I can't get my wireguard client to work with PBR (Version 1.1.7-67).
My two OPEN-VPN clients work fine with PBR.
Can anyone see what I missed in my wireguard client configuration?
Can see my client has a handshake with the ISP's server.
Please connect to your OpenWrt device using ssh and copy the output of the following commands and post it here using the "Preformatted text </> " button:
![]()
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
ubus call system board
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
root@DEFCON:~# ubus call system board
{
"kernel": "5.15.167",
"hostname": "DEFCON",
"system": "ARMv8 Processor rev 4",
"model": "GL.iNet GL-MT6000",
"board_name": "glinet,gl-mt6000",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.5",
"revision": "r24106-10cc5fcd00",
"target": "mediatek/filogic",
"description": "OpenWrt 23.05.5 r24106-10cc5fcd00"
}
}
root@DEFCON:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda1:cc83:50bb::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config device
option name 'lan1'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan2'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan3'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan4'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan5'
option macaddr '94:83:c4:a5:ff:7f'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth1'
option macaddr '94:83:c4:a5:ff:7d'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option type 'bridge'
option name 'br-guest'
option bridge_empty '1'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
config interface 'OpenVPN'
option proto 'none'
option device 'tun0'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
config interface 'OpenVPN2'
option proto 'none'
option device 'tun1'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
option delegate '0'
config interface 'wgc1'
option proto 'wireguard'
option private_key '<privare key>'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
list addresses '172.30.72.18/32'
list addresses 'fd00:0000:1337:cafe:1111:1111:766c:0537/128'
option mtu '1420'
config wireguard_wgc1
option description 'vpn62-sthlm'
option public_key '<public key>'
option endpoint_host 'vpn62.prd.kista.ovpn.com'
option endpoint_port '9929'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
option route_allowed_ips '1'
config wireguard_wgc1
option description 'vpn23-sthlm'
option public_key '<public key>'
option endpoint_host 'vpn23.prd.kista.ovpn.com'
option endpoint_port '9929'
option persistent_keepalive '25'
option disabled '1'
option route_allowed_ips '1'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
root@DEFCON:~# cat /etc/config/wireless
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/18000000.wifi'
option channel '1'
option band '2g'
option htmode 'HE40'
option txpower '20'
option cell_density '0'
option country 'SE'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'Defcon1.2'
option encryption 'sae-mixed'
option key '<key>'
option dtim_period '3'
config wifi-device 'radio1'
option type 'mac80211'
option path 'platform/soc/18000000.wifi+1'
option channel '124'
option band '5g'
option htmode 'HE160'
option txpower '20'
option cell_density '0'
option country 'SE'
config wifi-iface 'default_radio1'
option device 'radio1'
option network 'lan'
option mode 'ap'
option ssid 'Defcon1.5'
option encryption 'sae-mixed'
option dtim_period '3'
option key '<key>'
config wifi-iface 'wifinet2'
option device 'radio0'
option mode 'ap'
option ssid 'Defcon1.2-Guest'
option encryption 'sae-mixed'
option network 'guest'
option key '<key>'
root@DEFCON:~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'home.lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.wg'
option localservice '1'
option ednspacket_max '1280'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
option force '1'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
root@DEFCON:~# cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'tun0'
list device 'tun1'
list network 'OpenVPN'
list network 'OpenVPN2'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding
option src 'guest'
option dest 'wan'
config rule
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Allow-DHCP-Guest'
list proto 'udp'
option src 'guest'
option dest_port '67'
option target 'ACCEPT'
config zone
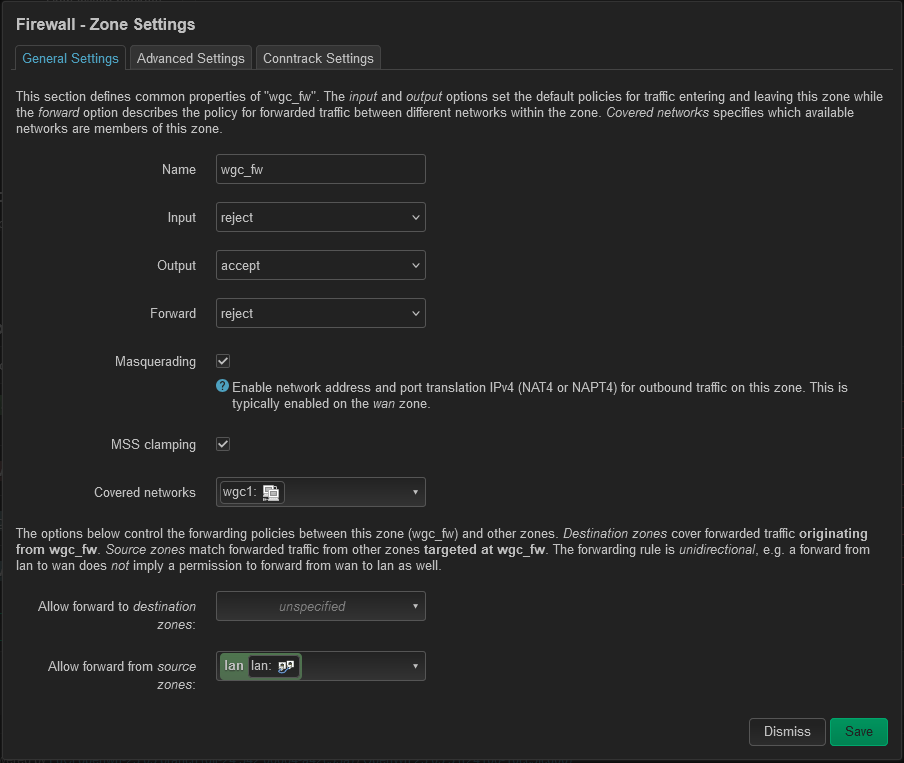
option name 'wgc_fw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wgc1'
config forwarding
option src 'lan'
option dest 'wgc_fw'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'
Disable or remove route_allowed_ips
You can indeed only have one peer per tunnel.
You can however make more tunnels to different locations
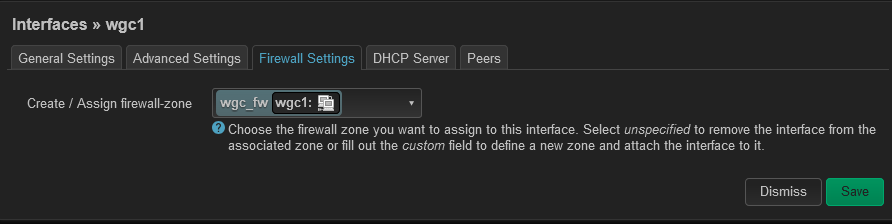
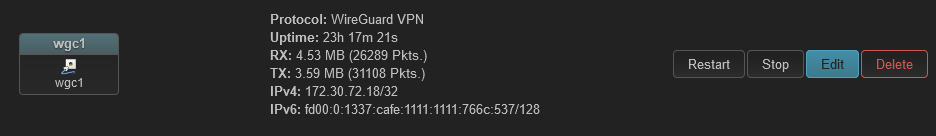
I have turned it off ( option route_allowed_ips '0') but can't still not get PBR working when choose "wgc1" interface.
Is Firewall and Inteface right configured?
I have only on peer running and have other as reserv if i need to change fast.
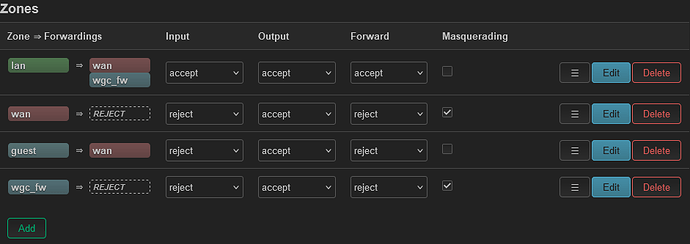
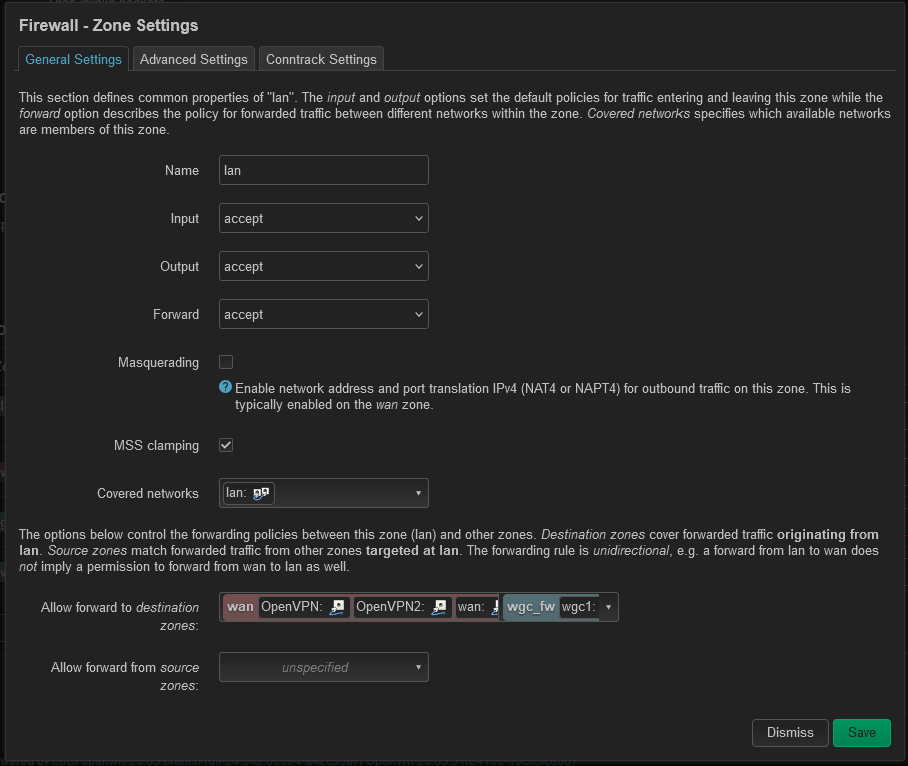
For lan clients the firewall is configured ok.
Not for guest clients as there is no forwarding from guest to wgc_fw
Yes, for now I have choose to route guest to wan.
Problem is I can't route wgc1 with PBR to working.
Hence it's working fine with my two openvpn clients.
Can PBR been using to policy routing wireguard clients?
I have tried removing "option route_allowed_ips '1' but it made no difference.
Tried in README to remove "redirect-gateway" from the VPN interface and "route_allowed_ips" for wireguard.
It worked for a while, then OpenVPN fell back to wan/eth1 route.
(it worked for about 30 seconds)
I have no idea why though
Maby I should try to use "route-nopull" instead?
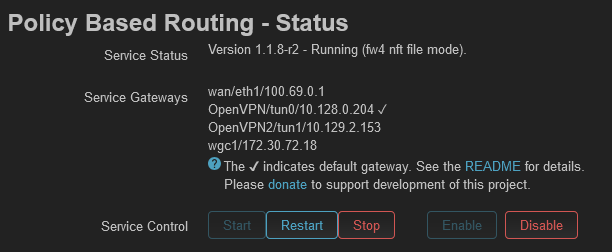
I have tried the new PBR (Version 1.1.8-r2) and it works, but can't get wireguard client to route via PBR.
OpenVPN/tun0 OpenVPN2/tun1 and wan/eth1 work but not "wgc1".
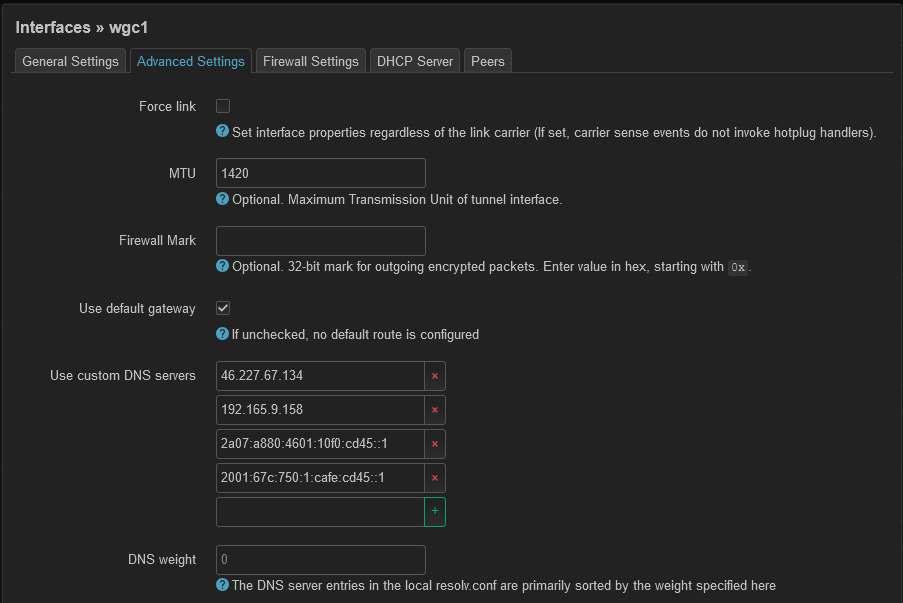
Not sure if I have managed to configure the firewall and interface correctly.
Can anyone see if there is any bad configuration?
Mon Dec 23 17:58:17 2024 user.notice pbr [13660]: Using wan interface (on_start): wan
Mon Dec 23 17:58:17 2024 user.notice pbr [13660]: Found wan gateway (on_start): 100.69.0.1
Mon Dec 23 17:58:18 2024 user.notice pbr [13660]: Setting up routing for 'wan/eth1/100.69.0.1' [✓]
Mon Dec 23 17:58:19 2024 user.notice pbr [13660]: Setting up routing for 'OpenVPN/tun0/10.128.0.204' [✓]
Mon Dec 23 17:58:19 2024 user.notice pbr [13660]: Setting up routing for 'OpenVPN2/tun1/10.129.2.153' [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Setting up routing for 'wgc1/172.30.72.18' [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Routing 'xxxxx-PC-lan' via OpenVPN [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Routing 'xxxxx-S24' via OpenVPN2 [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Routing 'xxxxxx' via wan [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Routing 'iplocation' via wgc1 [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Routing 'xxxxxx' DNS to 213.80.98.2 [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: Installing fw4 nft file [✓]
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: pbr 1.1.8-r2 monitoring interfaces: OpenVPN OpenVPN2 wan wgc1
Mon Dec 23 17:58:20 2024 user.notice pbr [13660]: pbr 1.1.8-r2 (fw4 nft file mode) started with gateways: wan/eth1/100.69.0.1 OpenVPN/tun0/10.128.0.204 [✓] OpenVPN2/tun1/10.129.2.153 wgc1/172.30.72.18
Mon Dec 23 17:58:22 2024 user.notice pbr: Sending reload signal to pbr due to firewall action: includes
Mon Dec 23 17:58:22 2024 user.notice pbr: Reusing the fw4 nft file.
Mon Dec 23 17:58:47 2024 user.notice pbr [16575]: Using wan interface (on_start): wan
Mon Dec 23 17:58:47 2024 user.notice pbr [16575]: Found wan gateway (on_start): 100.69.0.1
Mon Dec 23 17:58:49 2024 user.notice pbr [16575]: Setting up routing for 'wan/eth1/100.69.0.1' [✓]
Mon Dec 23 17:58:49 2024 user.notice pbr [16575]: Setting up routing for 'OpenVPN/tun0/10.128.0.204' [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Setting up routing for 'OpenVPN2/tun1/10.129.2.153' [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Setting up routing for 'wgc1/172.30.72.18' [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Routing 'xxxxx-PC-lan' via OpenVPN [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Routing 'xxxxx-S24' via OpenVPN2 [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Routing 'xxxxx' via wan [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Routing 'iplocation' via wan [✓]
Mon Dec 23 17:58:50 2024 user.notice pbr [16575]: Routing 'xxxxx' DNS to 213.80.98.2 [✓]
Mon Dec 23 17:58:51 2024 user.notice pbr [16575]: Installing fw4 nft file [✓]
Mon Dec 23 17:58:51 2024 user.notice pbr [16575]: pbr 1.1.8-r2 monitoring interfaces: OpenVPN OpenVPN2 wan wgc1
Mon Dec 23 17:58:51 2024 user.notice pbr [16575]: pbr 1.1.8-r2 (fw4 nft file mode) started with gateways: wan/eth1/100.69.0.1 OpenVPN/tun0/10.128.0.204 [✓] OpenVPN2/tun1/10.129.2.153 wgc1/172.30.72.18
Mon Dec 23 17:58:52 2024 user.notice pbr: Sending reload signal to pbr due to firewall action: includes
Mon Dec 23 17:58:52 2024 user.notice pbr: Reusing the fw4 nft file.
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda1:cc83:50bb::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config device
option name 'lan1'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan2'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan3'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan4'
option macaddr '94:83:c4:a5:ff:7f'
config device
option name 'lan5'
option macaddr '94:83:c4:a5:ff:7f'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config device
option name 'eth1'
option macaddr '94:83:c4:a5:ff:7d'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config device
option type 'bridge'
option name 'br-guest'
option bridge_empty '1'
config interface 'guest'
option proto 'static'
option device 'br-guest'
option ipaddr '192.168.2.1'
option netmask '255.255.255.0'
option gateway '192.168.1.1'
config interface 'OpenVPN'
option proto 'none'
option device 'tun0'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
config interface 'OpenVPN2'
option proto 'none'
option device 'tun1'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
option delegate '0'
config interface 'wgc1'
option proto 'wireguard'
option private_key 'private key'
list dns '46.227.67.134'
list dns '192.165.9.158'
list dns '2a07:a880:4601:10f0:cd45::1'
list dns '2001:67c:750:1:cafe:cd45::1'
list addresses '172.30.72.18/32'
list addresses 'fd00:0000:1337:cafe:1111:1111:766c:0537/128'
option mtu '1420'
config wireguard_wgc1
option description 'vpn62-sthlm'
option public_key 'public key'
option endpoint_host 'vpn62.prd.kista.ovpn.com'
option endpoint_port '9929'
option persistent_keepalive '25'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
config wireguard_wgc1
option description 'vpn23-sthlm'
option public_key 'public key'
option endpoint_host 'vpn23.prd.kista.ovpn.com'
option endpoint_port '9929'
option persistent_keepalive '25'
option disabled '1'
list allowed_ips '0.0.0.0/0'
list allowed_ips '::/0'
config pbr 'config'
option enabled '1'
option verbosity '2'
option strict_enforcement '1'
option resolver_set 'none'
list resolver_instance '*'
option ipv6_enabled '0'
list ignored_interface 'vpnserver'
option boot_timeout '30'
option rule_create_option 'add'
option procd_boot_delay '15'
option procd_reload_delay '1'
option webui_show_ignore_target '0'
option nft_rule_counter '0'
option nft_set_auto_merge '1'
option nft_set_counter '0'
option nft_set_flags_interval '1'
option nft_set_flags_timeout '0'
option nft_set_policy 'performance'
list webui_supported_protocol 'all'
list webui_supported_protocol 'tcp'
list webui_supported_protocol 'udp'
list webui_supported_protocol 'tcp udp'
list webui_supported_protocol 'icmp'
config include
option path '/usr/share/pbr/pbr.user.aws'
option enabled '0'
config include
option path '/usr/share/pbr/pbr.user.netflix'
option enabled '0'
config dns_policy
option name 'Johan-PC-lan'
option src_addr '192.168.1.113'
option dest_dns '46.227.67.134'
option enabled '0'
config dns_policy
option name 'xxxxxx-S24'
option src_addr '192.168.1.199'
option dest_dns '46.227.67.134'
option enabled '0'
config dns_policy
option name 'xxxxxxx'
option src_addr '192.168.1.151'
option dest_dns '213.80.98.2'
config dns_policy
option name 'Redirect Local IP DNS'
option src_addr '192.168.1.5'
option dest_dns '1.1.1.1'
option enabled '0'
config policy
option name 'Ignore Local Requests'
option interface 'ignore'
option dest_addr '10.0.0.0/24 10.0.1.0/24 192.168.100.0/24 192.168.1.0/24'
option enabled '0'
config policy
option name 'xxxxx-PC-lan'
option src_addr '192.168.1.113'
option interface 'OpenVPN'
config policy
option name 'xxxxx-S24'
option src_addr '192.168.1.199'
option interface 'OpenVPN2'
config policy
option name 'xxxxxx'
option src_addr '192.168.1.151'
option interface 'wan'
config policy
option name 'iplocation'
option dest_addr 'iplocation.com'
option interface 'wan'
config policy
option name 'ipleak.net'
option interface 'wan'
option dest_addr 'ipleak.net'
option enabled '0'
config policy
option name 'Plex/Emby Local Server'
option interface 'wan'
option src_port '8096 8920 32400'
option enabled '0'
config policy
option name 'Plex/Emby Remote Servers'
option interface 'wan'
option dest_addr 'plex.tv my.plexapp.com emby.media app.emby.media tv.emby.media'
option enabled '0'
config dns_policy
option name 'iplocation dns'
option src_addr 'iplocation'
option dest_dns '46.227.67.134'
option enabled '0'
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option mtu_fix '1'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list device 'tun0'
list device 'tun1'
list network 'OpenVPN'
list network 'OpenVPN2'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'guest'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'guest'
config forwarding
option src 'guest'
option dest 'wan'
config rule
option name 'Allow-DNS-Guest'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Allow-DHCP-Guest'
list proto 'udp'
option src 'guest'
option dest_port '67'
option target 'ACCEPT'
config zone
option name 'wgc_fw'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wgc1'
config forwarding
option src 'lan'
option dest 'wgc_fw'
config forwarding
option src 'guest'
option dest 'wgc_fw'
config include 'pbr'
option fw4_compatible '1'
option type 'script'
option path '/usr/share/pbr/firewall.include'
At this moment you have no policies to route via WireGuard but lets see if WireGuard is working first.
What is the output of ![]()
wg show
ip route show
ip route show table all
ip rule show
As a test you can disable OpenVPN and disable PBR.
In the WireGuard interface enable Route-Allowed IPs and after that reboot.
Then everything should go via the WG interface, check with ipleak.net
I'll try this later, show the interface for now
root@DEFCON:~# wg show
interface: wgc1
public key: public key
private key: (hidden)
listening port: 44939
peer: peer key
endpoint: 217.64.148.68:9929
allowed ips: 0.0.0.0/0, ::/0
latest handshake: 38 seconds ago
transfer: 10.14 MiB received, 7.72 MiB sent
persistent keepalive: every 25 seconds
root@DEFCON:~# ip route show
0.0.0.0/1 via 10.128.0.1 dev tun0
default via 100.69.0.1 dev eth1 proto static src 100.69.14.38
10.128.0.0/22 dev tun0 proto kernel scope link src 10.128.0.204
10.129.0.0/22 dev tun1 proto kernel scope link src 10.129.2.153
46.227.67.134 dev wgc1 scope link
100.69.0.0/17 dev eth1 proto kernel scope link src 100.69.14.38
128.0.0.0/1 via 10.128.0.1 dev tun0
192.165.9.158 dev wgc1 scope link
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest proto kernel scope link src 192.168.2.1
217.64.148.48 via 100.69.0.1 dev eth1
root@DEFCON:~# ip route show table all
default via 100.69.0.1 dev eth1 table pbr_wan
192.168.1.0/24 dev br-lan table pbr_wan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest table pbr_wan proto kernel scope link src 192.168.2.1
default via 10.128.0.204 dev tun0 table pbr_OpenVPN
192.168.1.0/24 dev br-lan table pbr_OpenVPN proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest table pbr_OpenVPN proto kernel scope link src 192.168.2.1
default via 10.129.2.153 dev tun1 table pbr_OpenVPN2
192.168.1.0/24 dev br-lan table pbr_OpenVPN2 proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest table pbr_OpenVPN2 proto kernel scope link src 192.168.2.1
default via 172.30.72.18 dev wgc1 table pbr_wgc1
192.168.1.0/24 dev br-lan table pbr_wgc1 proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest table pbr_wgc1 proto kernel scope link src 192.168.2.1
0.0.0.0/1 via 10.128.0.1 dev tun0
default via 100.69.0.1 dev eth1 proto static src 100.69.14.38
10.128.0.0/22 dev tun0 proto kernel scope link src 10.128.0.204
10.129.0.0/22 dev tun1 proto kernel scope link src 10.129.2.153
46.227.67.134 dev wgc1 scope link
100.69.0.0/17 dev eth1 proto kernel scope link src 100.69.14.38
128.0.0.0/1 via 10.128.0.1 dev tun0
192.165.9.158 dev wgc1 scope link
192.168.1.0/24 dev br-lan proto kernel scope link src 192.168.1.1
192.168.2.0/24 dev br-guest proto kernel scope link src 192.168.2.1
217.64.148.48 via 100.69.0.1 dev eth1
local 10.128.0.204 dev tun0 table local proto kernel scope host src 10.128.0.204
broadcast 10.128.3.255 dev tun0 table local proto kernel scope link src 10.128.0.204
local 10.129.2.153 dev tun1 table local proto kernel scope host src 10.129.2.153
broadcast 10.129.3.255 dev tun1 table local proto kernel scope link src 10.129.2.153
local 100.69.14.38 dev eth1 table local proto kernel scope host src 100.69.14.38
broadcast 100.69.127.255 dev eth1 table local proto kernel scope link src 100.69.14.38
local 127.0.0.0/8 dev lo table local proto kernel scope host src 127.0.0.1
local 127.0.0.1 dev lo table local proto kernel scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local proto kernel scope link src 127.0.0.1
local 172.30.72.18 dev wgc1 table local proto kernel scope host src 172.30.72.18
local 192.168.1.1 dev br-lan table local proto kernel scope host src 192.168.1.1
broadcast 192.168.1.255 dev br-lan table local proto kernel scope link src 192.168.1.1
local 192.168.2.1 dev br-guest table local proto kernel scope host src 192.168.2.1
broadcast 192.168.2.255 dev br-guest table local proto kernel scope link src 192.168.2.1
default from 2001:9b0:41::c934:936b via fe80::a67b:2cff:fe9e:ea01 dev eth1 proto static metric 512 pref medium
default from 2001:9b1:df0:e100::/56 via fe80::a67b:2cff:fe9e:ea01 dev eth1 proto static metric 512 pref medium
2001:67c:750:1:cafe:cd45:0:1 dev wgc1 metric 1024 pref medium
2001:9b1:df0:e100::/64 dev br-lan proto static metric 1024 pref medium
unreachable 2001:9b1:df0:e100::/56 dev lo proto static metric 2147483647 pref medium
2a07:a880:4601:10f0:cd45::1 dev wgc1 metric 1024 pref medium
fd00:0:1337:cafe:1111:1111:766c:537 dev wgc1 proto kernel metric 256 pref medium
fda1:cc83:50bb::/64 dev br-lan proto static metric 1024 pref medium
unreachable fda1:cc83:50bb::/48 dev lo proto static metric 2147483647 pref medium
fe80::/64 dev eth0 proto kernel metric 256 pref medium
fe80::/64 dev br-lan proto kernel metric 256 pref medium
fe80::/64 dev eth1 proto kernel metric 256 pref medium
fe80::/64 dev phy0-ap0 proto kernel metric 256 pref medium
fe80::/64 dev br-guest proto kernel metric 256 pref medium
fe80::/64 dev phy0-ap1 proto kernel metric 256 pref medium
fe80::/64 dev tun0 proto kernel metric 256 pref medium
fe80::/64 dev tun1 proto kernel metric 256 pref medium
fe80::/64 dev phy1-ap0 proto kernel metric 256 pref medium
local ::1 dev lo table local proto kernel metric 0 pref medium
local 2001:9b0:41::c934:936b dev eth1 table local proto kernel metric 0 pref medium
anycast 2001:9b1:df0:e100:: dev br-lan table local proto kernel metric 0 pref medium
local 2001:9b1:df0:e100::1 dev br-lan table local proto kernel metric 0 pref medium
local fd00:0:1337:cafe:1111:1111:766c:537 dev wgc1 table local proto kernel metric 0 pref medium
anycast fda1:cc83:50bb:: dev br-lan table local proto kernel metric 0 pref medium
local fda1:cc83:50bb::1 dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth0 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-lan table local proto kernel metric 0 pref medium
anycast fe80:: dev eth1 table local proto kernel metric 0 pref medium
anycast fe80:: dev phy0-ap1 table local proto kernel metric 0 pref medium
anycast fe80:: dev phy0-ap0 table local proto kernel metric 0 pref medium
anycast fe80:: dev br-guest table local proto kernel metric 0 pref medium
anycast fe80:: dev tun0 table local proto kernel metric 0 pref medium
anycast fe80:: dev tun1 table local proto kernel metric 0 pref medium
anycast fe80:: dev phy1-ap0 table local proto kernel metric 0 pref medium
local fe80::68c4:ebc4:e5e5:f4b0 dev tun1 table local proto kernel metric 0 pref medium
local fe80::8c23:baff:feb1:841b dev eth0 table local proto kernel metric 0 pref medium
local fe80::9483:c4ff:fea5:ff80 dev phy0-ap1 table local proto kernel metric 0 pref medium
local fe80::9483:c4ff:fea5:ff80 dev br-guest table local proto kernel metric 0 pref medium
local fe80::9683:c4ff:fea5:ff7d dev eth1 table local proto kernel metric 0 pref medium
local fe80::9683:c4ff:fea5:ff7f dev br-lan table local proto kernel metric 0 pref medium
local fe80::9683:c4ff:fea5:ff80 dev phy0-ap0 table local proto kernel metric 0 pref medium
local fe80::9683:c4ff:fea5:ff81 dev phy1-ap0 table local proto kernel metric 0 pref medium
local fe80::a6ae:b677:84a9:7c1 dev tun0 table local proto kernel metric 0 pref medium
multicast ff00::/8 dev eth0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev br-lan table local proto kernel metric 256 pref medium
multicast ff00::/8 dev eth1 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev phy0-ap0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev br-guest table local proto kernel metric 256 pref medium
multicast ff00::/8 dev phy0-ap1 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev wgc1 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev tun0 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev tun1 table local proto kernel metric 256 pref medium
multicast ff00::/8 dev phy1-ap0 table local proto kernel metric 256 pref medium
root@DEFCON:~# ip rule show
0: from all lookup local
29994: from all fwmark 0x40000/0xff0000 lookup pbr_wgc1
29996: from all fwmark 0x30000/0xff0000 lookup pbr_OpenVPN2
29998: from all fwmark 0x20000/0xff0000 lookup pbr_OpenVPN
30000: from all fwmark 0x10000/0xff0000 lookup pbr_wan
32766: from all lookup main
32767: from all lookup default
Make a policy to route a LAN client (PC or phone) via the WG interface.
As you are using IPv6 use the MAC address as source.
After making the policy do:
service network restart
service openvpn restart
service pbr stop
service pbr start
Test with ipleak.net and myip.is
Note you are using openvpn as default routing, the problem which can arise is that you are going to run a tunnel in a tunnel, it is not the case yet but if you have multiple tunnel it is better to let the WAN be the default route and use PBR to route via the VPN's
I noticed that the above DNS servers are routed via the WG interface, this is not something which is done automatically. Are you using routing rules or scripts to do this?
It's prevent DNS leaks, it's DNS from vpn-provider and goes inside tunnel.
Comes from here:
*After change to MAC-address to my phone it starting to working. *
Can see wgc1 ip-number in ipleak and myip.
Only thing I can think off is ipv6 causes it.
With the test router I can only have CGNAT ip-number and try with.
After change to MAC-address to my phone it starting to working.
Can see wgc1 ip-number in ipleak and myip.
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
Thanks! ![]()
I haven't tried using DNS Policies yet. I don't know if it works?!
EDIT: It seems to work to use DNS policies.
@stangri
Well after a day it seems that the wireguard client is not working again with PBR.
The only thing I can think of right now is that the keep alive function is causing it.
I have no more ideas. ![]()
time mismatch maybe ? you can use ntp to update the clock
System -> System -> Time Synchronization
but you need to make sure the time gets updated via the normal lan route not the vpn route because you need the right time to get the vpn up in the first place
I have set up an NTP server and it seems to be syncing.
Haven't routed it so it should go via wan/eth1
![]()

This issue is not about having an NTP server, but rather to ensure that NTP sync (as a client) such that the clock on the OpenWrt device is accurate.
You can check this on the main status page of the web interface and/or via the command line using the command date.