Hello OpenWrt community,
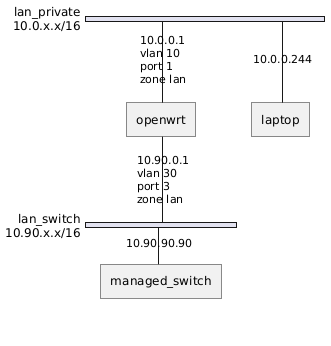
I am new to OpenWrt and have some issues implementing what I think should be a simple setup (see attached image).
I started from a vanilla installation and did very few configuration (as far a I can tell)
I think I got the vlans correctly setup. All networks are currently in the same firewall zone to simplify things.
I want to be able to reach the switch (in network 10.90) from the laptop (in network 10.0). But, currently from the laptop I cannot ping anything on the 10.90.x.x network (I tried 10.90.0.1 and 10.90.90.90).
From ssh on the openwrt router, I can ping both the switch and the laptop.
I am wondering if it is possible to do this, and what configuration am I missing.
Thanks in advance for your help
uci export network
package network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd57:3052:3b0e::/48'
option packet_steering '1'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
list ports 'lan4'
list ports 'lan5'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
config bridge-vlan
option device 'br-lan'
option vlan '10'
list ports 'lan1:u*'
config bridge-vlan
option device 'br-lan'
option vlan '20'
list ports 'lan2:u*'
config bridge-vlan
option device 'br-lan'
option vlan '30'
list ports 'lan3:u*'
config bridge-vlan
option device 'br-lan'
option vlan '40'
list ports 'lan4:u*'
config bridge-vlan
option device 'br-lan'
option vlan '50'
list ports 'lan5:u*'
config interface 'lan_private'
option proto 'static'
option device 'br-lan.10'
option ipaddr '10.0.0.1'
option netmask '255.255.0.0'
config interface 'lan_switch'
option proto 'static'
option device 'br-lan.30'
option ipaddr '10.90.0.1'
option netmask '255.255.0.0'
uci export dhcp
package dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option filterwin2k '0'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option nonegcache '0'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option ednspacket_max '1232'
option filter_aaaa '0'
option filter_a '0'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'lan_private'
option interface 'lan_private'
option start '100'
option limit '150'
option leasetime '12h'
config dhcp 'lan_switch'
option interface 'lan_switch'
option start '100'
option limit '150'
option leasetime '12h'
uci export firewall
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan_private'
list network 'lan_switch'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'