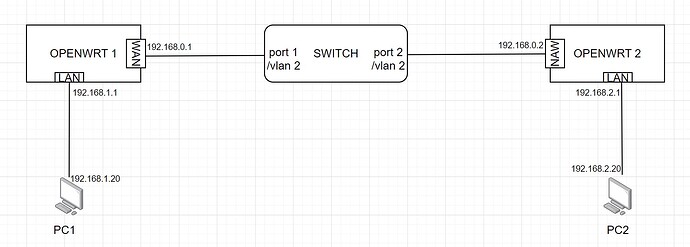
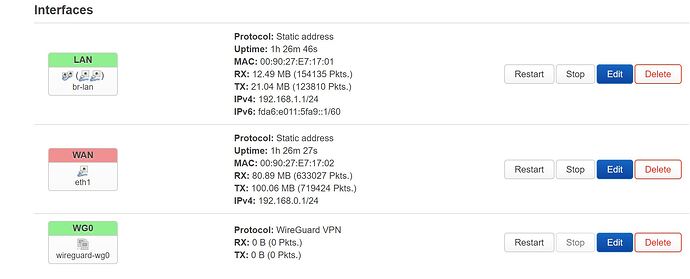
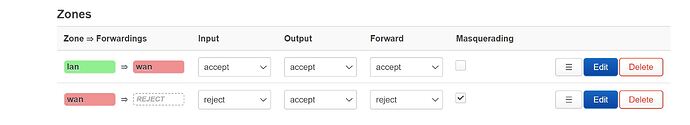
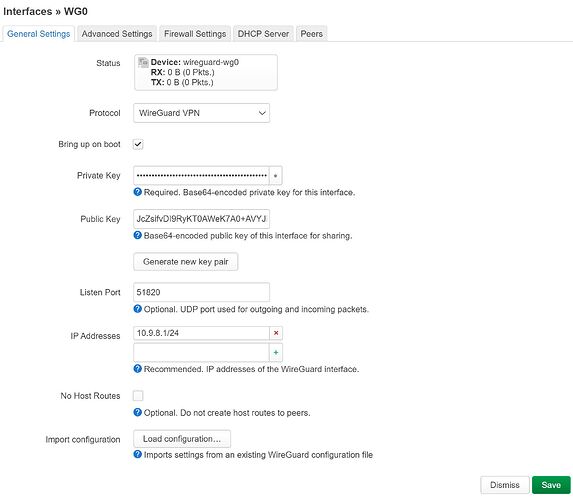
As shown in the topology diagram, the following is my configuration on OpenWrt. WireGuard seems to work normally, but no traffic rules are configured, and WireGuard packets cannot be captured.
For example, on PC1:
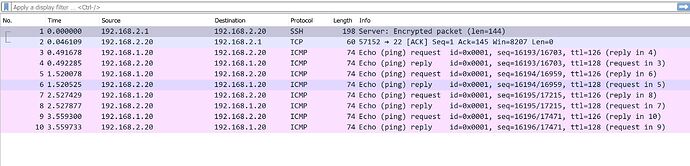
I can ping/trace 192.168.2.20 (PC2) as shown below. Once I typed "ifdown wg0", I cannot ping/trace it anymore. This seems to prove that the WireGuard tunnel is working.
>tracert 192.168.2.20
1 1 ms * * OpenWrt_A_LocalSide.lan [192.168.1.1]
2 1 ms 1 ms 1 ms 10.9.8.2
3 2 ms 1 ms 2 ms LOANERLAPTOP-SC [192.168.2.20]
At this point, there are only icmp packet , no WireGuard packets on its peer (OpenWrt 2)
After ’ifdown wg0‘
>tracert 192.168.2.20
1 * * OpenWrt_A_LocalSide.lan [192.168.1.1] reports: Destination net unreachable.
Openwrt 1's info.
# wg
interface: wg0
public key: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
private key: (hidden)
listening port: 51820
peer: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
endpoint: 192.168.0.2:51820
allowed ips: 10.9.8.2/32, 192.168.2.0/24
latest handshake: 33 seconds ago
transfer: 197.39 KiB received, 168.29 KiB sent
persistent keepalive: every 25 seconds
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.9.8.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
10.9.8.2 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
192.168.0.0 0.0.0.0 255.255.255.0 U 10 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
# ip route get 192.168.2.20
192.168.2.20 dev wg0 src 10.9.8.1
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.1/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1702/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:90:27:e7:17:03 brd ff:ff:ff:ff:ff:ff
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:90:27:e7:17:04 brd ff:ff:ff:ff:ff:ff
6: eth4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq master br-lan state DOWN qlen 1000
link/ether 00:90:27:e7:17:05 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:90:27:e7:17:06 brd ff:ff:ff:ff:ff:ff
43: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fda6:e011:5fa9::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1701/64 scope link
valid_lft forever preferred_lft forever
47: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.1/24 brd 10.9.8.255 scope global wg0
valid_lft forever preferred_lft forever
Openwrt 2's info.
# wg
interface: wg0
public key: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
private key: (hidden)
listening port: 51820
peer: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
endpoint: 192.168.0.1:51820
allowed ips: 10.9.8.1/32, 192.168.1.0/24
latest handshake: 8 seconds ago
transfer: 119.45 KiB received, 163.67 KiB sent
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth1
10.9.8.1 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
# ip route get 192.168.1.20
192.168.1.20 dev wg0 src 10.9.8.2
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:25 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.2/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da25/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:26 brd ff:ff:ff:ff:ff:ff
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:27 brd ff:ff:ff:ff:ff:ff
6: eth4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:28 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:29 brd ff:ff:ff:ff:ff:ff
21: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd15:619b:2d98::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da24/64 scope link
valid_lft forever preferred_lft forever
27: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.2/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
Openwrt 1's Configuratin
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda6:e011:5fa9::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option metric '10'
option ipaddr '192.168.0.1'
config interface 'wg0'
option proto 'wireguard'
option private_key 'GGv/4oUSIBdkUpt6231o/QObwtZ4Rpio9Kbh/Mm/c38='
option listen_port '51820'
option defaultroute '0'
list addresses '10.9.8.1/24'
config wireguard_wg0
option public_key '0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw='
option route_allowed_ips '1'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.9.8.2/32'
list allowed_ips '192.168.2.0/24'
option endpoint_host '192.168.0.2'
config device
option name 'eth3'
option acceptlocal '1'
******************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Openwrt 2's Configuratin
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:619b:2d98::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.2'
config interface 'wg0'
option proto 'wireguard'
option private_key 'YEtZJtUPjmzEYa80tMbVSZdPWG7gge92ZnU2kpkd7WQ='
option listen_port '51820'
list addresses '10.9.8.2/32'
config wireguard_wg0
option public_key 'JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng='
list allowed_ips '10.9.8.1/32'
list allowed_ips '192.168.1.0/24'
option route_allowed_ips '1'
option endpoint_host '192.168.0.1'
option endpoint_port '51820'
******************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'