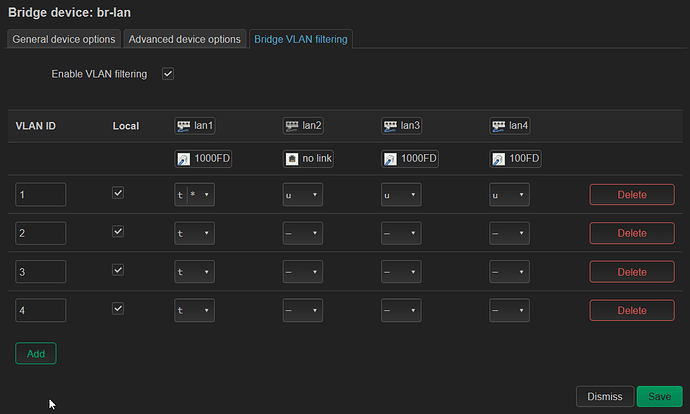
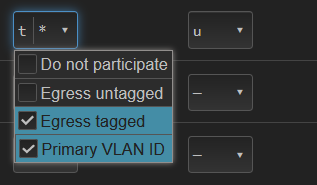
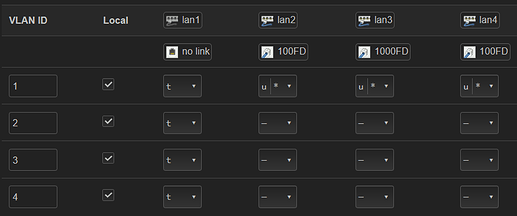
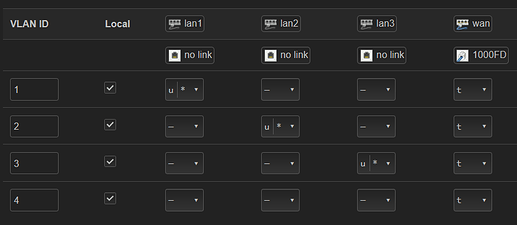
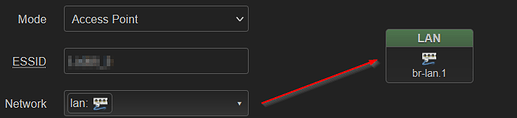
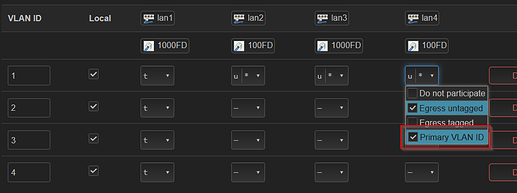
Was lan4, my bad.
MAC partially obfuscated
root@Router:~# tcpdump -i lan4 -evn -c 10
tcpdump: listening on lan4, link-type EN10MB (Ethernet), capture size 262144 bytes
16:00:52.741889 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 118: (tos 0x10, ttl 64, id 62461, offset 0, flags [DF], proto TCP (6), length 104)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x81ef (incorrect -> 0x071d), seq 3554015049:3554015113, ack 1405470178, win 1002, length 64
16:00:52.742005 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 182: (tos 0x10, ttl 64, id 62462, offset 0, flags [DF], proto TCP (6), length 168)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x822f (incorrect -> 0xf0d0), seq 64:192, ack 1, win 1002, length 128
16:00:52.742180 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 278: (tos 0x10, ttl 64, id 62463, offset 0, flags [DF], proto TCP (6), length 264)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x828f (incorrect -> 0x373a), seq 192:416, ack 1, win 1002, length 224
16:00:52.742313 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 262: (tos 0x10, ttl 64, id 62464, offset 0, flags [DF], proto TCP (6), length 248)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x827f (incorrect -> 0x612f), seq 416:624, ack 1, win 1002, length 208
16:00:52.742424 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 278: (tos 0x10, ttl 64, id 62465, offset 0, flags [DF], proto TCP (6), length 264)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x828f (incorrect -> 0x62ed), seq 624:848, ack 1, win 1002, length 224
16:00:52.742524 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 246: (tos 0x10, ttl 64, id 62466, offset 0, flags [DF], proto TCP (6), length 232)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x826f (incorrect -> 0x0250), seq 848:1040, ack 1, win 1002, length 192
16:00:52.742647 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 278: (tos 0x10, ttl 64, id 62467, offset 0, flags [DF], proto TCP (6), length 264)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x828f (incorrect -> 0x44ca), seq 1040:1264, ack 1, win 1002, length 224
16:00:52.742746 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 246: (tos 0x10, ttl 64, id 62468, offset 0, flags [DF], proto TCP (6), length 232)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x826f (incorrect -> 0x9974), seq 1264:1456, ack 1, win 1002, length 192
16:00:52.742854 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 278: (tos 0x10, ttl 64, id 62469, offset 0, flags [DF], proto TCP (6), length 264)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x828f (incorrect -> 0xfe3d), seq 1456:1680, ack 1, win 1002, length 224
16:00:52.742952 e8:9f:80:1c:xx:xx > 70:1c:e7:59:xx:xx, ethertype IPv4 (0x0800), length 246: (tos 0x10, ttl 64, id 62470, offset 0, flags [DF], proto TCP (6), length 232)
192.168.0.1.22 > 192.168.0.67.16251: Flags [P.], cksum 0x826f (incorrect -> 0xaa09), seq 1680:1872, ack 1, win 1002, length 192
10 packets captured
16 packets received by filter
0 packets dropped by kernel