Hi,
I want to refactor my home network. The following reason is to improve wiFi range in the house and improve the managment of some hosts I have locally.
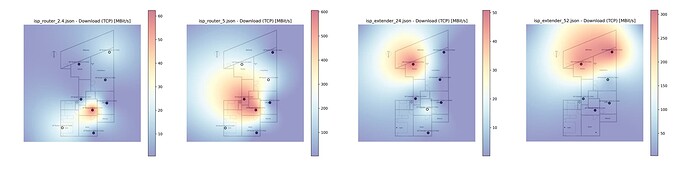
- About the WiFi I would like to improve the range and the roaming between APs. I have two APs: ISP Router and an AP sourced by the ISP. The problem is that there is no roaming between them so the clients only change between devices if the WiFi signal goes very low.
- About the network I would like to be able to set IPs for some devices (hosts and home automation devices). My current router doesn't support it. Right now I don't pretend to cretae VLANs.
- Improve the router firewall or at least have logs of incoming connections from unknow sources. Is it possible with OpenWrt, right?
- Move the reverse proxy from one of the Hosts to the router. I saw I can run docker containers on OpenWrt so it should be doable, right?
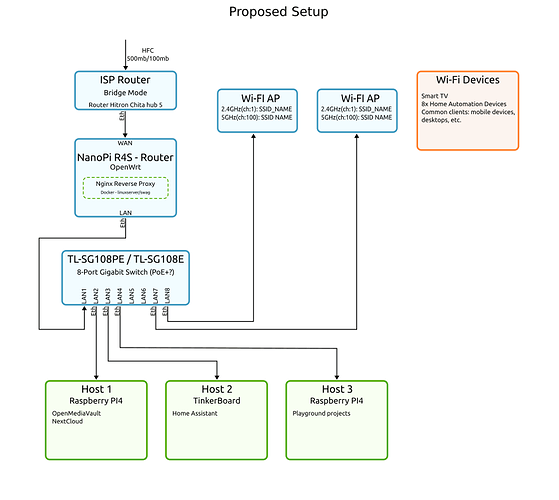
After some months reading about the topics I describe above I came up with the diagrams attached.
The main changes are to add a router after the ISP router with OpenWrt, add a switch and add two new APs.
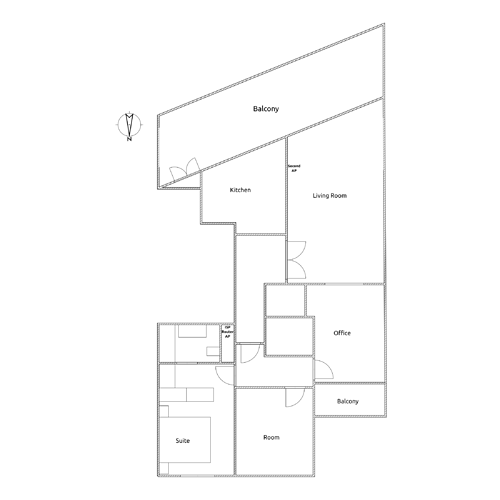
I would prefer to use the same place for the APs since they are hidden.
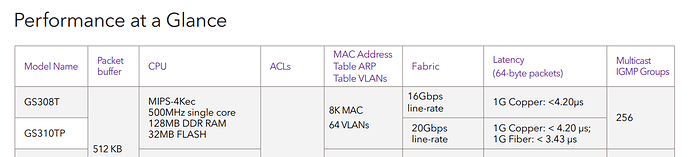
Do you think that is possible to add better APs on the same place of the current ones and get better range? It is ok to use two APs with OpenWrt or should I go with something like omada or a mesh kit? I dislike the omada solution because I need to have an extra controller for the roaming features. I saw that OpenWrt supports 802.11k, 802.11r and 802.11v.
Thank you