Is it really that simple? To check, I enter all found addresses into the config. It turns out something like this:
[Interface]
PrivateKey = ██████████████████████████████████████h3G3I=
# PublicKey = ██████████████████████████████████████OA2zg=
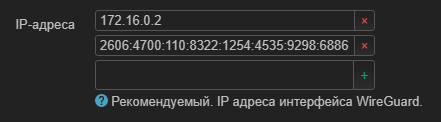
Address = 172.16.0.2
Address = 2606:4700:110:8322:1254:4535:9298:6886
DNS = 1.1.1.1
[Peer]
PublicKey = ██████████████████████████████████████Pfgyo=
Endpoint = engage.cloudflareclient.com:2408
# Endpoint = 162.159.192.9:0
# Endpoint = [2606:4700:d0::a29f:c009]:0
AllowedIPs = 64.15.112.0/24,64.15.115.0/24,64.15.118.0/23,64.15.123.0/24,64.15.126.0/24,70.32.133.0/24,103.111.147.0/24,104.237.164.0/24,104.237.167.0/24,104.237.168.0/22,104.237.172.0/24,104.237.190.0/24,136.22.130.0/23,136.22.132.0/23,156.38.33.0/24,156.38.34.0/23,156.38.37.0/24,156.38.39.0/24,176.29.0.0/24,176.29.203.0/24,176.29.205.0/24,176.29.209.0/24,176.29.210.0/24,176.29.215.0/24,176.29.216.0/21,176.29.224.0/21,176.29.253.0/24,176.29.255.0/24,176.126.58.0/24,185.192.249.0/24,185.225.248.0/24,197.230.59.0/24,197.230.70.0/24,208.117.234.0/24,208.117.236.0/24,208.117.238.0/24,208.117.240.0/24,208.117.250.0/24,208.117.252.0/24,208.117.254.0/24
AllowedIPs = 2001:fb0:109f:12::/64,2001:fb0:109f:14::/64,2001:fb0:109f:18::/63,2001:fb0:109f:8007::/64,2001:fb0:109f:8009::/64,2001:fb0:109f:8010::/64,2001:fb0:109f:8013::/64,2001:fb0:109f:8014::/64,2001:4430:f:104::/64,2001:4430:f:106::/63,2001:4430:f:108::/63,2001:4430:f:10a::/64,2001:4430:f:112::/64,2001:4430:f:114::/64,2001:4430:f:116::/63,2001:4430:f:118::/64,2400:9800:1b:1b::/64,2407:0:0:3d::/64,2620:11a:a000::/48,2620:11a:a011::/48,2620:11a:a01c::/48,2620:11a:a01f::/48,2620:11a:a024::/47,2620:11a:a029::/48,2620:11a:a02a::/48,2620:11a:a02d::/48,2620:11a:a02e::/48,2620:11a:a031::/48,2620:11a:a033::/48,2620:11a:a034::/48,2620:11a:a036::/47,2620:11a:a038::/46,2620:11a:a03c::/48,2620:11a:a0f1::/48,2a00:1588:d801::/48,2a00:1588:d802::/48,2a0f:f4c1:2::/48
Next, you need to install “wireguard-tools” and “luci-i18n-wireguard-ru” will not hurt. This is done as I remember in System → Software with a router connected to the Internet. Before searching, you need to click “Update lists…” otherwise the search will not work.
It would seem that I installed only 2 packages, but the Installed tab shows 5. All the necessary packages are installed together (wireguard-tools, kmod-wireguard, luci-app-wireguard, luci-i18n-wireguard-ru, luci-proto-wireguard)
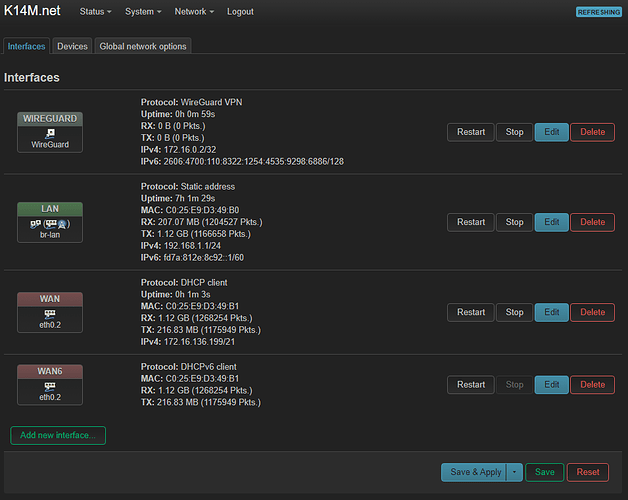
I reboot the router and make a backup just in case. Now in the Status tab, at the very bottom, the WireGuard item has appeared, which says No WireGuard interfaces configured.
By analogy with OpenVPN, I do everything in a similar way.
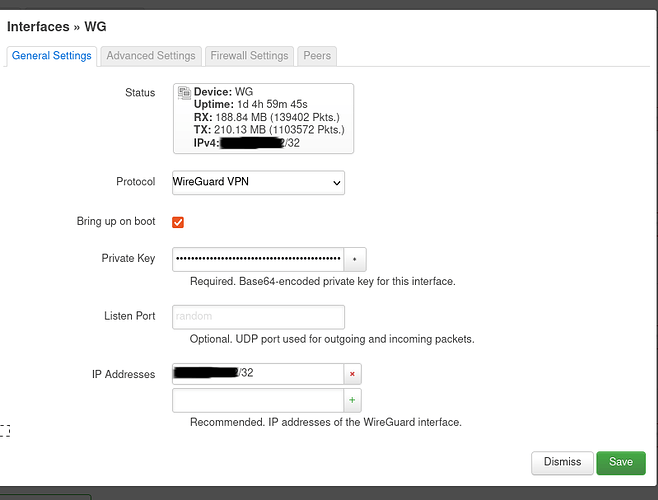
Network → Interfaces → Add new interface…
I write the name WARP
Protocol WireGuard VPN
Create interface
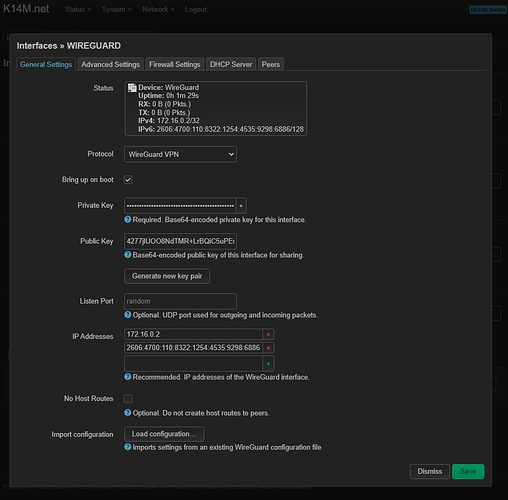
Next, Import configuration comes to the rescue with the “Load configuration…” button.
I drag the file there and see that all (?) settings have been successfully applied?
Checking...
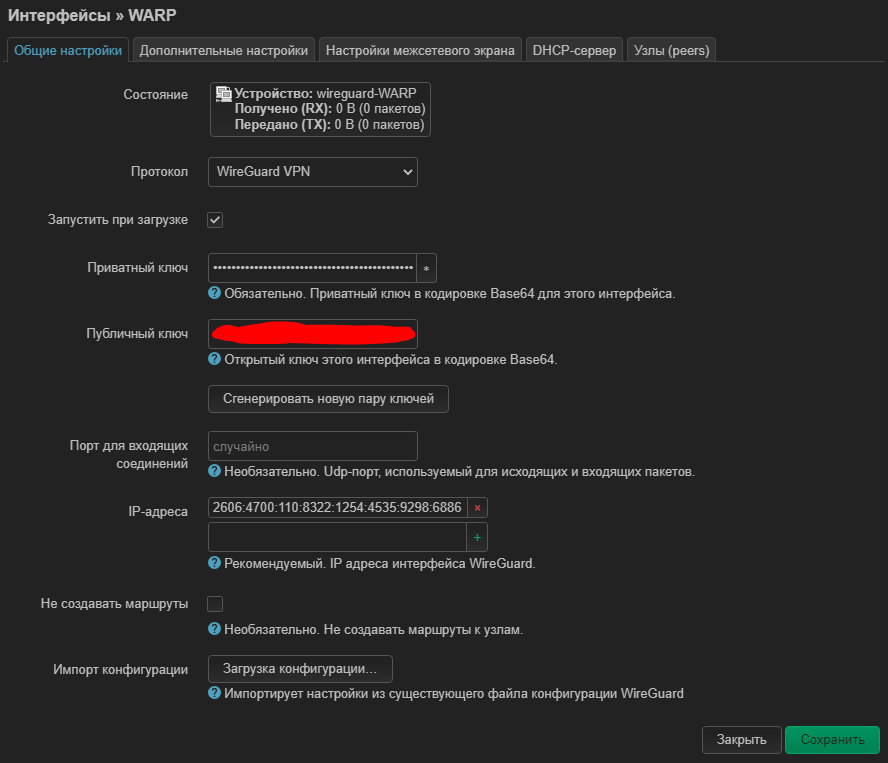
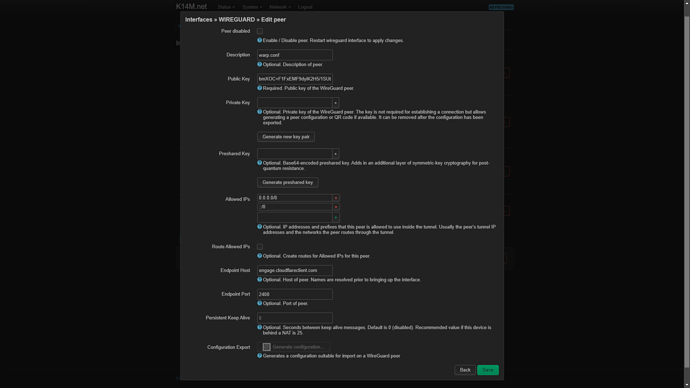
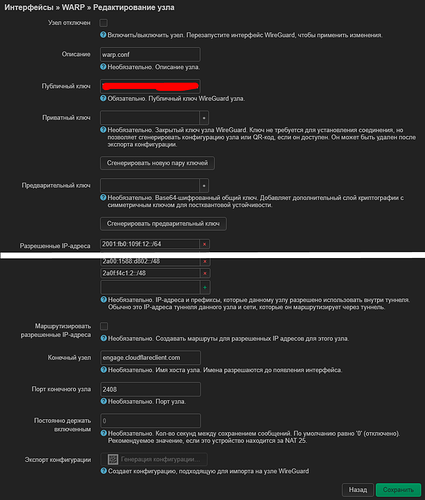
The private key was inserted from the line "[Interface] PrivateKey = "
Public key from "[Interface]# PublicKey = "
The port for incoming connections is empty, but it does not seem to be in the config either
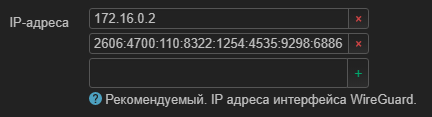
IP addresses inserted from “[Interface] Address = 2606:4700:110:8322:1254:4535:9298:6886”, that is, only v6? I don’t know if this is necessary, but manually and v4 I will add “Address = 172.16.0.2”
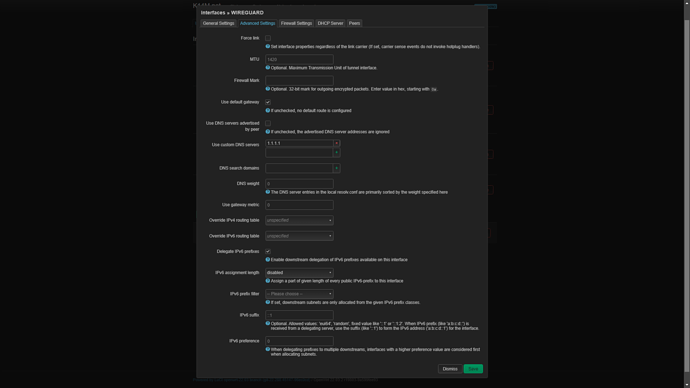
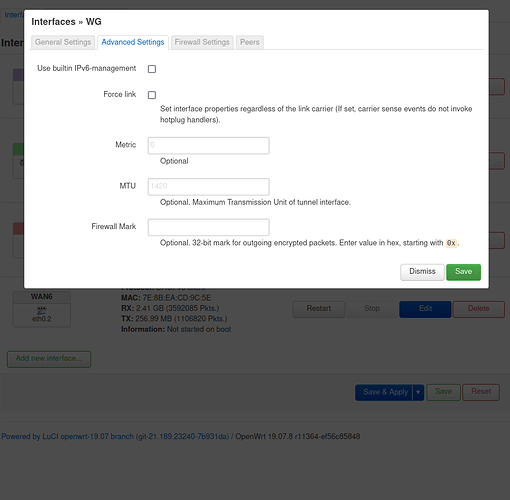
On the advanced settings tab
Use own DNS servers inserted from “[Interface] DNS = 1.1.1.1”
And everything seems to be here
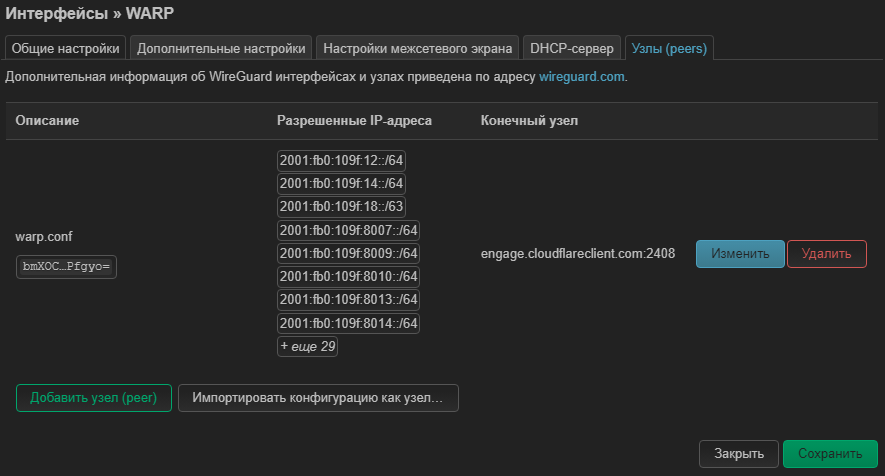
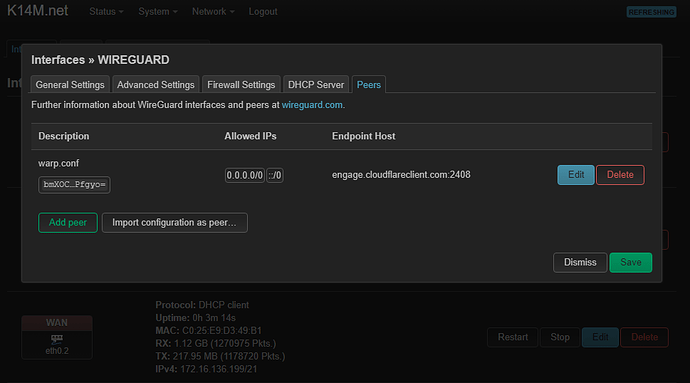
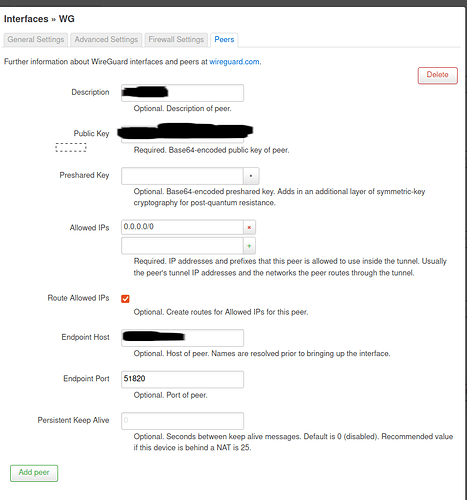
In the Peers tab
A new setting has been added, click "Change" to see what's inside:
Description of warp.conf, this is the name of the file that I uploaded
The public key was inserted from “[Peer] PublicKey =”
Allowed IP addresses, everything that I wrote in "[Peer] AllowedIPs = " was inserted here. But again, only v6
End node inserted from “[Peer] Endpoint = engage.cloudflareclient.com:2408” but only up to colon
End node port inserted from “[Peer] Endpoint = engage.cloudflareclient.com:2408” but only after the colon
And I didn't notice any changes.
A question has come up. Is the program accidentally or intentionally ignoring IP v4 addresses? Should I add them manually or not? And if so, should I paste them into the same file or create a new one?
Perhaps I will add them to the same file.
Apply all settings.
The instructions that I found also say to stop the WAN6 interface. This button is disabled for me. Perhaps the instruction is only for the config with IPv4, but I also have v6, which is why it doesn’t work. Xs…
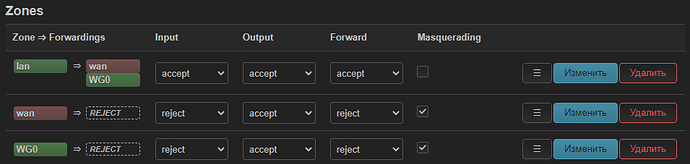
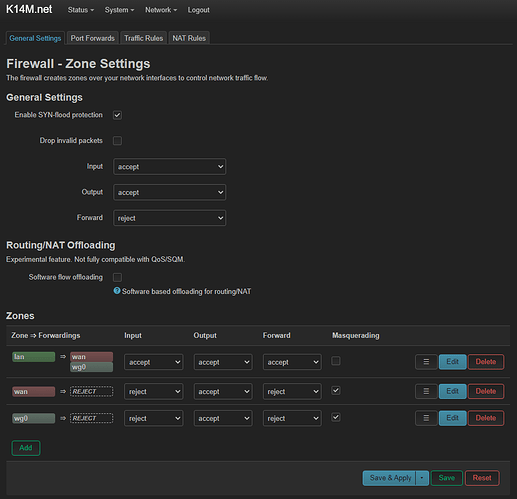
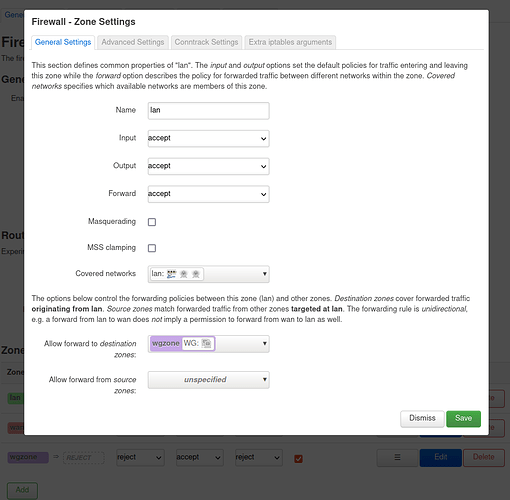
Now Network → Firewall → Add
Name well, for example WG0
input reject
output accept
forward rejection
Masquerading tick
MSS clamping tick
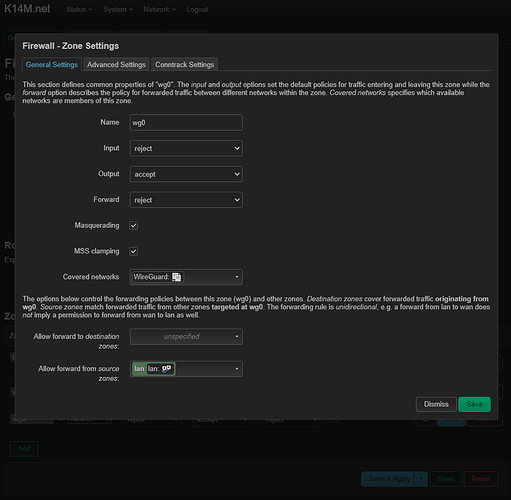
Covered networks is the same WARP interface that I created in the last step
Allow forward from source zones : lan
After saving it looks like this
Apply settings again
Back to interfaces
Network → Interfaces → WAN → Edit
In the Advanced settings tab, I uncheck the Use DNS servers declared by the host and enter my own from the config. Geez why. It seems that the same thing is written in the WARP interface, maybe you shouldn't do it again?
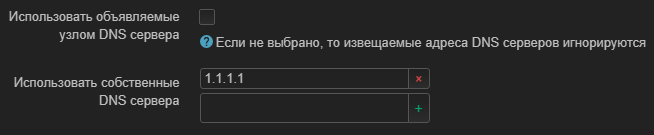
WAN6 was disabled in the instructions, but it works for me. So maybe I'll post it there...
Apply settings again
Further in the instructions there is an item Add Kill Switch (Optional), but since it is not required, I will not do it. Yes, and it is not clear what this is and why...
Restarting the router...
̶A̶n̶d̶ ̶I̶ ̶s̶u̶c̶c̶e̶s̶s̶f̶u̶l̶l̶y̶ ̶l̶o̶s̶t̶ ̶t̶h̶e̶ ̶I̶n̶t̶e̶r̶n̶e̶t̶
After some time, the Internet appeared. It looks like the settings take a long time to apply.
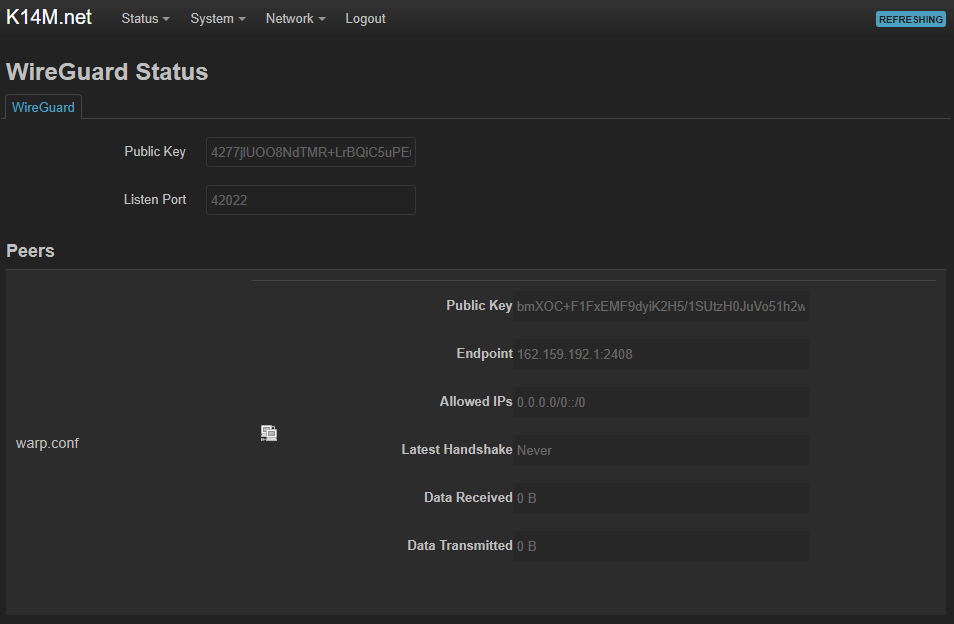
Now in the Status tab → WireGuard Status
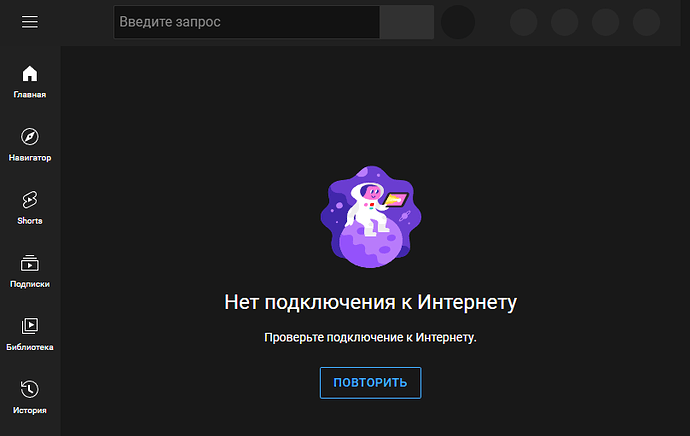
Which node is displayed. But how to check that everything works? I'm trying to access YouTube without any VPN and proxy...
Nothing comes out.
In one browser writes
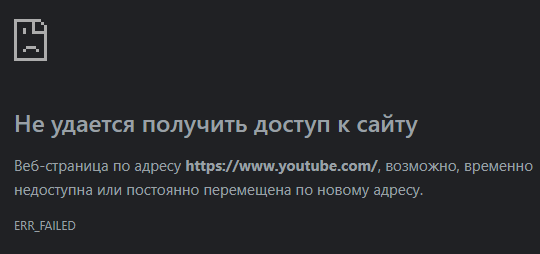
Writes something else in another
Output. Or maybe I've set it up wrong, which is quite possible. Or I indicated the wrong, or not all, YouTube IP addresses.
Is there any way to find out why nothing works for me?