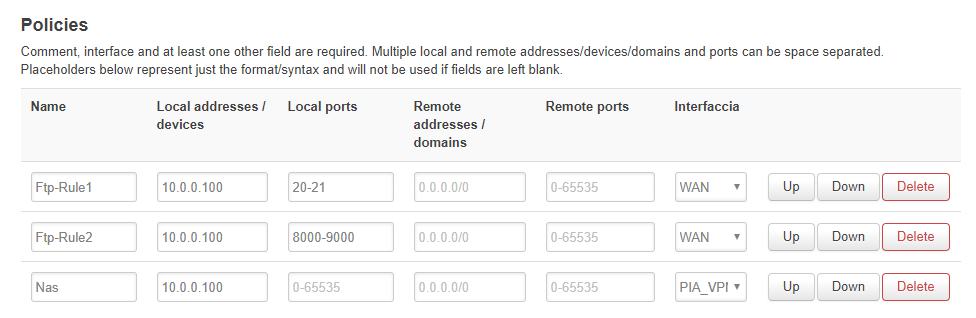
Wait, you just point me in one direction, and is good, I think/hope
I tried to better see what you said, I double check the log and I see that there's some "extra" data that "travel" I don't know if is the right word, on that port range, torrent data, so I check and I see a lot of traffic like this 10.0.0.100.46786, in this case 46786 is the portforward for pia service. So I changed the range for ftp to min 8000 and max 9000.
Why you said that the ftp don't use the correct range?
I changed the command to capture the new range
This's with pbr off
root@OpenWrt:~# tcpdump -i eth1.1 -vn 'tcp portrange 20-21 or (tcp portrange 8000-9000 and host 10.0.0.100)'
tcpdump: listening on eth1.1, link-type EN10MB (Ethernet), capture size 262144 bytes
19:30:30.401569 IP (tos 0x0, ttl 47, id 17782, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10559 > 10.0.0.100.21: Flags [S], cksum 0x59b7 (correct), seq 1181138561, win 65535, options [mss 1300,sackOK,TS val 1702903 ecr 0,nop,wscale 9], length 0
19:30:30.401959 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10559: Flags [S.], cksum 0xedc3 (correct), seq 2338870013, ack 1181138562, win 65160, options [mss 1460,sackOK,TS val 280722842 ecr 1702903,nop,wscale 7], length 0
19:30:30.719126 IP (tos 0x0, ttl 47, id 17783, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x1a60 (correct), ack 1, win 172, options [nop,nop,TS val 1702916 ecr 280722842], length 0
19:30:30.723783 IP (tos 0x0, ttl 64, id 21721, offset 0, flags [DF], proto TCP (6), length 86)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x6e7e (correct), seq 1:35, ack 1, win 510, options [nop,nop,TS val 280723164 ecr 1702916], length 34: FTP, length: 34
220 Welcome to Jorman FTP Server
19:30:31.060555 IP (tos 0x0, ttl 47, id 17784, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x18dc (correct), ack 35, win 172, options [nop,nop,TS val 1702948 ecr 280723164], length 0
19:30:31.085476 IP (tos 0x0, ttl 47, id 17785, offset 0, flags [DF], proto TCP (6), length 68)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x90e7 (correct), seq 1:17, ack 35, win 172, options [nop,nop,TS val 1702948 ecr 280723164], length 16: FTP, length: 16
USER anonymous
19:30:31.085839 IP (tos 0x0, ttl 64, id 21722, offset 0, flags [DF], proto TCP (6), length 52)
10.0.0.100.21 > 37.160.148.150.10559: Flags [.], cksum 0x1610 (correct), ack 17, win 510, options [nop,nop,TS val 280723526 ecr 1702948], length 0
19:30:31.085844 IP (tos 0x0, ttl 64, id 21723, offset 0, flags [DF], proto TCP (6), length 86)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xcec4 (correct), seq 35:69, ack 17, win 510, options [nop,nop,TS val 280723526 ecr 1702948], length 34: FTP, length: 34
331 Please specify the password.
19:30:31.426369 IP (tos 0x0, ttl 47, id 17786, offset 0, flags [DF], proto TCP (6), length 65)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0xfe24 (correct), seq 17:30, ack 69, win 172, options [nop,nop,TS val 1702986 ecr 280723526], length 13: FTP, length: 13
PASS jorman
19:30:31.439686 IP (tos 0x0, ttl 64, id 21724, offset 0, flags [DF], proto TCP (6), length 75)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x32c1 (correct), seq 69:92, ack 30, win 510, options [nop,nop,TS val 280723880 ecr 1702986], length 23: FTP, length: 23
230 Login successful.
19:30:31.574323 IP (tos 0x0, ttl 47, id 17787, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x80c0 (correct), seq 30:36, ack 92, win 172, options [nop,nop,TS val 1703020 ecr 280723880], length 6: FTP, length: 6
FEAT
19:30:31.574834 IP (tos 0x0, ttl 64, id 21725, offset 0, flags [DF], proto TCP (6), length 67)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xe950 (correct), seq 92:107, ack 36, win 510, options [nop,nop,TS val 280724015 ecr 1703020], length 15: FTP, length: 15
211-Features:
19:30:31.574840 IP (tos 0x0, ttl 64, id 21726, offset 0, flags [DF], proto TCP (6), length 117)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x0d43 (correct), seq 107:172, ack 36, win 510, options [nop,nop,TS val 280724015 ecr 1703020], length 65: FTP, length: 65
EPRT
EPSV
MDTM
PASV
REST STREAM
SIZE
TVFS
211 End
19:30:31.689462 IP (tos 0x0, ttl 47, id 17788, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x1488 (correct), ack 172, win 172, options [nop,nop,TS val 1703033 ecr 280724015], length 0
19:30:31.722758 IP (tos 0x0, ttl 47, id 17789, offset 0, flags [DF], proto TCP (6), length 57)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x7616 (correct), seq 36:41, ack 172, win 172, options [nop,nop,TS val 1703033 ecr 280724015], length 5: FTP, length: 5
PWD
19:30:31.723228 IP (tos 0x0, ttl 64, id 21727, offset 0, flags [DF], proto TCP (6), length 86)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x18a4 (correct), seq 172:206, ack 41, win 510, options [nop,nop,TS val 280724164 ecr 1703033], length 34: FTP, length: 34
257 "/" is the current directory
19:30:32.088964 IP (tos 0x0, ttl 47, id 17790, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x13b9 (correct), ack 206, win 172, options [nop,nop,TS val 1703052 ecr 280724164], length 0
19:30:32.441170 IP (tos 0x0, ttl 47, id 17791, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x6900 (correct), seq 41:47, ack 206, win 172, options [nop,nop,TS val 1703053 ecr 280724164], length 6: FTP, length: 6
NOOP
19:30:32.441631 IP (tos 0x0, ttl 64, id 21728, offset 0, flags [DF], proto TCP (6), length 66)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x76e4 (correct), seq 206:220, ack 47, win 510, options [nop,nop,TS val 280724882 ecr 1703053], length 14: FTP, length: 14
200 NOOP ok.
19:30:32.557942 IP (tos 0x0, ttl 47, id 17792, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x68d1 (correct), seq 41:47, ack 206, win 172, options [nop,nop,TS val 1703100 ecr 280724164], length 6: FTP, length: 6
NOOP
19:30:32.557970 IP (tos 0x0, ttl 47, id 17793, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x1094 (correct), ack 220, win 172, options [nop,nop,TS val 1703119 ecr 280724882], length 0
19:30:32.558384 IP (tos 0x0, ttl 64, id 21729, offset 0, flags [DF], proto TCP (6), length 64)
10.0.0.100.21 > 37.160.148.150.10559: Flags [.], cksum 0xcea0 (correct), ack 47, win 510, options [nop,nop,TS val 280724999 ecr 1703100,nop,nop,sack 1 {41:47}], length 0
19:30:32.582299 IP (tos 0x0, ttl 47, id 17794, offset 0, flags [DF], proto TCP (6), length 59)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x4fff (correct), seq 47:54, ack 220, win 172, options [nop,nop,TS val 1703120 ecr 280724882], length 7: FTP, length: 7
CWD /
19:30:32.582674 IP (tos 0x0, ttl 64, id 21730, offset 0, flags [DF], proto TCP (6), length 52)
10.0.0.100.21 > 37.160.148.150.10559: Flags [.], cksum 0x0ead (correct), ack 54, win 510, options [nop,nop,TS val 280725023 ecr 1703120], length 0
19:30:32.582680 IP (tos 0x0, ttl 64, id 21731, offset 0, flags [DF], proto TCP (6), length 89)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x831e (correct), seq 220:257, ack 54, win 510, options [nop,nop,TS val 280725023 ecr 1703120], length 37: FTP, length: 37
250 Directory successfully changed.
19:30:32.824356 IP (tos 0x0, ttl 47, id 17795, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x7b18 (correct), seq 54:60, ack 257, win 172, options [nop,nop,TS val 1703136 ecr 280725023], length 6: FTP, length: 6
FEAT
19:30:32.824848 IP (tos 0x0, ttl 64, id 21732, offset 0, flags [DF], proto TCP (6), length 67)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xe33d (correct), seq 257:272, ack 60, win 510, options [nop,nop,TS val 280725265 ecr 1703136], length 15: FTP, length: 15
211-Features:
19:30:32.824853 IP (tos 0x0, ttl 64, id 21733, offset 0, flags [DF], proto TCP (6), length 101)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xc5e0 (correct), seq 272:321, ack 60, win 510, options [nop,nop,TS val 280725265 ecr 1703136], length 49: FTP, length: 49
EPRT
EPSV
MDTM
PASV
REST STREAM
SIZE
19:30:32.824856 IP (tos 0x0, ttl 64, id 21734, offset 0, flags [DF], proto TCP (6), length 68)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x6c69 (correct), seq 321:337, ack 60, win 510, options [nop,nop,TS val 280725265 ecr 1703136], length 16: FTP, length: 16
TVFS
211 End
19:30:32.938207 IP (tos 0x0, ttl 47, id 17796, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x0e6b (correct), ack 337, win 172, options [nop,nop,TS val 1703159 ecr 280725265], length 0
19:30:32.942316 IP (tos 0x0, ttl 47, id 17797, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x5aa5 (correct), seq 60:66, ack 337, win 172, options [nop,nop,TS val 1703159 ecr 280725265], length 6: FTP, length: 6
SYST
19:30:32.942774 IP (tos 0x0, ttl 64, id 21735, offset 0, flags [DF], proto TCP (6), length 71)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xa531 (correct), seq 337:356, ack 66, win 510, options [nop,nop,TS val 280725383 ecr 1703159], length 19: FTP, length: 19
215 UNIX Type: L8
19:30:33.108137 IP (tos 0x0, ttl 47, id 17798, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x5d21 (correct), seq 66:72, ack 356, win 172, options [nop,nop,TS val 1703170 ecr 280725383], length 6: FTP, length: 6
PASV
19:30:33.108869 IP (tos 0x0, ttl 64, id 21736, offset 0, flags [DF], proto TCP (6), length 100)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xc25c (correct), seq 356:404, ack 72, win 510, options [nop,nop,TS val 280725549 ecr 1703170], length 48: FTP, length: 48
227 Entering Passive Mode (10,0,0,100,33,253).
19:30:33.355226 IP (tos 0x0, ttl 47, id 8821, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10574 > 10.0.0.100.8701: Flags [S], cksum 0x8a54 (correct), seq 3520126822, win 65535, options [mss 1300,sackOK,TS val 1703187 ecr 0,nop,wscale 9], length 0
19:30:33.355645 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.8701 > 37.160.148.150.10574: Flags [S.], cksum 0xe430 (correct), seq 1672063330, ack 3520126823, win 65160, options [mss 1460,sackOK,TS val 280725796 ecr 1703187,nop,wscale 7], length 0
19:30:33.359544 IP (tos 0x0, ttl 47, id 17799, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x0ce0 (correct), ack 404, win 172, options [nop,nop,TS val 1703191 ecr 280725549], length 0
19:30:33.720806 IP (tos 0x0, ttl 47, id 8822, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10574 > 10.0.0.100.8701: Flags [.], cksum 0x10ad (correct), ack 1, win 172, options [nop,nop,TS val 1703232 ecr 280725796], length 0
19:30:33.726286 IP (tos 0x0, ttl 47, id 17800, offset 0, flags [DF], proto TCP (6), length 58)
37.160.148.150.10559 > 10.0.0.100.21: Flags [P.], cksum 0x6000 (correct), seq 72:78, ack 404, win 172, options [nop,nop,TS val 1703233 ecr 280725549], length 6: FTP, length: 6
LIST
19:30:33.727095 IP (tos 0x0, ttl 64, id 21737, offset 0, flags [DF], proto TCP (6), length 91)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0xf3a5 (correct), seq 404:443, ack 78, win 510, options [nop,nop,TS val 280726168 ecr 1703233], length 39: FTP, length: 39
150 Here comes the directory listing.
19:30:33.727099 IP (tos 0x8, ttl 64, id 18092, offset 0, flags [DF], proto TCP (6), length 244)
10.0.0.100.8701 > 37.160.148.150.10574: Flags [P.], cksum 0xc382 (correct), seq 1:193, ack 1, win 510, options [nop,nop,TS val 280726168 ecr 1703232], length 192
19:30:33.727104 IP (tos 0x8, ttl 64, id 18093, offset 0, flags [DF], proto TCP (6), length 52)
10.0.0.100.8701 > 37.160.148.150.10574: Flags [F.], cksum 0x0d26 (correct), seq 193, ack 1, win 510, options [nop,nop,TS val 280726168 ecr 1703232], length 0
19:30:33.835856 IP (tos 0x0, ttl 47, id 8823, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10574 > 10.0.0.100.8701: Flags [.], cksum 0x0e67 (correct), ack 193, win 174, options [nop,nop,TS val 1703248 ecr 280726168], length 0
19:30:33.840573 IP (tos 0x0, ttl 47, id 17801, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x0a0f (correct), ack 443, win 172, options [nop,nop,TS val 1703248 ecr 280726168], length 0
19:30:33.840598 IP (tos 0x0, ttl 47, id 8824, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10574 > 10.0.0.100.8701: Flags [F.], cksum 0x0e65 (correct), seq 1, ack 194, win 174, options [nop,nop,TS val 1703248 ecr 280726168], length 0
19:30:33.840972 IP (tos 0x8, ttl 64, id 18094, offset 0, flags [DF], proto TCP (6), length 52)
10.0.0.100.8701 > 37.160.148.150.10574: Flags [.], cksum 0x0ca4 (correct), ack 2, win 510, options [nop,nop,TS val 280726281 ecr 1703248], length 0
19:30:33.840978 IP (tos 0x0, ttl 64, id 21738, offset 0, flags [DF], proto TCP (6), length 76)
10.0.0.100.21 > 37.160.148.150.10559: Flags [P.], cksum 0x42b1 (correct), seq 443:467, ack 78, win 510, options [nop,nop,TS val 280726282 ecr 1703248], length 24: FTP, length: 24
226 Directory send OK.
19:30:33.960204 IP (tos 0x0, ttl 47, id 17802, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0x0979 (correct), ack 467, win 172, options [nop,nop,TS val 1703260 ecr 280726282], length 0
19:30:36.666271 IP (tos 0x0, ttl 47, id 17803, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [F.], cksum 0x086a (correct), seq 78, ack 467, win 172, options [nop,nop,TS val 1703530 ecr 280726282], length 0
19:30:36.666701 IP (tos 0x0, ttl 64, id 21739, offset 0, flags [DF], proto TCP (6), length 52)
10.0.0.100.21 > 37.160.148.150.10559: Flags [F.], cksum 0xfc0d (correct), seq 467, ack 79, win 510, options [nop,nop,TS val 280729107 ecr 1703530], length 0
19:30:36.806654 IP (tos 0x0, ttl 47, id 17804, offset 0, flags [DF], proto TCP (6), length 52)
37.160.148.150.10559 > 10.0.0.100.21: Flags [.], cksum 0xfd53 (correct), ack 468, win 172, options [nop,nop,TS val 1703542 ecr 280729107], length 0
^C
51 packets captured
51 packets received by filter
0 packets dropped by kernel
Before the connection the port is the 21, after the connection, became 8701, I understood well?
And this's with pbr on
root@OpenWrt:~# tcpdump -i eth1.1 -vn 'tcp portrange 20-21 or (tcp portrange 8000-9000 and host 10.0.0.100)'
tcpdump: listening on eth1.1, link-type EN10MB (Ethernet), capture size 262144 bytes
19:33:25.414414 IP (tos 0x0, ttl 47, id 63352, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10568 > 10.0.0.100.21: Flags [S], cksum 0x41c8 (correct), seq 541511851, win 65535, options [mss 1300,sackOK,TS val 1714131 ecr 0,nop,wscale 9], length 0
19:33:25.414910 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x3a4c (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280897857 ecr 1714131,nop,wscale 7], length 0
19:33:25.867484 IP (tos 0x0, ttl 47, id 63353, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10568 > 10.0.0.100.21: Flags [S], cksum 0x4163 (correct), seq 541511851, win 65535, options [mss 1300,sackOK,TS val 1714232 ecr 0,nop,wscale 9], length 0
19:33:25.867881 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x3887 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280898310 ecr 1714131,nop,wscale 7], length 0
19:33:26.892742 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x3486 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280899335 ecr 1714131,nop,wscale 7], length 0
19:33:27.785278 IP (tos 0x0, ttl 47, id 63354, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10568 > 10.0.0.100.21: Flags [S], cksum 0x409b (correct), seq 541511851, win 65535, options [mss 1300,sackOK,TS val 1714432 ecr 0,nop,wscale 9], length 0
19:33:27.785647 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x310a (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280900227 ecr 1714131,nop,wscale 7], length 0
19:33:29.804728 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x2926 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280902247 ecr 1714131,nop,wscale 7], length 0
19:33:31.789593 IP (tos 0x0, ttl 47, id 63355, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10568 > 10.0.0.100.21: Flags [S], cksum 0x3f0b (correct), seq 541511851, win 65535, options [mss 1300,sackOK,TS val 1714832 ecr 0,nop,wscale 9], length 0
19:33:31.789952 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x2165 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280904232 ecr 1714131,nop,wscale 7], length 0
19:33:36.044730 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x10c6 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280908487 ecr 1714131,nop,wscale 7], length 0
19:33:39.978330 IP (tos 0x0, ttl 47, id 63356, offset 0, flags [DF], proto TCP (6), length 60)
37.160.148.150.10568 > 10.0.0.100.21: Flags [S], cksum 0x3bdb (correct), seq 541511851, win 65535, options [mss 1300,sackOK,TS val 1715648 ecr 0,nop,wscale 9], length 0
19:33:39.978679 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 60)
10.0.0.100.21 > 37.160.148.150.10568: Flags [S.], cksum 0x0168 (correct), seq 178963354, ack 541511852, win 65160, options [mss 1460,sackOK,TS val 280912421 ecr 1714131,nop,wscale 7], length 0
^C
13 packets captured
13 packets received by filter
0 packets dropped by kernel
Like I always say, I'm really not expert, I only ask and try. Is possible that when I try to connect with pbr is on, the packets arrive to 10.0.0.100:21, but then are not returned via normal port but via pia? So don't use the same route when came in and out?
J
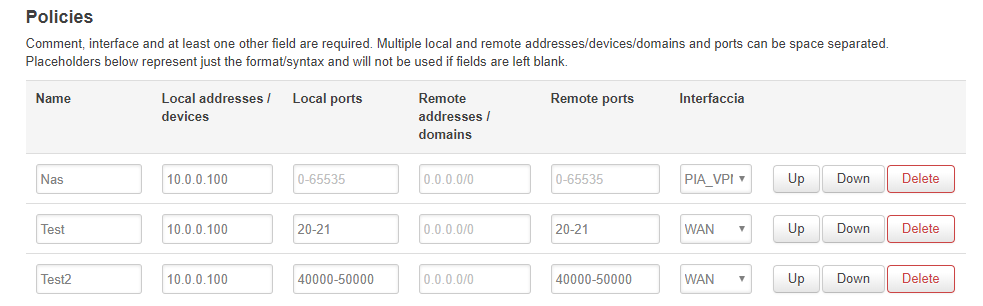
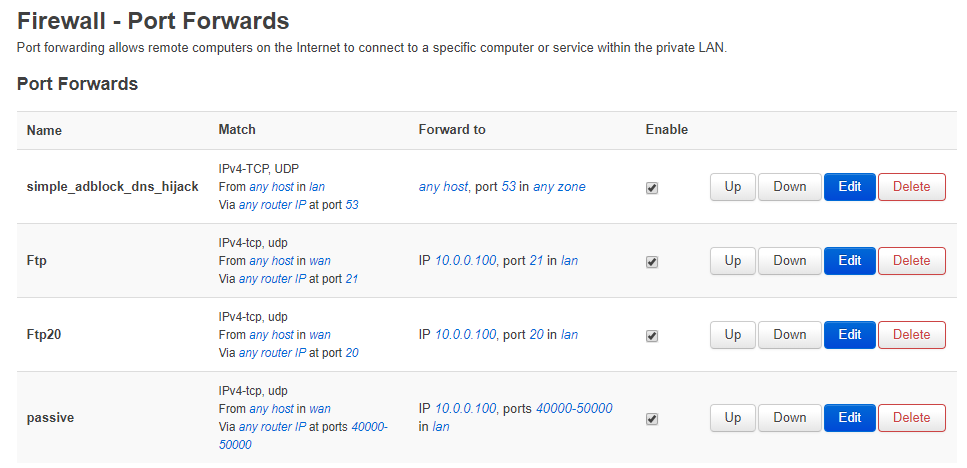
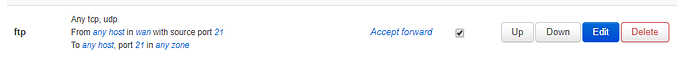
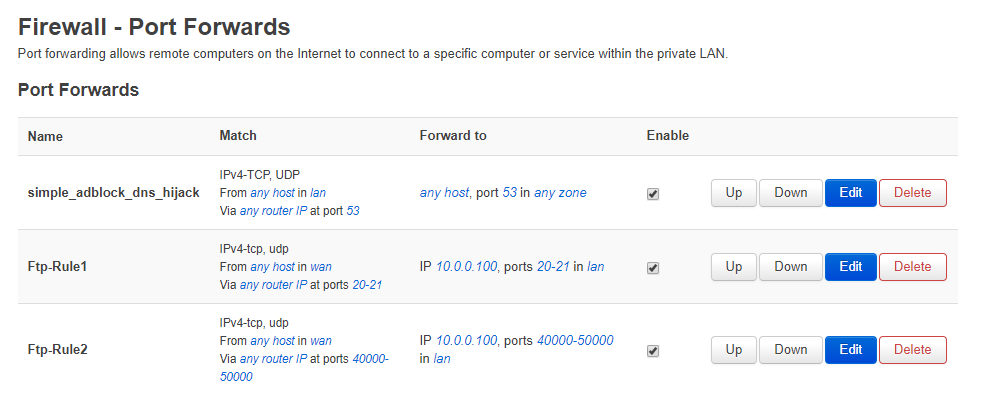
 Like I said network is very complicated for me, I've only very little knowledge.
Like I said network is very complicated for me, I've only very little knowledge.