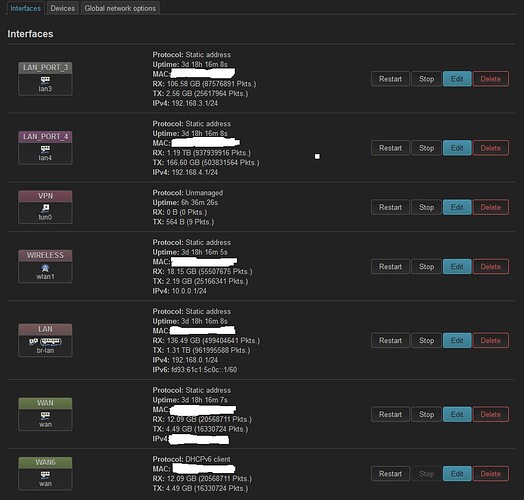
Greetings.
I would like to ask the community for help. I'm trying to get WireGuard to function between two routers and I'm having trouble. I think it's coming down to a routing issue. My scenario is below:
Main router to internet has a second router connected to it. It's this connection I'd like to use WireGuard on.
The second router sits on the main router's 192.168.3.0 subnet as 192.168.3.215 and that second router (and all of its devices) can access the internet fine without WireGuard.
I tried the following configurations and it locked me out of the second router (had to boot to safe mode to restore it), which is why I think my routing was wrong.
Any thoughts on what I might be doing wrong? Do I need to use different "allowed_ips"? Do I need to add additional routing (and I'm not sure what routing to use if so)?
Thanks for your thoughts.
Main router
config interface 'vpn'
option proto 'wireguard'
option private_key '###'
option listen_port '51820'
config wireguard_vpn
option public_key '###'
option preshared_key '###'
option description 'Site B'
list allowed_ips '192.168.3.0/24'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host 192.168.3.215
option endpoint_port '51820'
Second router
config interface 'vpn'
option proto 'wireguard'
option private_key '###'
option listen_port '51820'
config wireguard_vpn
option public_key '###'
option preshared_key '###'
option description 'Site A'
list allowed_ips '192.168.0.0/24'
option route_allowed_ips '1'
option persistent_keepalive '25'
option endpoint_host 192.168.3.1
option endpoint_port '51820'