Hi there,
I'm fairly new to openwrt, but a pretty advanced user of Fresh Tomato, and the level of abstraction/changes I'm facing is challenging ![]()
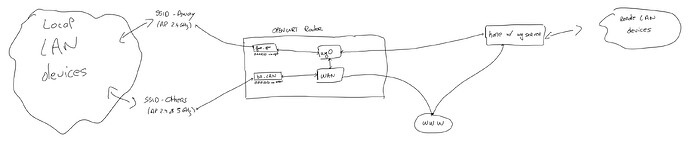
I'm trying to create the following:
- A LAN network consisting of 3 AP handled by openwrt: two normal ones (on 2.4 and 5 Ghz) and one AP named "Away" that would route all the traffic received to internet via a Wireguard tunnel.
- The Wireguard tunnel is leading to my home network and would route all the traffic of the internet so the device connected would be able to access some of my servers/services and have my public IP address when browsing the web.
Sometime a handmade diagram is better than words to explain things, so here it is:
The issues I'm facing right now:
-
Sometimes (like in the current config you'll find below), the handshake for the WG0 interface doesn't work and I'm stuck with no connectivity. There's definitely a problem with my firewalling/routing that I can't pinpoint.
-
The routing seems problematic as well. When the WG does work, all the traffic of all the interfaces is routed through the VPN. Even though I created a static IPV4 routing policy and a dedicated routing table for the VPN. Which leads to a total loss of connectivity when the Wireguard interface doesn't work.
Please find below the different configuration files of my current configuration:
/etc/config/network
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd5d:2359:e23b::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.40.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
config interface 'wg0'
option proto 'wireguard'
option private_key 'some info here'
list addresses '10.175.214.7/24'
option defaultroute '0'
config interface 'iface_vpn'
option proto 'static'
option ipaddr '192.168.41.1'
option netmask '255.255.255.0'
config rule
option in 'iface_vpn'
option lookup '100'
option out 'wg0'
config wireguard_wg0
option description 'MMA-ROUTER.conf'
option public_key 'some info here'
option preshared_key 'some info here'
option endpoint_host 'some info here'
option endpoint_port '51820'
list allowed_ips '0.0.0.0/0'
option persistent_keepalive '25'
/etc/config/wireless
cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:01.0/0000:02:00.0'
option channel 'auto'
option band '2g'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Ma2.4'
option encryption 'sae-mixed'
option key 'some info here'
config wifi-device 'radio1'
option type 'mac80211'
option path '1e140000.pcie/pci0000:00/0000:00:00.0/0000:01:00.0'
option channel 'auto'
option band '5g'
option htmode 'VHT80'
option cell_density '0'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'Ma5.0'
option encryption 'sae-mixed'
option key 'some info here'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'Away'
option encryption 'psk2'
option key 'some info here'
option network 'iface_vpn'
/etc/config/firewall
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wg0'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option network 'iface_vpn'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'vpn'
option dest 'wan'
config rule
option name 'Allow-WireGuard-Out'
option src '*'
option dest 'wan'
option proto 'udp'
option dest_port '51820'
option target 'ACCEPT'
config rule
option name 'Allow-Administration'
option src 'wan'
option dest_port '443 80 22 21'
option target 'ACCEPT'
/etc/iproute2/rt_tables
cat /etc/iproute2/rt_tables
#
# reserved values
#
128 prelocal
255 local
254 main
253 default
0 unspec
#
# local
#
#1 inr.ruhep
100 iface_vpn
256 pbr_wan
257 pbr_wg0
That should be the entirety of my configuration.
Help would be appreciated !
Thanks,
F