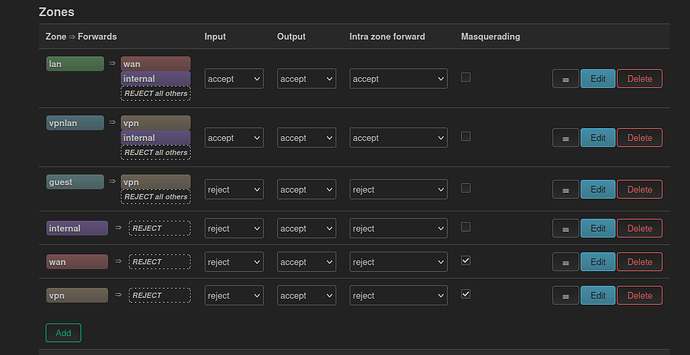
I'm finally reaching a point where my setup is "good enough". The last thing I want to figure out is how to cross firewall zones.
Here's overview of the setup:
There's also a rule for vpnlan that forces everything into vpn - I managed to set it up with help of the forum as well in this post.
config rule
option in 'vpnlan'
option lookup '102'
config route
option interface 'vpn'
option target '0.0.0.0/0'
option table '102'
What I want to do now is:
- Make
internalbecome reachable fromvpnlan- right now my rule makes it impossible. Does it even make sense to put thisforwardrule in the GUI if I have the rule to redirect it all tovpn? - Allow for
lan <=> vpnlancommunication - I want to be able to reach devices onvpnlanfromlan, and onlanfromvpnlan. Only locally so192.168.0.0/16restricted - I don't wantvpnlanto anyhow be able to go throughlantowan.
How can I do this? Do I have to define rules that are 192.168.0.0/16 specific? Maybe there's some way to do it using interfaces only, like: if it came from lan and is going to vpnlan - let it go?
/etc/config/network
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd95:f13:1605::/48'
option packet_steering '1'
config interface 'lan'
option device 'br-vlan.20'
option proto 'static'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option norelease '1'
option peerdns '0'
config interface 'vpn'
option proto 'wireguard'
option private_key 'openwrt='
list addresses '10.2.0.2/32'
option listen_port '51820'
list dns '10.2.0.1'
option mtu '1280'
config wireguard_vpn
option description 'WG'
option public_key 'openwrt='
list allowed_ips '0.0.0.0/0'
option endpoint_host '09.107.106.103'
option endpoint_port '51820'
option persistent_keepalive '25'
config rule
option in 'vpnlan'
option lookup '102'
config route
option interface 'vpn'
option target '0.0.0.0/0'
option table '102'
config interface 'vpnlan'
option proto 'static'
option ipaddr '192.168.12.1'
option netmask '255.255.255.0'
option defaultroute '0'
option device 'br-vlan.12'
config route
option interface 'vpn'
option target '10.2.0.1/24'
option table '110'
config rule
option in 'guest'
option lookup '102'
config rule
option dest '10.2.0.1/24'
option lookup '110'
option in 'loopback'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option device 'br-vlan.10'
option defaultroute '0'
config interface 'internal'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option device 'br-vlan.1'
option defaultroute '0'
config device
option type 'bridge'
option name 'br-vlan'
list ports 'eth0'
list ports 'eth2'
list ports 'eth3'
list ports 'eth4'
list ports 'eth5'
config bridge-vlan
option device 'br-vlan'
option vlan '1'
list ports 'eth2:u*'
list ports 'eth3:u*'
config bridge-vlan
option device 'br-vlan'
option vlan '10'
list ports 'eth2:t'
list ports 'eth3:t'
config bridge-vlan
option device 'br-vlan'
option vlan '20'
list ports 'eth0:u*'
list ports 'eth2:t'
list ports 'eth3:t'
list ports 'eth4:u*'
list ports 'eth5:u*'
config bridge-vlan
option device 'br-vlan'
option vlan '12'
list ports 'eth2:t'
list ports 'eth3:t'
/etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
option flow_offloading '1'
option flow_offloading_hw '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'vpnlan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vpnlan'
option family 'ipv4'
option mtu_fix '1'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config zone
option name 'internal'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'internal'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpn'
option family 'ipv4'
option mtu_fix '1'
option masq '1'
config forwarding
option src 'vpnlan'
option dest 'vpn'
config forwarding
option src 'guest'
option dest 'vpn'
config rule
option name 'Allow-Guest-DHCP-DNS'
option src 'guest'
option dest_port '53 67 68'
option target 'ACCEPT'
config rule
option name 'Allow-Internal-DHCP-DNS-NGINX'
option src 'internal'
option dest_port '53 67 68 80 443'
option target 'ACCEPT'
config rule
option name 'Allow-VPNLan-DHCP-DNS-NGINX'
option src 'vpnlan'
option dest_port '53 67 68 80 443'
option target 'ACCEPT'
config forwarding
option src 'lan'
option dest 'internal'
config forwarding
option src 'vpnlan'
option dest 'internal'
Thank you!