config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option output 'ACCEPT'
option mtu_fix '1'
option network 'wan wan6'
option masq '1'
option forward 'REJECT'
option input 'DROP'
option name 'WAN'
config rule
option name 'Allow-DHCP-Renew'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
option src 'WAN'
config rule
option name 'Allow-Ping'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-IGMP'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-DHCPv6'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-MLD'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config rule
option name 'Allow-ICMPv6-Forward'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option src 'WAN'
config include
option path '/etc/firewall.user'
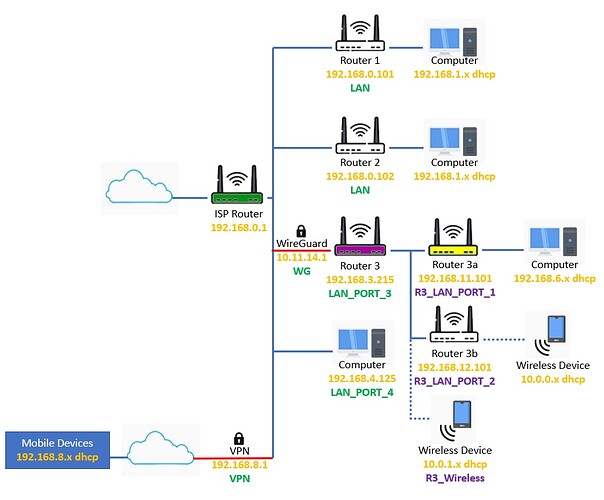
config zone
option name 'R3_LAN_Port_4'
option output 'ACCEPT'
option network 'R3_LAN_Port_4'
option forward 'REJECT'
option input 'ACCEPT'
config zone
option name 'R3_LAN_Port_3'
option output 'ACCEPT'
option network 'R3_LAN_Port_3'
option forward 'REJECT'
option input 'ACCEPT'
config zone
option name 'Wireless'
option output 'ACCEPT'
option network 'Wireless'
option input 'ACCEPT'
option forward 'REJECT'
config forwarding
option src 'R3_LAN_Port_4'
option dest 'WAN'
config forwarding
option src 'R3_LAN_Port_3'
option dest 'WAN'
config forwarding
option src 'Wireless'
option dest 'WAN'
config rule
option target 'ACCEPT'
option src 'Wireless'
option name 'Wireless DHCP'
option dest_port '67-68'
config rule
option target 'ACCEPT'
option src 'Wireless'
option name 'Wireless DNS'
option dest_port '53'
config rule
option target 'ACCEPT'
option src 'R3_LAN_Port_4'
option name 'R3_LAN Port 4 DHCP'
option dest_port '67-68'
config rule
option target 'ACCEPT'
option src 'R3_LAN_Port_4'
option name 'R3_LAN Port 4 DNS'
option dest_port '53'
config rule
option target 'ACCEPT'
option name 'R3_LAN Port 3 DHCP'
option src 'R3_LAN_Port_3'
option dest_port '67-68'
config rule
option target 'ACCEPT'
option src 'R3_LAN_Port_3'
option name 'R3_LAN Port 3 DNS'
option dest_port '53'
config zone
option output 'ACCEPT'
option name 'R3_LAN_Port_1'
list network 'R3_LAN_Port_1'
option input 'ACCEPT'
option forward 'REJECT'
config forwarding
option src 'R3_LAN_Port_1'
option dest 'WAN'
config zone
option name 'R3_LAN_Port_2'
option network 'R3_LAN_Port_2'
option output 'ACCEPT'
option forward 'REJECT'
option input 'ACCEPT'
config forwarding
option src 'R3_LAN_Port_2'
option dest 'WAN'
config rule
option src 'R3_LAN_Port_2'
option name 'R3_LAN Port 2 DHCP'
option target 'ACCEPT'
option dest_port '67-68'
config rule
option src 'R3_LAN_Port_2'
option name 'R3_LAN Port 2 DNS'
option target 'ACCEPT'
option dest_port '53'
config rule
option dest_port '67-68'
option src 'R3_LAN_Port_1'
option name 'R3_LAN Port 1 DNS'
option target 'ACCEPT'
config rule
option dest_port '53'
option src 'R3_LAN_Port_1'
option target 'ACCEPT'
option name 'R3_LAN Port 1 DNS'
config rule
option name 'Luci from WAN'
list proto 'tcp'
option target 'ACCEPT'
option dest_port '80'
option src 'WAN'
config rule
option name 'Luci from WAN SSL'
list proto 'tcp'
option target 'ACCEPT'
option dest_port '443'
option src 'WAN'
config rule
option name 'SSH from WAN'
list proto 'tcp'
option target 'ACCEPT'
option dest_port '22'
option src 'WAN'
config zone
option name 'WireGuard'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'WAN'
config forwarding
option src 'R3_LAN_Port_1'
option dest 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'R3_LAN_Port_1'
config forwarding
option src 'WAN'
option dest 'WireGuard'
config rule
option name 'Luci from WireGuard'
option src 'WireGuard'
option dest_port '80'
option target 'ACCEPT'
config rule
option name 'Luci from WireGuard SSL'
option src 'WireGuard'
option dest_port '443'
option target 'ACCEPT'
config forwarding
option src 'R3_LAN_Port_2'
option dest 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'R3_LAN_Port_2'
config forwarding
option src 'R3_LAN_Port_3'
option dest 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'R3_LAN_Port_3'
config forwarding
option src 'Wireless'
option dest 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'Wireless'
config forwarding
option src 'R3_LAN_Port_4'
option dest 'WireGuard'
config forwarding
option src 'WireGuard'
option dest 'R3_LAN_Port_4'