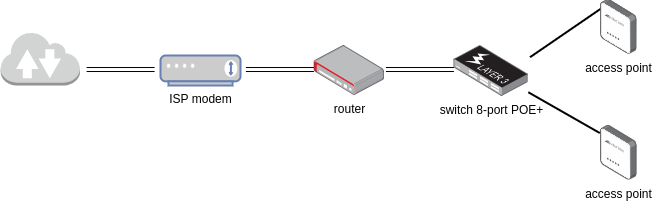
In OpenWrt 23.05 I created a basic VLAN setup from scratch using following Network devices
- router: RPi CM4 with DFRobot routerboard (no wifi)
- managed switch: Netgear SG308PE
- access point: TP-Link EAP615
This works ok as far as I can tell, but I have two questions:
Q1: is this a correct (described) way of setup?
Q2: finding out howto configure a VLAN setup took me some time by digging through documentation and forum posts. Possibly an example like mine deserves a wiki page under https://openwrt.org/docs/guide-user/network/vlan/start ?
(I will need to apply for a wiki account in that case)
Step 1: preparation
define networks that need to be isolated from each other with Network address and VLAN ids
192.168.10.0 VLAN id 10 main lan
192.168.20.0 VLAN id 20 guest
define IPs for device management
192.168.10.1 router
192.168.10.2 switch
192.168.10.3 access point
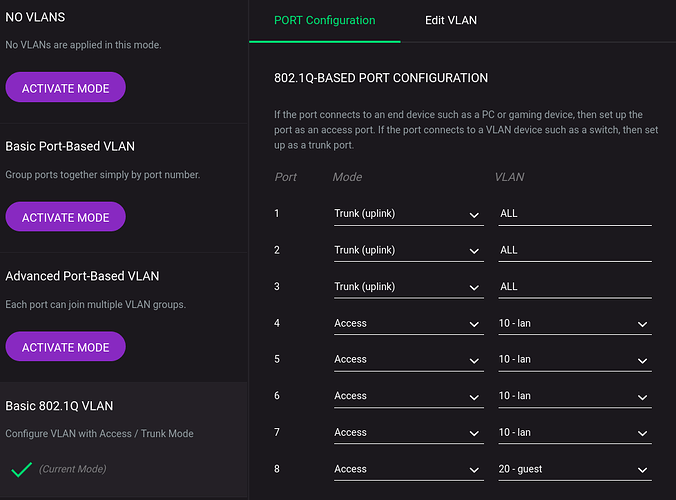
Step 2: configure switch
- configure static IP 192.168.10.2
- enable 802.1Q VLAN
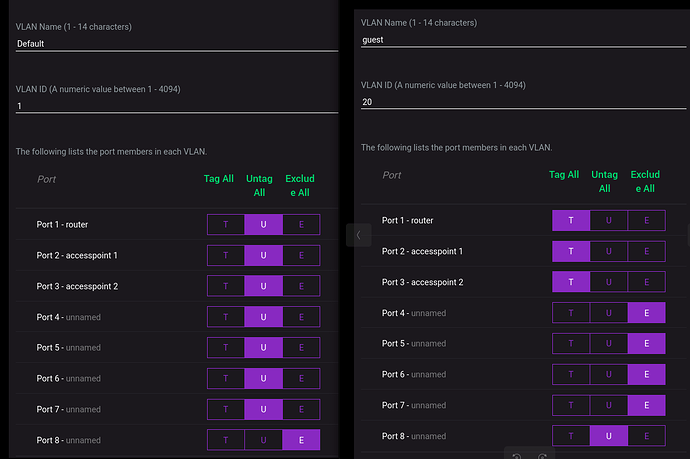
- setup VLAN ids 10 and 20
- set trunk ports for router and access points, ie port 1 -3
- set access ports for PC's and peripherals, ie port 4-7 for VLAN id 10 and port 8 for VLAN id 20
Step 3: configure router
note: after a Network Address change disable/enable the wired connection on the device from where you are configuring OpenWrt (laptop/pc)
- connect router to an access port on the switch and connect to 192.168.1.1
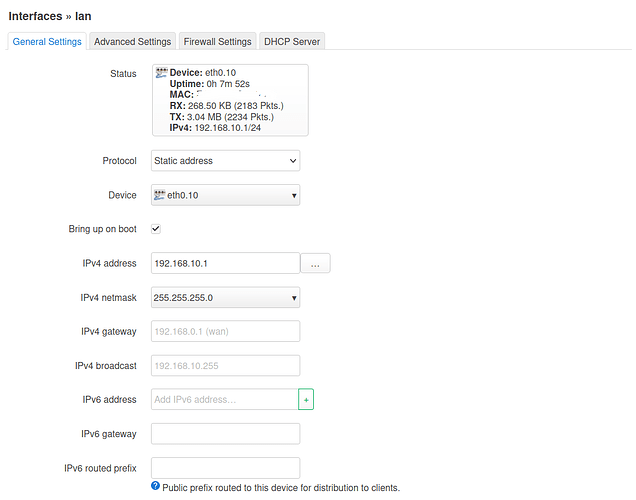
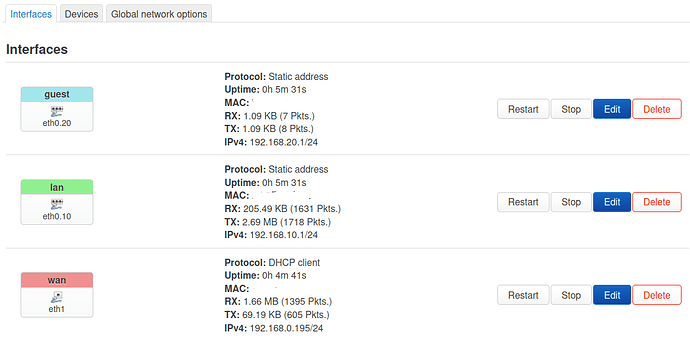
- in Network > Interfaces: edit lan interface and set device = eth0.10, protocol = Static, IPv4 = 192.168.10.1
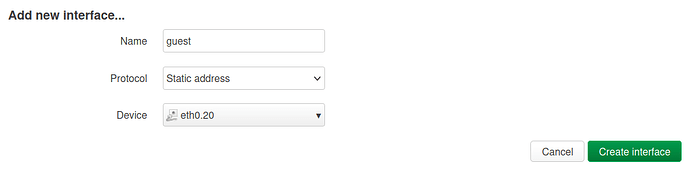
- in Network > Interfaces: add guest interface and set device = eth0.20, protocol = Static, IPv4 = 192.168.20.1; on DHCP server tab enable dhcp server
- in Network > Interfaces > Devices: click unconfigure br-lan (applicable when you have eth0 & eth1 only)
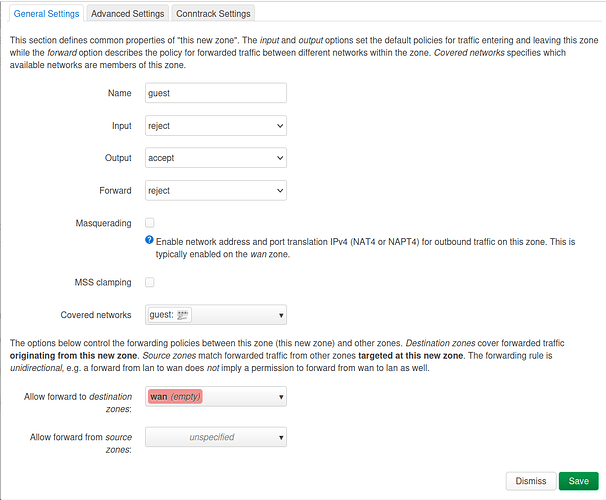
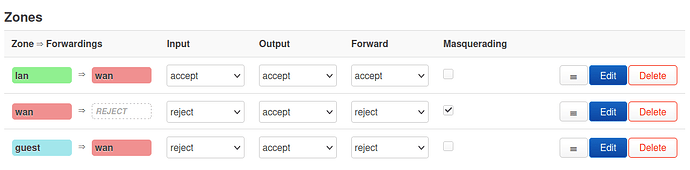
- in Network > Firewall > General: add guest zone
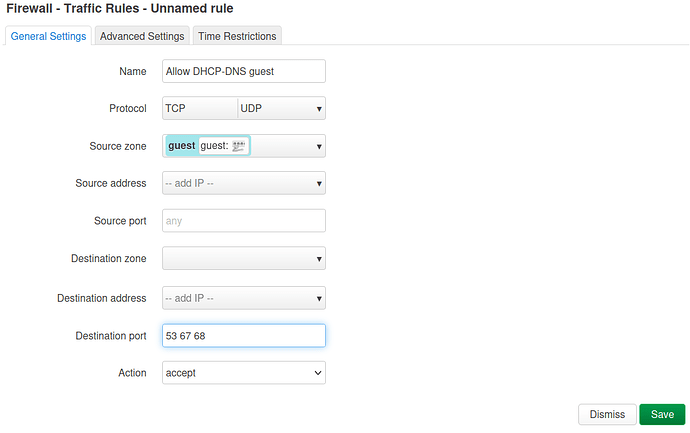
- in Network > Firewall > Traffic Rules: add DHCP-DNS guest rule
- Save & Apply (keep settings) and reboot router
- connect router to a trunk port on the switch and connect to 192.168.10.1 to verify if connection works.
Step 4: configure Access Points (AP)
note: lan0 is the backhaul port on this AP, this may be different on other devices.
- disconnect router from the switch
- connect AP to an access port on the switch and connect to 192.168.1.1
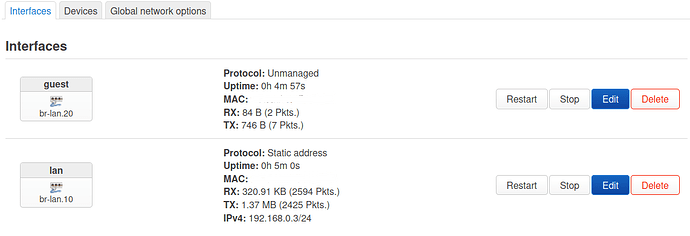
- in Network > Interfaces: edit lan interface and set device = br-lan.10, protocol = Static, IPv4 = 192.168.10.3 (protocol DHCP is possible as well - in that case the device will get an IP like 192.168.10.100); on DHCP server tab disable DHCP server
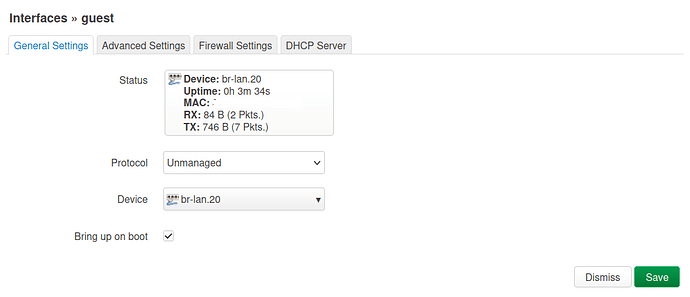
- in Network > Interfaces: add guest interface and set device = br-lan.20, protocol = None
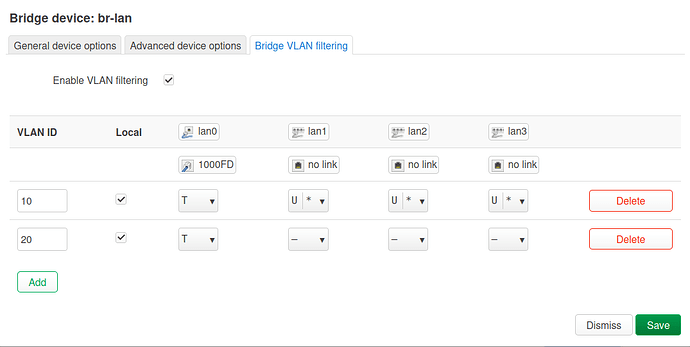
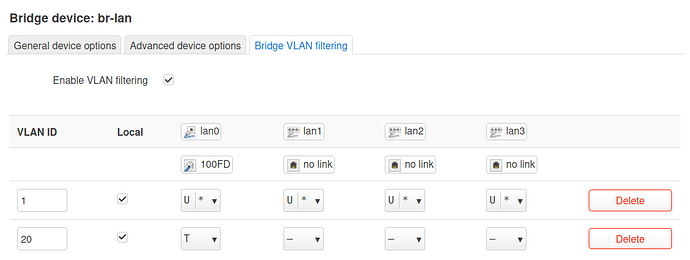
- in Network > Interfaces > Devices > br-lan > Configure > Bridge VLAN filtering: set trunk (tagged) and access (untagged) ports
- Save & Apply (keep settings) and reboot AP
- connect router to a trunk port on the switch
- connect AP to a trunk port on the switch and connect to 192.168.10.3
- in Network > Interfaces > lan > Firewall: set zone = Unspecified (optional)
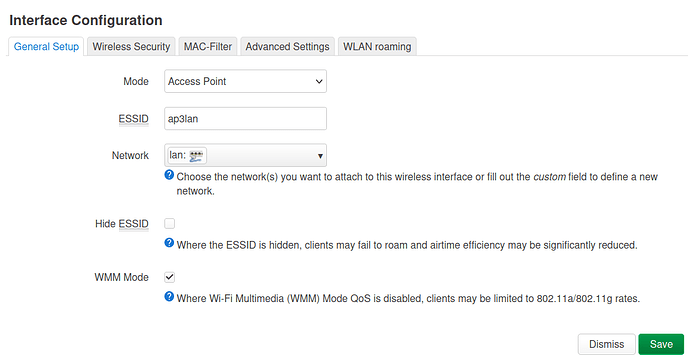
- in Network > Wireless configure one ssid with Network set to lan, and another ssid with Network set to guest
Resources
Config files
router /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '.........'
option packet_steering '1'
config interface 'lan'
option proto 'static'
option device 'eth0.10'
option ipaddr '192.168.10.1'
option netmask '255.255.255.0'
config interface 'guest'
option proto 'static'
option device 'eth0.20'
option ipaddr '192.168.20.1'
option netmask '255.255.255.0'
config interface 'wan'
option proto 'dhcp'
option device 'eth1'
router /etc/config/dhcp addition
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
router /etc/config/firewall addition
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding
option src 'guest'
option dest 'wan'
config rule
option name 'Allow DHCP-DNS guest'
option src 'guest'
option dest_port '53 67 68'
option target 'ACCEPT'
AP /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix '.........'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan0'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config bridge-vlan
option device 'br-lan'
option vlan '10'
list ports 'lan0:t'
list ports 'lan1:u*'
list ports 'lan2:u*'
list ports 'lan3:u*'
# list ports 'lan3:t' in case you want to pass VLAN traffic to an additional PoE powered AP
config bridge-vlan
option device 'br-lan'
option vlan '20'
list ports 'lan0:t'
config interface 'lan'
option proto 'static'
option device 'br-lan.10'
option ipaddr '192.168.10.3'
option netmask '255.255.255.0'
option gateway '192.168.10.1'
config interface 'guest'
option proto 'none'
option device 'br-lan.20'