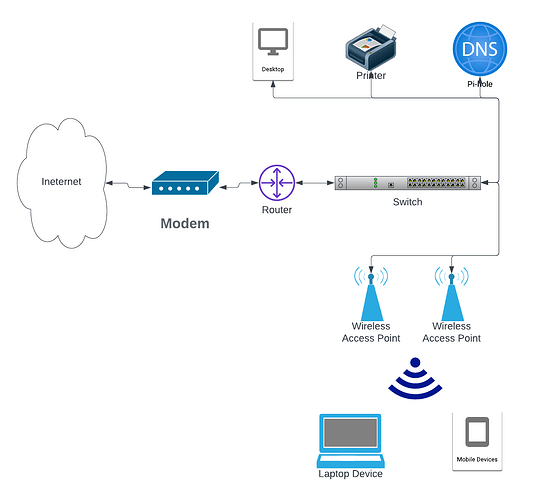
Thank you for all your response.
Several posts are already suggestions for solutions.
I'm sure those will be very helpful once I've defined the problem well so I'll try to finish that first.
I'll write up a new draft of the problem statement but I had some questions about your proposed rewrite. I'll just add them as inline questions.
Starting points
Internet connection: 1 Gbps
Did you pull out the rest of the info because bandwidth is the only relevant factor?
number of Wired devices: ...
What's the best way to describe this given that it's not a static number? I could list the devices that people in my family currently have. I could provide some estimates on the maximum number of concurrent devices over the past few months. I could guess at the maximum we might need in the near to mid-term.
Is it enough to guess that the order of magnitude is around 10 (ie support for just 5 is probably not enough, support for 20 is probably overkill)?
budget: up to $1000 (?)
I don't have a fixed budget. I want to primarily focus on defining the requirements. If I can get the platonic ideal of home networks for $1100 I won't complain but, by the same token, I wouldn't be happy with a $900 home network that is missing key functionality.
Generic requirements
For this section as a whole, I love that you provided objectively measurable factors for all of them)
wide userbase (=> statistics via https://sysupgrade.openwrt.org/stats/d/LM1HE4E7k/attended-sysupgrade-server?orgId=1)
Yes. That seems like a great way to define "wide user base". Do I understand correctly that you're suggesting some (fixed or percentage) threshold of "builds by target" as the metric?
proven reliability (=> choose device that is supported since 22.03 or before and look for user experiences)
"time since supported" is a good metric. If possible it would be nice to have a metric of how well it was supported (eg trend of bug reports, mean time to resolution)
maximum throughput (=> choose device that handles 802.11ax on 2.4GHz and 5Ghz)
Between this and PS3 it seems like the relevant question here would be "What is the range of planned/current wifi devices (eg 802.11c - 802.11ax)?
future proof upgrades (=> choose device with minimal 16MB flash / 128MB RAM)
"future proof" is a tricky requirement to define. Are there actually any reasonably future scenarios I could describe that would yield a different recommendation? If not maybe "future proof" isn't a good requirement at all and >16MB flash / 128MB RAM should just be the minimum recommended memory?
I notice you pulled out the section on latency. Is that not a relevant question? I could imagine that some effects are just fixed; ie adding a device will in the path will always increase latency. I've read cases where design choices or misconfigurations resulted in unnecessarily high latencies. Keeping that in check is relevant to me.
Wireless coverage (to determine amount of Access Points)
number of floors: 3
area/#rooms per floor? concrete/brick walls?
strategic positioning of Access Points possible? (=> https://arstechnica.com/gadgets/2020/02/the-ars-technica-semi-scientific-guide-to-wi-fi-access-point-placement/)
outside coverage needed?
That Arstechnica article reinforces what I knew about signal strength; it's complicated. I don't have a device that measures signal attenuation directly but I have "Wi-Fi Sweetspots". It shows more confusion. The room right next to the AP gets a weaker signal and than the next room farther away gets. The house is almost 100 years old and I don't really know what's in the walls. At least 2 generations of wiring, water and steam plumbing, some lath and plaster. There's also weird stuff; like a wall with windows facing nothing, just the interior of the wall.
Is the most practical approach to wireless coverage just to try it out and, if it's not enough, commit to adding more wired APs until it is?
Additional Router services (the more you need, the more cpu/memory is needed)
Network isolation / Guest Wifi
Maybe? I'm not sure. My main motivation for having Guest Wifi is that
a) Guests can easily sing up to our network
b) Organization and tracking
I'm less concerned about network isolation for QoS or Security. I should have enough bandwidth that guests can happily stream videos without causing a problem and I'm not worried about house guests using up my Laserjet toner or DOSing my network drives.
Traffic shaping (=> ie. SQM)
Maybe? Is that actually a functional requirement? From reading into it the main point of SQM seems to be to reduce latency. So yes to reduced latency but I'm totally open to considering other ways to reduce latency.
Would you put parental controls in this category? Ideally I'd have time controls (ie off at bedtime) and tiered access control (ie free access to most sites, weekly or daily time limits on things likesocial media, complete blocks on sites that present a security threat)
Adblock / tracking protection (=> ie. Adblock-fast or Adblock-lean)
Yes. I want aggressive and configurable Ad and tracking protection. I'm comfortable using some combination of Pi-hole, filters and subscriptions to allow/deny lists
VPN (=> ie. WireGuard)
I don't think so. We can install VPNs on end devices as needed (either for work or for privacy). I don't have a need to have the whole house on VPN and I wouldn't want the additional latency.
Intrusion Detection/Prevention System (=> ie. CrowdSec)
Yes. Is it enough to say "yes" to an ID/PS? Or do I need to go into more detail about what I want?
We have a fairly simple setup at home. I haven't set up dynDNS yet (although maybe I should) so we haven't bothered to set up any services with externally available ports.
For IDS I'm mostly interested in comprehensive logging, both internal and external. I don't
ps1: standard features Firewall and Parental Control do not impact the choice of hardware.
Good to know. I'll leave that out of the final version.
ps2: SPAM protection refers to SPAM received per email? If so, this needs to be done by email provider / email client
I was using SPAM in the more general sense of "unwanted connections" (ads, trackers etc)
ps3: do you have actually have old wireless devices which require legacy 802.11b ?
See above.
Thank you for your efforts in helping me. And thank you to all the people who offered specific hardware recommendations. I'll use those as the starting points once the requirements are buttoned up and I'm ready to design the solution.
![]()