Hi all, I tried following the tutorial posted here (Basic VLAN setup for router / managed switch / access point), but in the end when trying to connect to the SSIDs, there is no IP issued by DHCP on the main router. Planning on using VLAN 111 as an empty VLAN, 286 for LAN, 531 for Media, and 754 for IoT.
Port 1 is the router, Port 2 is the AP, and Port 4 is what my desktop is connected to on the switch.
I just reset the AP config before making this thread after the failed attempt so that's why there's nothing regarding VLANs on it.
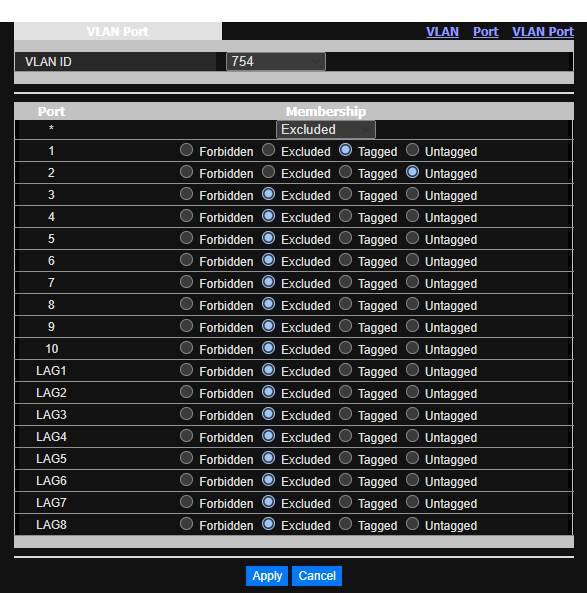
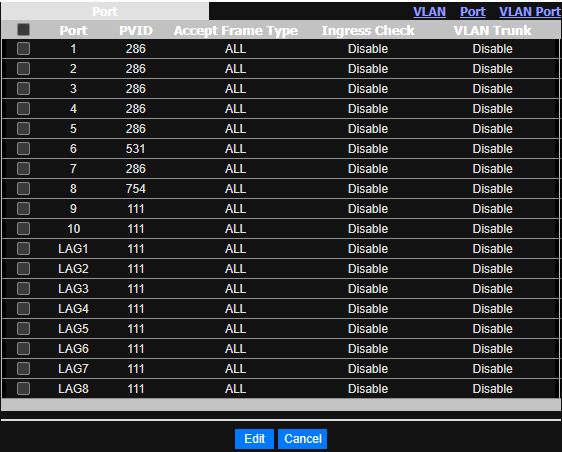
Switch setup
Router ubus call system board
"kernel": "5.15.150",
"hostname": "Lenovo",
"system": "Intel(R) Core(TM) i5-6500T CPU @ 2.50GHz",
"model": "LENOVO 10MUS17L00",
"board_name": "lenovo-10mus17l00",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "23.05.3",
"revision": "r23809-234f1a2efa",
"target": "x86/64",
"description": "OpenWrt 23.05.3 r23809-234f1a2efa"
Router network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdcc:38e1:a48e::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan.286'
option proto 'static'
option ipaddr '192.168.1.11'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
list dns '8.8.8.8'
list dns '9.9.9.9'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns 'xxxx:xxxx:xxxx::xxxx'
list dns 'xxxx:xx::xx'
config interface 'cjdns'
option device 'tuncjdns'
option proto 'none'
config bridge-vlan
option device 'br-lan'
option vlan '531'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '286'
list ports 'eth0:u*'
config bridge-vlan
option device 'br-lan'
option vlan '111'
option local '0'
list ports 'eth0:t'
config bridge-vlan
option device 'br-lan'
option vlan '754'
list ports 'eth0:t'
config interface 'IoT'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option device 'br-lan.754'
Router dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '0'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
option noresolv '0'
option port '54'
list server '192.168.1.11'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
list ra_flags 'managed-config'
list ra_flags 'other-config'
list dhcp_option '6,192.168.1.11'
list dhcp_option '3,192.168.1.11'
list dns 'fdcc:38e1:a48e::1'
list dns '2601:58a:8200:1df0::1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config host
option name 'GS1900'
option ip '192.168.1.156'
option mac 'xx:xx:xx:xx:xx:xx'
config dhcp 'IoT'
option interface 'IoT'
option start '100'
option limit '150'
option leasetime '12h'
Router firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'cjdns'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option conntrack '1'
option family 'ipv6'
list network 'cjdns'
config rule
option name 'Allow-ICMPv6-cjdns'
option src 'cjdns'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option enabled '0'
option name 'Allow-SSH-cjdns'
option src 'cjdns'
option proto 'tcp'
option dest_port '22'
option target 'ACCEPT'
config rule
option enabled '0'
option name 'Allow-HTTP-cjdns'
option src 'cjdns'
option proto 'tcp'
option dest_port '80'
option target 'ACCEPT'
config rule
option name 'Allow-cjdns-wan'
option src 'wan'
option proto 'udp'
option dest_port '12376'
option target 'ACCEPT'
config zone
option name 'IoT'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'IoT'
config forwarding
option src 'IoT'
option dest 'wan'
config rule
option name 'Allow-IoT-DNS'
option src 'IoT'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Allow-IoT-DHCP'
list proto 'udp'
option src 'IoT'
option dest_port '67 68'
option target 'ACCEPT'
AP ubus call system board
"kernel": "5.15.137",
"hostname": "AC1750v5",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C7 v5",
"board_name": "tplink,archer-c7-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ath79/generic",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
AP network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd26:7096:79af::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.12'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.11'
list dns '192.168.1.11'
config device
option name 'eth0.2'
option macaddr 'xx:xx:xx:xx:xx:xx'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
AP wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'pci0000:00/0000:00:00.0'
option channel '36'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'network'
option encryption 'psk2'
option key 'password'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/ahb/18100000.wmac'
option channel '1'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'network'
option encryption 'psk2'
option key 'password'