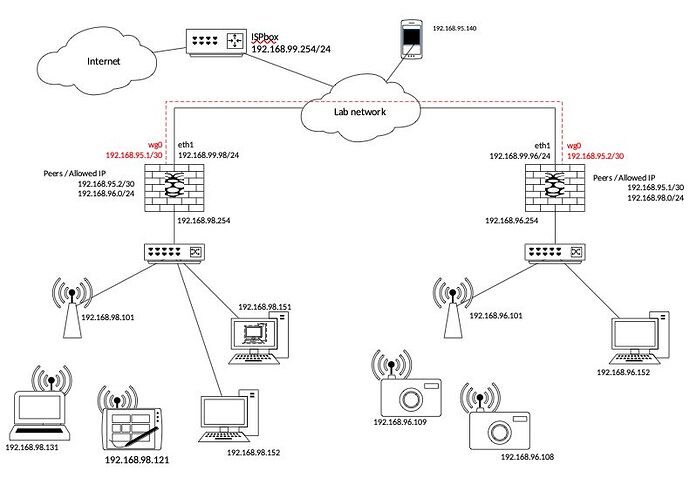
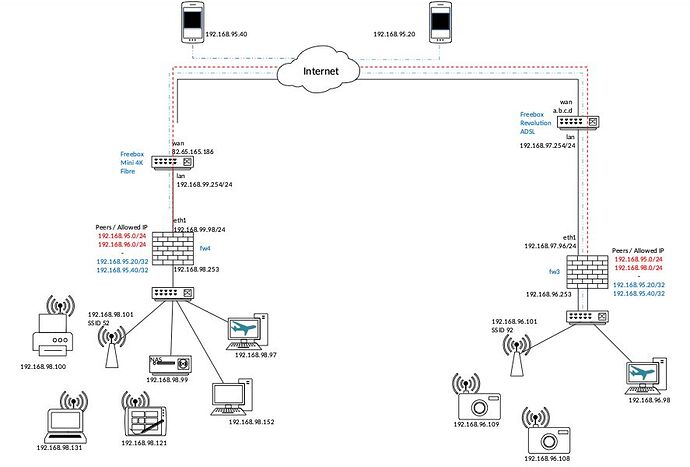
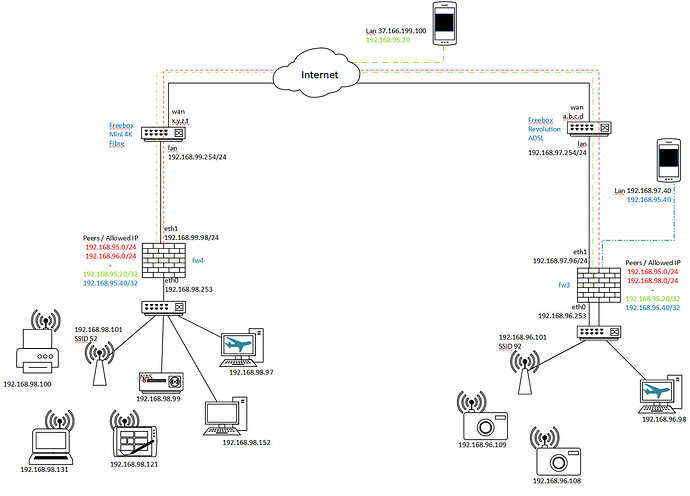
OK Thx for the hint, I'm a bit late as I made several tests.
I've tried to connect from the internet or from the network between my ISP box & the Openwrt pi, the behaviour is always the same (the example is incoming from internet)
root@fw:~# tcpdump -i eth1 -vn udp port 28041
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
04:14:00.312711 IP (tos 0x0, ttl 63, id 29042, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.96.28041 > a.b.c.d.28041: UDP, length 148
04:14:00.313606 IP (tos 0x0, ttl 62, id 29042, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.254.28041 > 192.168.97.96.28041: UDP, length 148
04:14:05.588439 IP (tos 0x0, ttl 63, id 2862, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.96.28041 > a.b.c.d.28041: UDP, length 148
04:14:05.589293 IP (tos 0x0, ttl 62, id 2862, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.254.28041 > 192.168.97.96.28041: UDP, length 148
04:14:10.753868 IP (tos 0x0, ttl 63, id 51807, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.96.28041 > a.b.c.d.28041: UDP, length 148
04:14:10.754699 IP (tos 0x0, ttl 62, id 51807, offset 0, flags [none], proto UDP (17), length 176)
192.168.97.254.28041 > 192.168.97.96.28041: UDP, length 148
So it doesn't seem to be an ISP box problem... On the other side connection goes OK
root@ew:~# tcpdump -i eth1 -vn udp port 33901
tcpdump: listening on eth1, link-type EN10MB (Ethernet), capture size 262144 bytes
11:28:21.197310 IP (tos 0x0, ttl 58, id 40744, offset 0, flags [none], proto UDP (17), length 176)
x.y.z.t.40503 > 192.168.99.98.33901: UDP, length 148
11:28:21.200387 IP (tos 0x88, ttl 64, id 40242, offset 0, flags [none], proto UDP (17), length 120)
192.168.99.98.33901 > x.y.z.t.40503: UDP, length 92
11:28:21.277417 IP (tos 0x0, ttl 58, id 3863, offset 0, flags [none], proto UDP (17), length 124)
x.y.z.t.40503 > 192.168.99.98.33901: UDP, length 96
11:28:21.281567 IP (tos 0x0, ttl 64, id 40253, offset 0, flags [none], proto UDP (17), length 284)
192.168.99.98.33901 > x.y.z.t.40503: UDP, length 256
11:28:21.284272 IP (tos 0x0, ttl 58, id 48927, offset 0, flags [none], proto UDP (17), length 124)
x.y.z.t.40503 > 192.168.99.98.33901: UDP, length 96
11:28:21.285261 IP (tos 0x0, ttl 64, id 40254, offset 0, flags [none], proto UDP (17), length 140)
192.168.99.98.33901 > x.y.z.t.40503: UDP, length 112
11:28:22.604218 IP (tos 0x0, ttl 58, id 12691, offset 0, flags [none], proto UDP (17), length 156)
x.y.z.t.40503 > 192.168.99.98.33901: UDP, length 128
11:28:22.604218 IP (tos 0x0, ttl 58, id 47644, offset 0, flags [none], proto UDP (17), length 156)
x.y.z.t.40503 > 192.168.99.98.33901: UDP, length 128
So now I'm a bit lost! Any ideas would help...