KOA
June 27, 2022, 7:41am
21
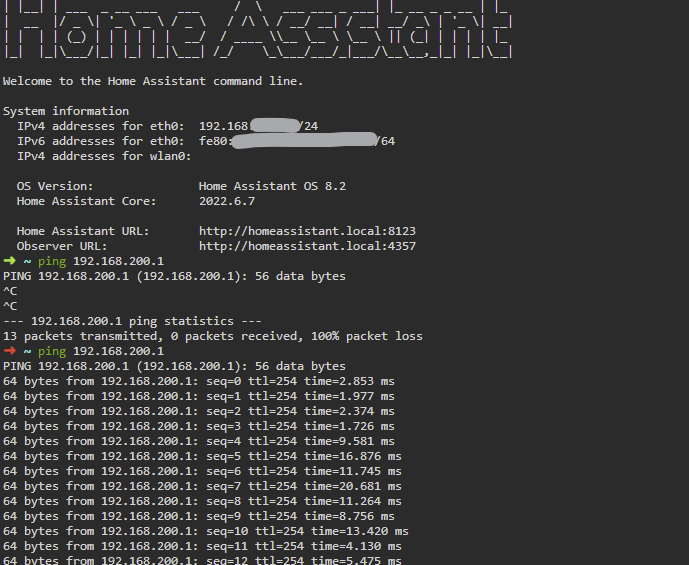
output for this command
root@OpenWrt:~# iptables-save -t nat -c
# Generated by iptables-save v1.8.7 on Mon Jun 27 12:40:16 2022
*nat
:PREROUTING ACCEPT [4382:797175]
:INPUT ACCEPT [52:6894]
:OUTPUT ACCEPT [1084:82382]
:POSTROUTING ACCEPT [1088:82686]
:ts-postrouting - [0:0]
[1088:82686] -A POSTROUTING -j ts-postrouting
[0:0] -A ts-postrouting -m mark --mark 0x40000 -j MASQUERADE
COMMIT
# Completed on Mon Jun 27 12:40:16 2022
Something is wrong here. All default chains are missing. Did you install iptables additionally?
ubus call system board; nft list chain inet fw4 forward
KOA
June 27, 2022, 7:52am
23
# Completed on Mon Jun 27 12:40:16 2022
root@OpenWrt:~# ubus call system board; nft list chain inet fw4 forward
{
"kernel": "5.4.188",
"hostname": "OpenWrt",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "Netgear WNDR4300 v2",
"board_name": "netgear,wndr4300-v2",
"release": {
"distribution": "OpenWrt",
"version": "21.02.3",
"revision": "r16554-1d4dea6d4f",
"target": "ath79/nand",
"description": "OpenWrt 21.02.3 r16554-1d4dea6d4f"
}
}
-ash: nft: not found
N I didn't install iptables. Only installed fping opkg.
/etc/init.d/firewall status; /etc/init.d/firewall restart; iptables-save -t nat -c
1 Like
KOA
June 27, 2022, 8:07am
25
root@OpenWrt:~# /etc/init.d/firewall status; /etc/init.d/firewall restart; iptables-save -t nat -c
inactive
Warning: Unable to locate ipset utility, disabling ipset support
Warning: Section @zone[1] (wan) cannot resolve device of network 'wwan'
* Flushing IPv4 filter table
* Flushing IPv4 nat table
* Flushing IPv4 mangle table
* Flushing IPv6 filter table
* Flushing IPv6 mangle table
* Flushing conntrack table ...
* Populating IPv4 filter table
* Rule 'Allow-DHCP-Renew'
* Rule 'Allow-Ping'
* Rule 'Allow-IGMP'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Redirect 'Pre route'
* Forward 'lan' -> 'wan'
* Forward 'lan' -> 'sun'
* Forward 'sun' -> 'lan'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv4 nat table
* Redirect 'Pre route'
* NAT 'Post route'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv4 mangle table
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv6 filter table
* Rule 'Allow-DHCPv6'
* Rule 'Allow-MLD'
* Rule 'Allow-ICMPv6-Input'
* Rule 'Allow-ICMPv6-Forward'
* Rule 'Allow-IPSec-ESP'
* Rule 'Allow-ISAKMP'
* Forward 'lan' -> 'wan'
* Forward 'lan' -> 'sun'
* Forward 'sun' -> 'lan'
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Populating IPv6 mangle table
* Zone 'lan'
* Zone 'wan'
* Zone 'sun'
* Flushing conntrack table ...
* Set tcp_ecn to off
* Set tcp_syncookies to on
* Set tcp_window_scaling to on
* Running script '/etc/firewall.user'
# Generated by iptables-save v1.8.7 on Mon Jun 27 13:05:50 2022
*nat
:PREROUTING ACCEPT [9:536]
:INPUT ACCEPT [3:176]
:OUTPUT ACCEPT [1:100]
:POSTROUTING ACCEPT [1:100]
:postrouting_lan_rule - [0:0]
:postrouting_rule - [0:0]
:postrouting_sun_rule - [0:0]
:postrouting_wan_rule - [0:0]
:prerouting_lan_rule - [0:0]
:prerouting_rule - [0:0]
:prerouting_sun_rule - [0:0]
:prerouting_wan_rule - [0:0]
:zone_lan_postrouting - [0:0]
:zone_lan_prerouting - [0:0]
:zone_sun_postrouting - [0:0]
:zone_sun_prerouting - [0:0]
:zone_wan_postrouting - [0:0]
:zone_wan_prerouting - [0:0]
[7:438] -A PREROUTING -m comment --comment "!fw3: Custom prerouting rule chain" -j prerouting_rule
[7:438] -A PREROUTING -i br-lan -m comment --comment "!fw3" -j zone_lan_prerouting
[0:0] -A PREROUTING -i eth0.2 -m comment --comment "!fw3" -j zone_wan_prerouting
[0:0] -A PREROUTING -i wlan0 -m comment --comment "!fw3" -j zone_sun_prerouting
[1:100] -A POSTROUTING -m comment --comment "!fw3: Custom postrouting rule chain" -j postrouting_rule
[1:100] -A POSTROUTING -o br-lan -m comment --comment "!fw3" -j zone_lan_postrouting
[0:0] -A POSTROUTING -o eth0.2 -m comment --comment "!fw3" -j zone_wan_postrouting
[0:0] -A POSTROUTING -o wlan0 -m comment --comment "!fw3" -j zone_sun_postrouting
[1:100] -A zone_lan_postrouting -m comment --comment "!fw3: Custom lan postrouting rule chain" -j postrouting_lan_rule
[7:438] -A zone_lan_prerouting -m comment --comment "!fw3: Custom lan prerouting rule chain" -j prerouting_lan_rule
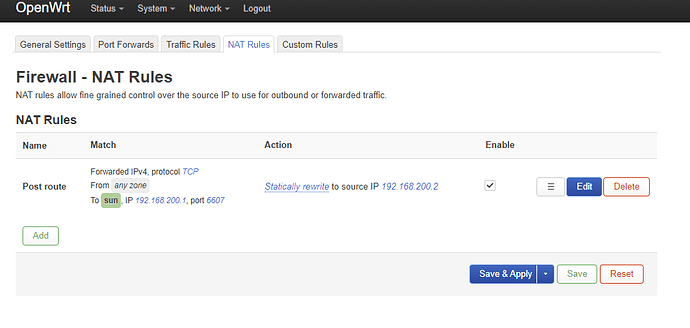
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Pre route" -j DNAT --to-destination 192.168.200.1:6607
[0:0] -A zone_sun_postrouting -m comment --comment "!fw3: Custom sun postrouting rule chain" -j postrouting_sun_rule
[0:0] -A zone_sun_postrouting -d 192.168.200.1/32 -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Post route" -j SNAT --to-source 192.168.200.2
[0:0] -A zone_sun_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_sun_prerouting -m comment --comment "!fw3: Custom sun prerouting rule chain" -j prerouting_sun_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3: Custom wan postrouting rule chain" -j postrouting_wan_rule
[0:0] -A zone_wan_postrouting -m comment --comment "!fw3" -j MASQUERADE
[0:0] -A zone_wan_prerouting -m comment --comment "!fw3: Custom wan prerouting rule chain" -j prerouting_wan_rule
COMMIT
# Completed on Mon Jun 27 13:05:50 2022
You must activate the firewall service permanently.
/etc/init.d/firewall enable
The port forwarding rule is correct
[0:0] -A zone_lan_prerouting -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Pre route" -j DNAT --to-destination 192.168.200.1:6607
The second rule is redundant. The masquerading on the sun zone is enabled so it should work without the SNAT rule, which in this case takes precedence.
[0:0] -A zone_sun_postrouting -d 192.168.200.1/32 -p tcp -m tcp --dport 6607 -m comment --comment "!fw3: Post route" -j SNAT --to-source 192.168.200.2
[0:0] -A zone_sun_postrouting -m comment --comment "!fw3" -j MASQUERADE
Try to access the inverter. If it doesn't work, post again
iptables -t nat -nvL zone_lan_prerouting; iptables -t nat -nvL zone_sun_postrouting
to check the rules for hits.
2 Likes
KOA
June 27, 2022, 8:33am
27
root@OpenWrt:~# /etc/init.d/firewall enable
root@OpenWrt:~#
root@OpenWrt:~#
done, enabled firewall using the command. All parameters seems to be working.
should I delete the second rule?
Leave it that way, it is not a problem, but restart the router to make sure that the firewall starts.
KOA
June 27, 2022, 8:44am
29
rebooted how to check firewall is up and running?
/etc/init.d/firewall status
1 Like
KOA
June 27, 2022, 8:46am
31
root@OpenWrt:~# /etc/init.d/firewall status
active with no instances
root@OpenWrt:~#
KOA
June 27, 2022, 8:54am
33
Thanks for the help. It is working fine I think
1 Like
KOA
June 27, 2022, 8:59am
34
The only thing is how to summarize all this for an alternative Openwrt method (instead of using dd-wrt, bcz forum support is best on both Openwrt and Fresh tomato, which I as previously using.) , to solve this thread.
I would omit the SNAT rule. Masquerading does not depend on the router IP address (which may change) and allows you to ping the device.
EDIT:
BTW, when masquerading is enabled, you should be able to access the device directly by its IP address (192.168.200.1) without port forwarding on the router lan interface.
1 Like
KOA
June 27, 2022, 11:51am
36
pavelgl:
192.168.200.1
inverter at 192.168.200.1 doesn't have any web interface or something fancy. I can try connecting sun2000 app, which requires direct connection to the inverter's AP.https://support.huawei.com/enterprise/en/doc/EDOC1100096889?section=j00b
https://support.huawei.com/enterprise/en/doc/EDOC1100141536/54364b7/downloading-and-installing-the-app
KOA
July 6, 2022, 11:26am
38
How can we change these rules for the next version of OpenWrt i.e 22.03, which changes over to nfttables ?
OK, installing the latest upgrade (rc4) solved it. Now firewall is started at startup, BUT Network → Firewall does not have the Custom rules -tab anymore!!! So, where and how i put these, becaude the HA integration does not work without: iptables...
If you create the rules using LuCI, you do not need to change anything.
If you insist on custom rules, they must be created in /etc/nftables.d/.
1 Like
KOA
July 6, 2022, 12:01pm
40
No, I am not insisting on custom rules, I recommended the same setting i.e from LUCI and it seems to be working.
1 Like
KOA
July 13, 2022, 3:54pm
41
I summarized all the steps in this thread. any issues to be fixed in that?
So to summarize, I did this. Note Huawei inverter is on another subnet that is 192.168.200.0.
[image]
Flash Openwrt on the router
Setup your router as a dumb AP. https://openwrt.org/docs/guide-user/network/wifi/dumbap
Connect it to your ISP router via ethernet. This will change the IP to something in the router’s subnet range. e.g if your ISP’s router Ip is 192.168.1.1 then your OpenWrt's router IP will be 192.168.1.24 (anything in between 192.168.1.2 to 192.168.1.100)
Connect to your Huwae…