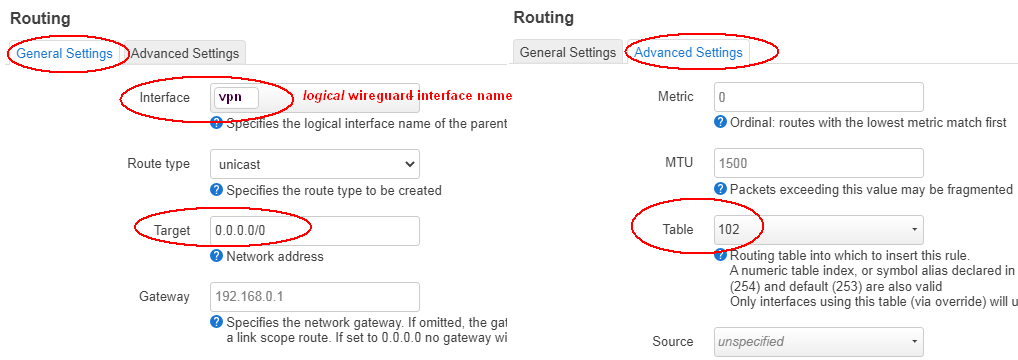
I'm absolutely new to this, sorry.
I have a router I got from my ISP and one of it's interfaces goes into my OpenWRT router as a WAN. My router has 6 ethernet ports and I want to utilize them. One goes to WAN, one to LAN and one to VPN connection - that's the plan.
I was pretty sure that my plan was quite simple to do. I wanted to have two networks:
lanusingwaninterfacevpn-lanusingvpninterface
This just won't work. It's either WAN or VPN picking all the traffic. If VPN picks up the traffic, vpn-lan has no connection to the internet and if VPN picks it up - there's no connection to the internet on lan. I have no idea what's happening.
I've seen some people just linking the PBR thing - I don't know what it is honestly. I got it, saw the config having 123890123 toggles and I decided to post a question here instead.
Here's what I've got going on:
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb9:398a:5b78::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
option ipv6 '0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option gateway '192.168.0.170'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '10.2.0.1'
option metric '20'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config interface 'guest'
option proto 'static'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
option device 'vlan-guest'
config interface 'internal'
option proto 'static'
option device 'vlan-internal'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
config interface 'vpnlan'
option proto 'static'
option device 'br-vpn'
option ipaddr '192.168.60.1'
option netmask '255.255.255.0'
option gateway '10.2.0.1'
config device
option type 'bridge'
option name 'br-vpn'
list ports 'eth2'
option ipv6 '0'
config interface 'vpn'
option proto 'wireguard'
option private_key '2IsIDUOUGlzPjN8V3tHBu/RISsi8yH/CvqXKumb4/2k='
list addresses '10.2.0.2/32'
list dns '10.2.0.1'
option force_link '1'
option mtu '1392'
option metric '10'
config wireguard_vpn
option description 'Proton PL#100'
option public_key 'wpfRQRhJirL++QclFH6SDhc+TuJJB4UxbCABy7A1tS4='
option route_allowed_ips '1'
option endpoint_host '79.127.186.193'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.2.0.2/32'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option force '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'internal'
option interface 'internal'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'vpnlan'
option interface 'vpnlan'
option start '100'
option limit '150'
option leasetime '12h'
option force '1'
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
option family 'ipv4'
config zone
option name 'vpnlan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vpnlan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'wan'
list network 'wan6'
option mtu_fix '1'
option masq6 '1'
option masq '1'
option family 'ipv4'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'vpn'
config zone
option name 'internal'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'internal'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config rule
option name 'Allow-Guest-DHCP-DNS'
option src 'guest'
option dest_port '53 67 68'
option target 'ACCEPT'
config rule
option name 'Allow-WireGuard-DHCP-DNS'
option src 'vpnlan'
option dest_port '53 67 68'
option target 'ACCEPT'
config forwarding
option src 'vpnlan'
option dest 'vpn'
config rule
option name 'Allow-WireGuard-Inbound'
option src 'vpnlan'
option dest_port '51820'
option target 'ACCEPT'
list proto 'tcp'
list proto 'udp'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'