Good morning everyone.
It's recently that I met OpenWRT.
I installed it on a Cudy WR1300 router.
It's a bit difficult to set up.
I'll explain my situation.
I would like to know if it is possible to configure the router as an access point connected by cable to the ISP router and then enable an OpenVPN tunnel usable by a PC in the LAN connected to one of the OpenWRT router ports.
I do not know if I was clear.
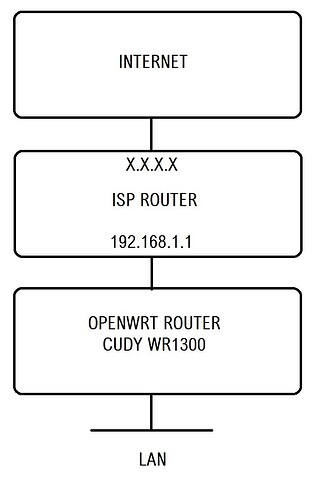
I attach topology.
If it were possible, how should I set it up?
Is it enough to assign the lan a static IP address of the ISP router's lan and then upload the .ovpn file to OpenWRT?
As for the firewall, do I have to disable it?
Thank you all in advance !!!!
Yes, it's possible, but it's not entirely ideal.
In order to get the computer to use tunnel, you have two options:
-
Set the computer's gateway address to the address of the OpenWrt device. This means configuring a static IP address on your computer, and this is usually not ideal.
-
Create a second subnet and SSID on your OpenWrt router. Then, connect your computer to that SSID when you want to use the VPN tunnel.
Hi
as i see on your picture
ISP ROUTER
192.168.1.1
and below is openwrt router
please note that default IP range for OpenWRT router is 192.168.1.1/24
so if you feed 192.168.1.x/24 on a WAN side it will not work because same 192.168.1.x/24 on LAN side
you need to move one of your router to different subnet, for ex 192.168.2.x/24
sorry, i read it again, you want simple AP with OVPN
Hi psherman
Thank a lot for your response.
So i like the second choice, the only thing is that the hardware that needs to use the tunnel is a Grandtsream phone and it doesn't have wifi.
It would be possible to configure one of the 4 ethernet ports that the router has (for example 4) and physically connect the phone to it, and make sure that all the traffic from that port ends up in the tunnel while the other users instead use the ISP's router to navigate etc. ?
If so, could you help me set it up?
Thanks in advance...
Sure...
Let's see the output of the following:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
wooooowwwww you are the fastest in the world !!
here they are :
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fd9f:9a0c:552a::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.3.70'
option gateway '192.168.3.1'
config device
option name 'tun0'
config interface 'OpenVPN'
option proto 'none'
option device 'tun0'
root@OpenWrt:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel '1'
option band '2g'
option htmode 'HT20'
option disabled '1'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option disabled '1'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option encryption 'none'
root@OpenWrt:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '8.8.8.8'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'OpenVPN'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Thanks
P.s. the ip address of ISP router is 192.168.3.1 lan side
Ok...
Start by removing lan4 from br-lan:
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
Then create a new network interface using lan4. (here, I'm calling it phone and giving it an address of 192.168.4.1/24
config interface 'phone'
option device 'lan4'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.4.1'
Add a DHCP server for this network:
config dhcp 'phone'
option interface 'phone'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
and create a new firewall zone that includes this new phone network.
config zone
option name 'phone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'phone'
Remove the openvpn network from your lan zone and create another one for the vpn, with masquerading enabled. I'm making an assumption that the VPN is not 100% trusted (insofar as other devices on the VPN network should have access to the router's administration interfaces), so I've changed it to input and forward as reject.
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'OpenVPN'
Finally, create a zone forwarding rule from phone > vpn.
config forwarding
option src 'phone'
option dest 'vpn'
Restart your router and plug a device into port lan4. You should get an address in the 192.168.4.0/24 subnet and it should have internet access via the VPN.
wooooowwwwww
works perfectly...
only two things:
-
my pc is 192.168.3.220 (dhcp from 192.168.3.1) how can i access phone interface on the 192.168.4.x lan ?
-
Which is your phisical address to send you something from my town ?


enable forwarding from lan > phone network.
config forwarding
option src 'lan'
option dest 'phone'
![]() . Not necessary at all. But thanks.
. Not necessary at all. But thanks.
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
Thanks! ![]()
enable forwarding from lan > phone network.
config forwarding
option src 'lan'
option dest 'phone'
Sorry but it doesn't works....
i can ping 192.168.4.2 from openwrt -> network -> diagnostic
but not from my pc
Oh, yeah... your main router doesn't know how to reach that network.
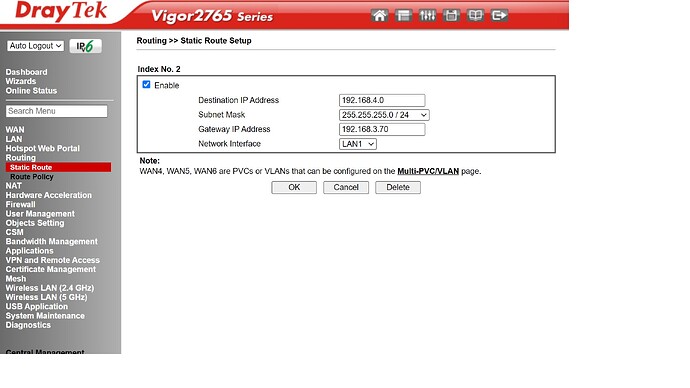
Does your main router have an option to specify static routes? If so, you need to add this:
192.168.4.0/24 via 192.168.3.70
added static route
ping from pc to phone
reply from 192.168.3.70 destination port not reachable
Before adding static route
Request timed out.
let's see the route as you've added it in the main router.
And let's review the firewall file from the OpenWrt side.
Also, keep in mind that some devices will not allow connections from a different subnet. The phone could potentially be in that category.
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'phone'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'phone'
option forward 'ACCEPT'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
list network 'OpenVPN'
config rule
option src 'phone'
option dest 'vpn'
option target 'ACCEPT'
config rule
option src 'lan'
option dest 'phone'
option target 'ACCEPT'
On the DrayTek device, what are the network interfae options in that dropdown?
in your firewall file, I'm not 100% certain it matters, but delete these rules and then add forwarding statements (below)
Add these:
config forwarding
option src 'phone'
option dest 'vpn'
config forwarding
option src 'lan'
option dest 'phone'
Options are
LAN1 LAN2 LAN3 LAN4 WAN1 WAN2 WAN3 WAN4 WAN5 WAN6
Sorry but how have i to do to add forwarding ?
I'm in Firewall->traffic rules. Is it correct ?
What physical port is used to connect to the OpenWrt device? Try using that one.
If you're using the LuCI web interface, edit the firewall zones. For example, edit the lan zone and then allow forward to destination phone zone.
Sorry i'm an idiot !!!!!
The phone reply web interface on port 9999 and i ask to port 80
It works perfectly !!!!
have patience !!!!
perfect! Glad it is working now!
Yes i'm going to switch topic as solved.
Thank again!!!
Have a good life !!! ![]()
![]()