Is this the correct way to add iptables rules using "Network --- Firewall - Custom Rules"
Generally speaking, yes. However these rules can be implemented on the regular port forwarding and masquerading rules and not as custom rules.
how to do that?
I wanted to connect my Solar inverter with my network using Openwrt router, without using CLI. Connect to Huwaei SUN2000 inverter using fiber modem - #22 by KOA
this GitHub did mention some rules but I just used Winscp to edit the relevant files.
My plan was to make this configuration as noob-friendly as possible and make easy to follow Youtube video about it.
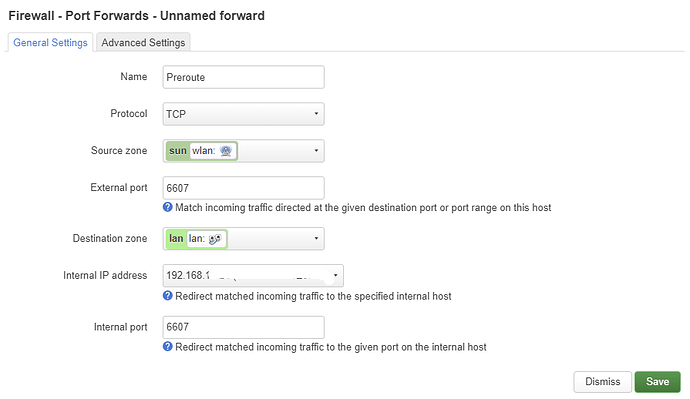
Browse to Network > Firewall > Port Forward.
(You literally browsed past this page to Custom Rules - then asked how, so it's difficult to understand why you skipped it then typed a iptables rule manually. I surmise you had this rule from somewhere else.)
- Since you insist on the web GUI, the rule as noted in
/etc/config/firewallmay not help, but will display on the GUI if you add it properly - Also, what is 192.168.200.1, is this another router?
- I saw the other post, unless I missed, it doesn't say
See:
I followed this post.
which is written by the author of this blog.
https://skyboo.net/2021/07/how-to-connect-to-sun2000-from-dd-wrt/
I just copy-pasted the rules, adjusting them according to my network.
192.168.200.1 is the Ip of the Huwaei solar inverter, which can only be connected to in client mode i.e it will act as short-range router only.
Insistence on GUI only, is only to make it "noob-friendly" process.
edit: Is this the correct way to add first rule/portfoward with internal Ip being Ip address of the router?
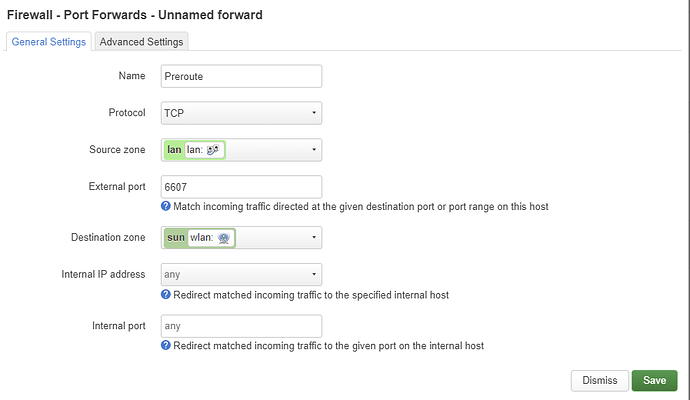
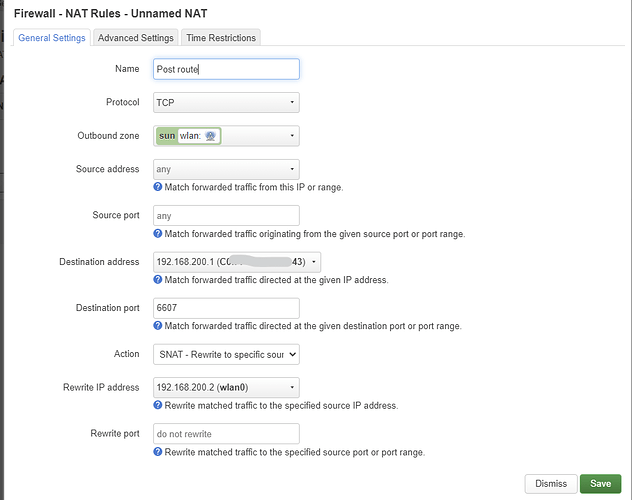
Swap the source and destination zones. The internal IP address must be 192.168.200.1.
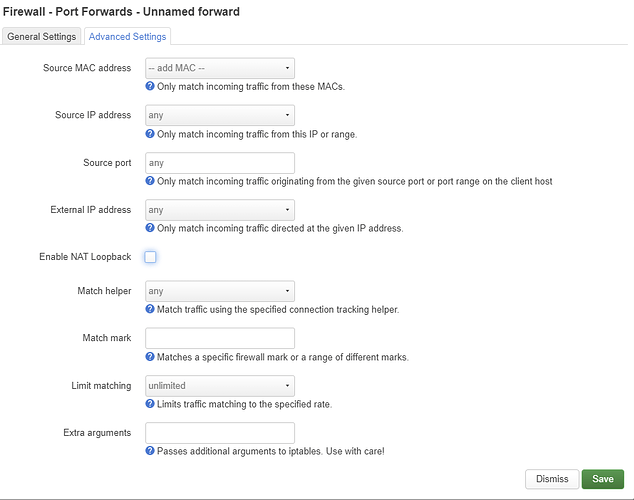
It is not necessary, but if you insist on specifying the IP address of the router, go to Advanced Settings and set it as the external IP address.
Check the rule running
iptables -t nat -nvL zone_lan_prerouting
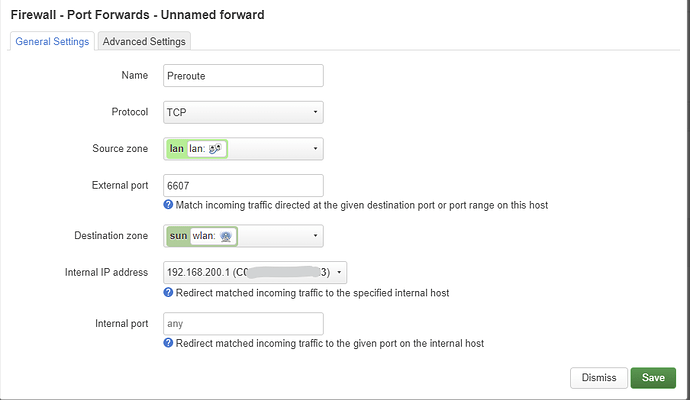
is this correct for the first rule now?
will the second rule will be required or not? https://openwrt.org/docs/guide-user/network/routedclient#using_masquerade
The internal IP address is missing.
EDIT:
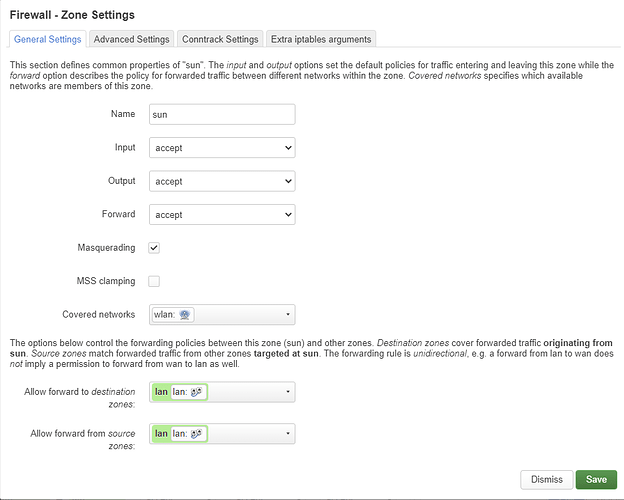
Disable NAT Loopback in the first rule and enable MASQUERADING on the sun zone.
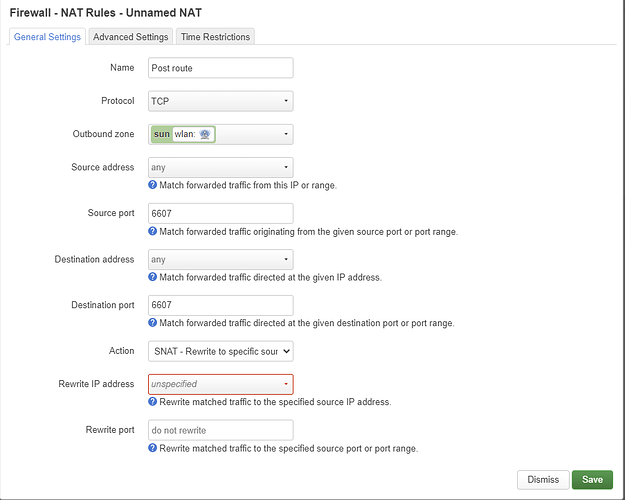
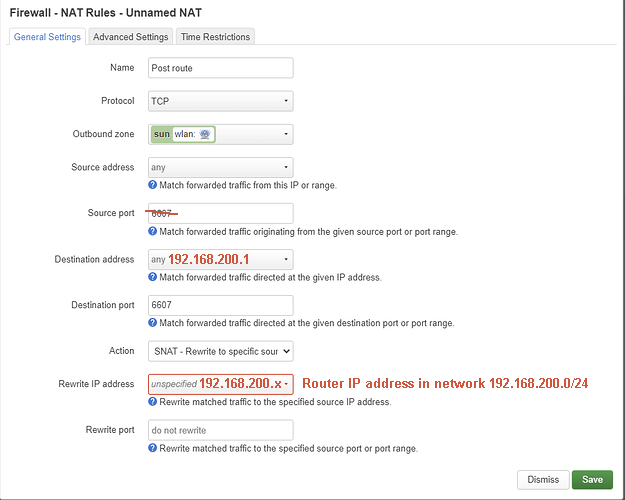
I think it would be better with a SNAT rule.
how to do that?
Is this correct?
and for second rules, if we follow SNAT
and in case of MASQUERADING
I am doing it write or anything wrong?
If I understood the situation correctly, the router is connected to the inverter as a DHCP client via a wireless connection in sta mode.
The router's IP address may change and the SNAT rule will need to be updated.
I don't think it's worth the effort, especially if the inverter is the only one device in the "sun" zone/network and the benefits of SNATing (or more precise masquerading) are questionable...
OpenWRT router is the only device connected to the inverter and vice versa is true. The inverter only allows one connection at a time.
For the second rule with SNAT.
or should I follow masquerading?
and for the first rule
and NAT loopback disabled for the first rule.
You can use the SNAT rule. The rest seems to be correct, but to be sure please SSH into the router and post the output of the following commands:
iptables -t nat -nvL zone_lan_prerouting; iptables -t nat -nvL zone_sun_postrouting
I assume you used lowercase letters for the name of the "sun" zone. If not, update the second command accordingly.
output
root@OpenWrt:~# iptables -t nat -nvL zone_lan_prerouting; iptables -t nat -nvL zone_sun_postrouting
iptables: No chain/target/match by that name.
iptables: No chain/target/match by that name.
edit:
sun zone is small case
iptables-save -c nat
Redact only the public IPs (if any)
strange
root@OpenWrt:~# iptables-save -c nat
Unknown arguments found on commandline
root@OpenWrt:~# iptables-save -c nat
Unknown arguments found on commandline
root@OpenWrt:~#
Sorry, typo
iptables-save -t nat -c