meazz1
December 6, 2020, 11:37pm
1
I have installed and setup my basic configurations as followa;
/etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:0d16:e967::/48'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
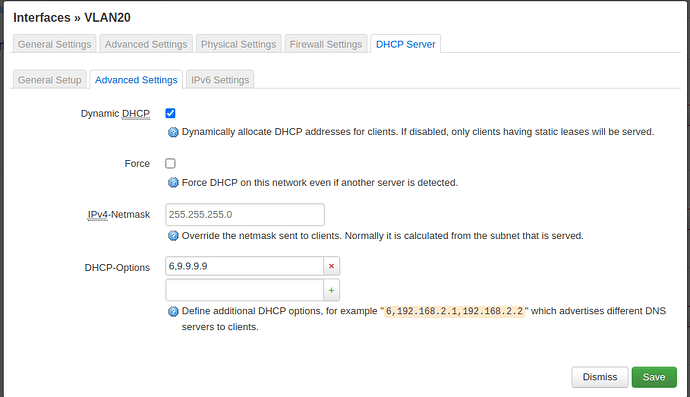
list dns '6,9.9.9.9'
option type 'bridge'
option ifname 'eth0.1'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
config interface 'VLAN20'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.20.1'
option ip6assign '64'
list dns '9.9.9.9'
list dns '1.1.1.1'
option type 'bridge'
option ifname 'eth0.20'
mikma
December 7, 2020, 12:20am
2
What isn't working?
Those DNS server probably should not be configured that way on that interface
Use a DHCP option like on the LAN interface.
Or configure the DNS servers on the WAN interface instead since that's the interface the IP addresses are routed via.
1 Like
meazz1
December 7, 2020, 12:52am
3
Any suggestion how to isolate the VLAN from LAN?
Assign the network you want to isolate to separate firewall zone.
trendy
December 7, 2020, 12:07pm
5
meazz1:
list dns '6,9.9.9.9'
Delete the dns entries from lan and VLAN20 and add them in wan, where they are reachable from. Moreover this syntax is wrong. The 6, is for dhcp server options.
1 Like
meazz1
December 7, 2020, 2:39pm
6
Ok, so I will remove them from LAN/
VLAN dhcp below but not seeing anywhere in WAN to enter them.
Can help?
mk24
December 7, 2020, 2:57pm
7
In the WAN advanced settings, uncheck "Use DNS servers advertised by peer" and a box to enter a custom DNS server will appear. Click + to create another box for more than one server.
This causes the internal DNS server running on both lan and vlan20 to consult the servers you specify for an unknown / uncached name request, instead of the ISP default.
To advise clients to go directly to a certain server, enter that as a DHCP option on their network, but realize that the client is still free to use a different one.
1 Like
meazz1
December 8, 2020, 12:31am
8
For the life of me I can't get the VLAN and LAN firewall rules to work. I don't want VLAN to access anything in lan segment.
/etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
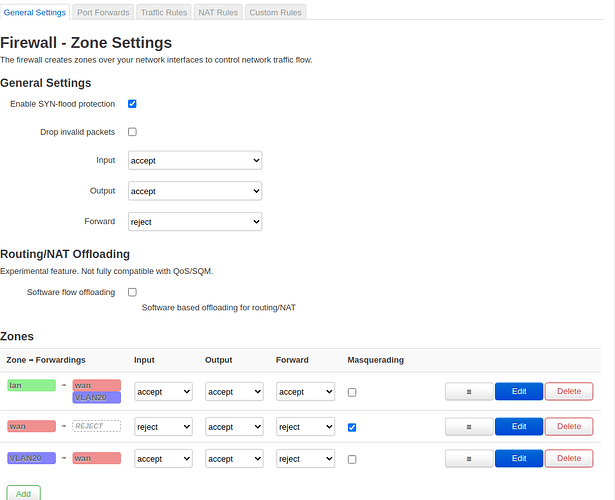
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
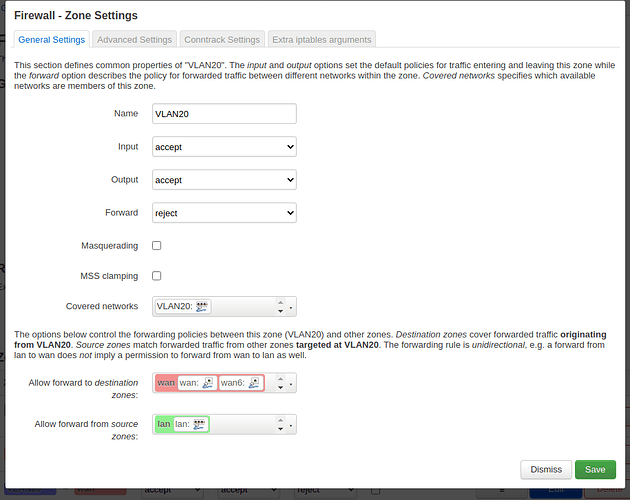
config zone
option name 'VLAN20'
option input 'ACCEPT'
option output 'ACCEPT'
option network 'VLAN20'
option forward 'REJECT'
config forwarding
option dest 'wan'
option src 'VLAN20'
config forwarding
option dest 'wan'
option src 'lan'
config redirect
option dest_port '51820'
option src 'wan'
option name 'WG VPN'
option src_dport '51820'
option target 'DNAT'
option dest_ip '192.168.4.8'
option dest 'lan'
list proto 'udp'
config forwarding
option dest 'VLAN20'
option src 'lan'
/etc/config/network
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdda:0d16:e967::/48'
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
option ifname 'eth0.1'
config interface 'wan'
option ifname 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '9.9.9.9'
list dns '208.67.222.123'
config interface 'wan6'
option ifname 'eth1'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'try'
option peerdns '0'
list dns '9.9.9.9'
list dns '208.67.222.123'
config interface 'VLAN20'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '10.0.20.1'
option ip6assign '64'
option type 'bridge'
option ifname 'eth0.20'
type or paste code here
trendy
December 8, 2020, 9:15am
9
Your config looks correct.
Are you certain there is no loop with the bridged interfaces? If you are not bridging them to some wifi SSIDs you can disable bridging.
Are you sure that the switch is properly configured and not acting up? Both vlans 1 and 20 must be tagged and don't allow untagged frames.
meazz1
December 8, 2020, 12:40pm
10
I'm not bridging with any wifif. My unifi ac-lite is on a unifi poe switch port .
config interface 'lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
option ifname 'eth0.1'
option stp 1
trendy
December 8, 2020, 2:06pm
11
I think it's best to remove both stp and type bridge.
1 Like
meazz1
December 9, 2020, 1:35am
12
For the life of me I can't get thos to work. I just need VLAN20 not able to see any LAN devices including the router.
trendy
December 9, 2020, 6:50am
13
Change the zone input to reject. But then you'll need to allow things like dns and dhcp, if they are used.
meazz1
December 9, 2020, 12:48pm
14
Thanks, That's what was missing, a firewall rules for DNS and DHCP. It's all good now.
trendy
December 9, 2020, 12:51pm
15
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
system
December 19, 2020, 12:51pm
16
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.