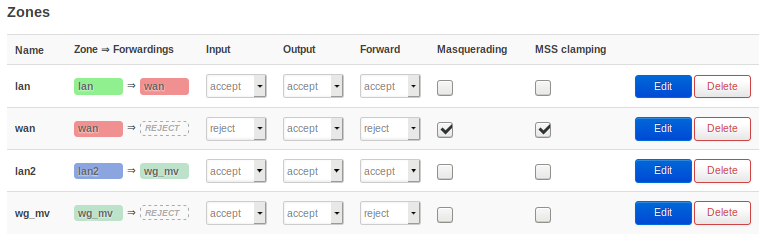
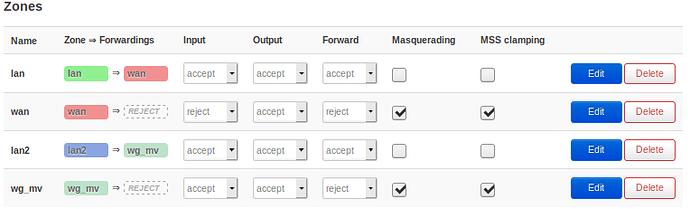
6: configure firewall like this:
lan: lan -> wan; accept, accept, accept
wan: wan -> reject; reject, accept, reject, Masquerading on, MSS clamping on
lan2: lan2 -> wg_mv; accept, accept, accept
wg_mv: wan -> reject; reject, accept, reject, Masquerading on, MSS clamping on
lan zone contains: lan
wan zone contains: wan, wan6
lan2 zone contains: lan2, wg0
wg_mv zone contains: wg_mv
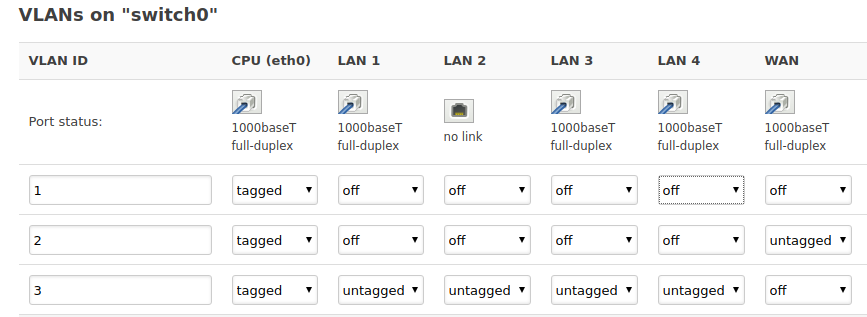
7: now switch traffic from eth0.1 to 0.3. You do this under Network/switch by setting all untagged port in eth0.1 to off, and all off port (besides WAN) on eth0.3 to untagged. Leave WAN as is in eth0.3 and also CPU.
8: now move your WIFI interfaces from lan to lan2.
9: reboot and check am.i.mullvad.net. It should show green (maybe not DNS) from phone and from LAN.
Errors I made:
- for switching traffic you must also move WIFI interfaces. Only switching traffic when there are connected devices in WLAN does nothing.
- make sure to add the rules under /etc/config/network, nowhere else!
- make sure to have a firewall zone for mullvad (wg_mv), and one new for lan2, containing lan2 AND wg0 (phone tunnel).
- do not play around with VPN PBR before. This should also work somehow, but with this steps I could make it work, not before!
After all it should look like this (or similar):