Check the windows firewall. There is a high probability that the problem is there. By default, Windows firewall will not accept connections from a different subnet. You need to modify the firewall to allow this. The simple way to test this is to simply turn off the windows firewall and run the test.
Thank you for reminding me. I can confirm that the firewall has been shut down on both PCs. During today's testing, there was some progress. I discovered that I had mistakenly created a gateway with the IP address of 6.6.6.1 on the switch. Although I did not use this network for testing, the gateway was included in the LAN zone on the firewall, which can caused some issues.
PC_A(192.168.8.20) at the Remote Side:
>tracert 192.168.1.1
1 <1 ms <1 ms <1 ms OpenWrt_B_RemoteSide.lan [192.168.8.1]
2 1 ms 1 ms 1 ms 192.168.1.1
>tracert 192.168.1.20
1 <1 ms <1 ms <1 ms OpenWrt_B_RemoteSide.lan [192.168.8.1]
2 1 ms 1 ms <1 ms 192.168.100.1
3 1 ms 1 ms 1 ms LOANERLAPTOP-SC [192.168.1.20]
Remote Side's Openwrt:
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 7.7.7.1 0.0.0.0 UG 0 0 0 eth1
6.6.6.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
7.7.7.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
8.8.8.2 7.7.7.1 255.255.255.255 UGH 0 0 0 eth1
8.8.8.8 7.7.7.1 255.255.255.255 UGH 0 0 0 eth1
10.10.10.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.8.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
# ip route
default via 7.7.7.1 dev eth1
6.6.6.0/24 dev eth2 scope link src 6.6.6.8
7.7.7.0/24 dev eth1 scope link src 7.7.7.8
8.8.8.2 via 7.7.7.1 dev eth1
8.8.8.8 via 7.7.7.1 dev eth1
10.10.10.0/24 dev wg0 scope link
192.168.1.0/24 dev wg0 scope link
192.168.8.0/24 dev br-lan scope link src 192.168.8.1
192.168.100.0/24 dev wg0 scope link
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:25 brd ff:ff:ff:ff:ff:ff
inet 7.7.7.8/24 brd 7.7.7.255 scope global eth1
valid_lft forever preferred_lft forever
inet 7.7.7.2/24 scope global secondary eth1
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da25/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:26 brd ff:ff:ff:ff:ff:ff
inet 6.6.6.8/24 brd 6.6.6.255 scope global eth2
valid_lft forever preferred_lft forever
inet 6.6.6.2/24 scope global secondary eth2
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da26/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:27 brd ff:ff:ff:ff:ff:ff
6: eth4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:28 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:29 brd ff:ff:ff:ff:ff:ff
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
inet 192.168.8.1/24 brd 192.168.8.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd15:619b:2d98::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da24/64 scope link
valid_lft forever preferred_lft forever
13: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 192.168.100.2/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:619b:2d98::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.8.1'
config interface 'wan'
option device 'eth1'
option proto 'static'
option ipaddr '7.7.7.8'
option netmask '255.255.255.0'
option gateway '7.7.7.1'
config interface 'lanb'
option proto 'static'
option device 'eth2'
option ipaddr '6.6.6.8'
option netmask '255.255.255.0'
config interface 'wg0'
option proto 'wireguard'
option private_key 'YEtZJtUPjmzEYa80tMbVSZdPWG7gge92ZnU2kpkd7WQ='
option listen_port '51820'
list addresses '192.168.100.2'
option defaultroute '0'
config wireguard_wg0
option public_key 'JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng='
list allowed_ips '192.168.100.0/24'
list allowed_ips '192.168.1.0/24'
list allowed_ips '10.10.10.0/24'
option route_allowed_ips '1'
option endpoint_port '51820'
option persistent_keepalive '25'
option endpoint_host '8.8.8.8'
************************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lanb'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'wg0'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
PC_B(192.168.1.20) at the Local Side:
>tracert 192.168.8.1
1 <1 ms <1 ms <1 ms OpenWrt_A_LocalSide.lan [192.168.1.1]
2 1 ms <1 ms 1 ms 192.168.8.1
>tracert 192.168.8.20
1 <1 ms <1 ms <1 ms OpenWrt_A_LocalSide.lan [192.168.1.1]
2 1 ms 1 ms 1 ms 192.168.100.2
3 1 ms 1 ms 1 ms SHUANG2-SC01 [192.168.8.20]
Local Side's Openwrt:
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 8.8.8.1 0.0.0.0 UG 10 0 0 eth1
0.0.0.0 9.9.9.1 0.0.0.0 UG 20 0 0 eth2
6.6.6.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
8.8.8.0 0.0.0.0 255.255.255.0 U 10 0 0 eth1
9.9.9.0 0.0.0.0 255.255.255.0 U 20 0 0 eth2
10.10.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth3
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.8.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.100.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
# ip route
default via 8.8.8.1 dev eth1 metric 10
default via 9.9.9.1 dev eth2 metric 20
6.6.6.0/24 dev wg0 scope link
8.8.8.0/24 dev eth1 scope link metric 10
9.9.9.0/24 dev eth2 scope link metric 20
10.10.10.0/24 dev eth3 scope link src 10.10.10.8
192.168.1.0/24 dev br-lan scope link src 192.168.1.1
192.168.8.0/24 dev wg0 scope link
192.168.100.0/24 dev wg0 scope link
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:02 brd ff:ff:ff:ff:ff:ff
inet 8.8.8.8/24 brd 8.8.8.255 scope global eth1
valid_lft forever preferred_lft forever
inet 8.8.8.2/24 scope global secondary eth1
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1702/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:03 brd ff:ff:ff:ff:ff:ff
inet 9.9.9.8/24 brd 9.9.9.255 scope global eth2
valid_lft forever preferred_lft forever
inet 9.9.9.2/24 scope global secondary eth2
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1703/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:04 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.8/24 brd 10.10.10.255 scope global eth3
valid_lft forever preferred_lft forever
inet 10.10.10.2/24 scope global secondary eth3
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1704/64 scope link
valid_lft forever preferred_lft forever
6: eth4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq master br-lan state DOWN qlen 1000
link/ether 00:90:27:e7:17:05 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:90:27:e7:17:06 brd ff:ff:ff:ff:ff:ff
8: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fda6:e011:5fa9::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1701/64 scope link
valid_lft forever preferred_lft forever
14: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 192.168.100.1/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda6:e011:5fa9::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'static'
option ipaddr '8.8.8.8'
option netmask '255.255.255.0'
option gateway '8.8.8.1'
option metric '10'
config interface 'wanb'
option proto 'static'
option device 'eth2'
option ipaddr '9.9.9.8'
option netmask '255.255.255.0'
option gateway '9.9.9.1'
option metric '20'
config interface 'lanb'
option proto 'static'
option device 'eth3'
option ipaddr '10.10.10.8'
option netmask '255.255.255.0'
option gateway '8.8.8.1'
config interface 'wg0'
option proto 'wireguard'
option private_key 'GGv/4oUSIBdkUpt6231o/QObwtZ4Rpio9Kbh/Mm/c38='
option listen_port '51820'
list addresses '192.168.100.1'
option defaultroute '0'
config wireguard_wg0
option public_key '0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw='
option route_allowed_ips '1'
option endpoint_port '51820'
list allowed_ips '192.168.100.0/24'
list allowed_ips '192.168.8.0/24'
list allowed_ips '6.6.6.0/24'
option endpoint_host '7.7.7.8'
option persistent_keepalive '25'
config device
option name 'eth3'
option acceptlocal '1'
************************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lanb'
list network 'wg0'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
list network 'wan'
list network 'wanb'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'wg0'
list proto 'udp'
option src 'wan'
option dest_port '51820'
option target 'ACCEPT'
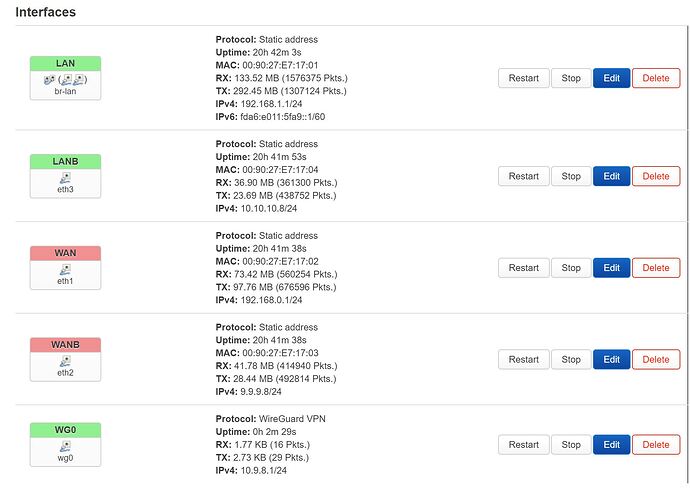
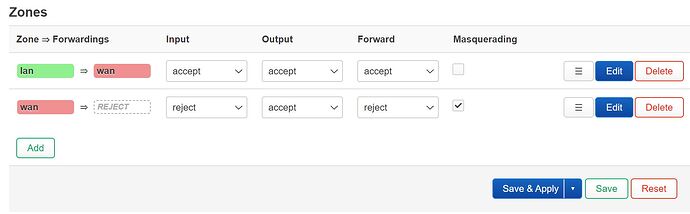
At the moment, both PCs on either side can ping each other successfully (192.168.8.20 --- 192.168.1.20). However, I am still not completely certain if this is correct. The firewall configurations is same as yesterday
I've been trying to capture Wireguard packets on both OpenWrt devices, but I haven't seen any Wireguard packets at all, which is strange.
I used the command 'tcpdump -w /etc/keepalived/21.cap' to capture packets. However, whenever I run the 'ifdown wg0' command, the ping between 192.168.8.20 and 192.168.1.20 is interrupted. The switch only has routing between the WANs. There's no routing between the LANs (6.6.6.0/24, 10.10.10.0/24, 192.168.1.0/24, and 192.168.8.0/24) on both sides, and LAN traffic is supposed to go through the wg0 interface.
I think that your setup is fundamentally working now. But you're actually overcomplicating everything by a large margin.
This can be done with two routers connected to each other, no additional routing needed, no switch (L2 or L3) either. And instead of using what are normally public IP address schemes, use RFC1918 address ranges instead.
Here's what I would suggest for a simpler, but very conclusive setup:
Router 1:
- wan address - static 192.168.0.1/24
- wan zone: masquerading enabled, input = drop or reject
- lan address: 192.168.1.1/24
- lan zone: masquerading disabled, input = accept, forward = accept
- lan > wan forwarding allowed on the firewall
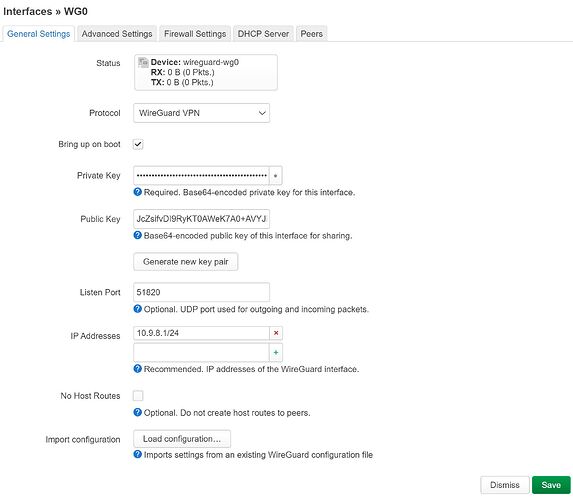
- wg as a 'server' with interface address 10.9.8.1/24
- wg peer with allowed IPs 10.9.8.2/32, 192.168.2.0/24
- wg either in lan zone or in its own zone (if in its own zone, masquerading disabled, input = accept, lan > wg and wg > lan forwarding allowed)
- firewall traffic rule accept the listen port for wg
Router 2:
- wan address - static 192.168.0.2/24
- wan zone: masquerading enabled, input = drop or reject
- lan address: 192.168.2.1/24
- lan zone: masquerading disabled, input = accept, forward = accept
- lan > wan forwarding allowed on the firewall
- wg as a 'client' with interface address 10.9.8.2/32
- wg peer with allowed IPs 10.9.8.1/32, 192.168.1.0/24
- wg either in lan zone or in its own zone (if in its own zone, masquerading disabled, input = accept, lan > wg and wg > lan forwarding allowed)
Then, with WG not started, try to ping from a host on one router to hosts on the other (including the lan address of the other router).... they will fail. Activate WG (make sure it has connected -- you can check the last handshake time), and try the ping tests again. They will suceed (provided that there are no local firewalls on the hosts that would prevent it).
Your setup with additional routing on your L3 capable switch is not necessary or relevant to OpenWrt + WG because the behavior will be the same regardless if the 2 routers have their wans on the same subnet or on totally different and unrelated subnets across the world.
Thank you so much for your help. I will testing it and provide you with feedback as soon as possible.
Thank you very much. I was indeed overcomplicating things, because my entire topology is a little complex.
Following your advice, The WAN ports of these two OpenWrt are directly connected. I completed the testing and everything seems to be fine. Initially, when WG was not started, the ping test failed. However, after activating WG and retesting, it was successful.
I have a few small questions:
- As shown below, on Router1: I can ping the physical LAN interface (192.168.2.1) of Route2. It seems that WireGuard is not necessary, because I don't see the second hop address 10.9.8.2. However, when pinging a testing PC, such as 192.168.2.20, it seems to go through WireGuard because I can see that its second hop is 10.9.8.2.
>tracert 192.168.2.1
1 <1 ms <1 ms <1 ms OpenWrt_A_LocalSide.lan [192.168.1.1]
2 <1 ms <1 ms <1 ms 192.168.2.1
>tracert 192.168.2.20
1 <1 ms <1 ms <1 ms OpenWrt_A_LocalSide.lan [192.168.1.1]
2 1 ms 1 ms 1 ms 10.9.8.2
3 1 ms 1 ms 1 ms LOANERLAPTOP-SC [192.168.2.20]
-
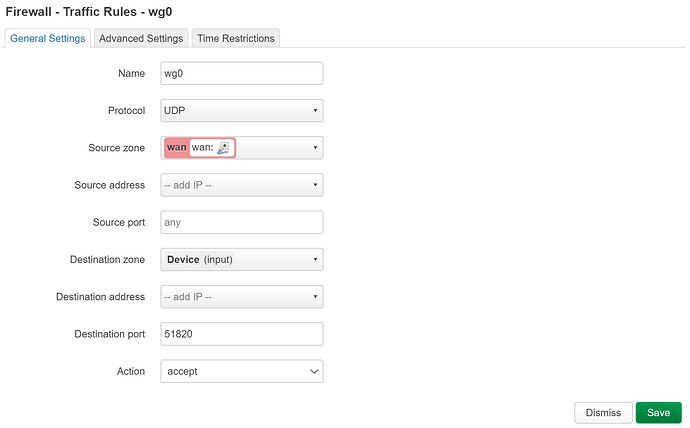
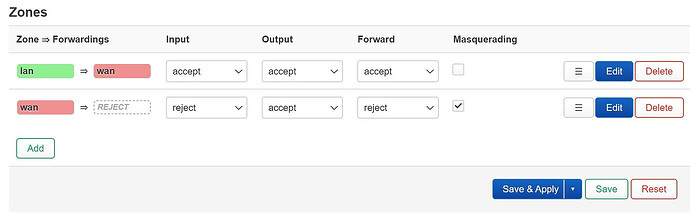
At the beginning, I created a traffic rule as shown below and tested that everything was working fine. However, when I deleted this traffic rule, WireGuard VPN still seemed to be working because I could still ping each other.
-
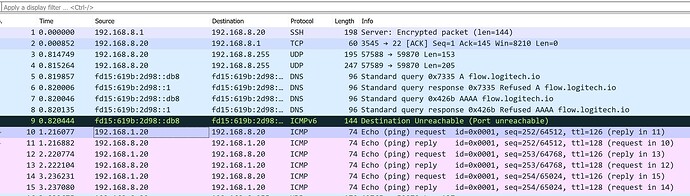
I tried to ping from Router 1 and captured the packets on Router 2, but did not find any WireGuard packets.
Router 1's configuration
# wg
interface: wg0
public key: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
private key: (hidden)
listening port: 51820
peer: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
endpoint: 192.168.0.2:51820
allowed ips: 10.9.8.2/32, 192.168.2.0/24
latest handshake: 42 seconds ago
transfer: 4.73 KiB received, 7.05 KiB sent
persistent keepalive: every 25 seconds
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.2 0.0.0.0 UG 0 0 0 eth1
0.0.0.0 9.9.9.1 0.0.0.0 UG 20 0 0 eth2
9.9.9.0 0.0.0.0 255.255.255.0 U 20 0 0 eth2
10.9.8.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
10.9.8.2 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
10.10.10.0 0.0.0.0 255.255.255.0 U 0 0 0 eth3
192.168.0.0 0.0.0.0 255.255.255.0 U 10 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.1/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1702/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:03 brd ff:ff:ff:ff:ff:ff
inet 9.9.9.8/24 brd 9.9.9.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1703/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:04 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.8/24 brd 10.10.10.255 scope global eth3
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1704/64 scope link
valid_lft forever preferred_lft forever
6: eth4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq master br-lan state DOWN qlen 1000
link/ether 00:90:27:e7:17:05 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:90:27:e7:17:06 brd ff:ff:ff:ff:ff:ff
19: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fda6:e011:5fa9::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1701/64 scope link
valid_lft forever preferred_lft forever
28: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.1/24 brd 10.9.8.255 scope global wg0
valid_lft forever preferred_lft forever
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda6:e011:5fa9::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option metric '10'
option ipaddr '192.168.0.1'
config interface 'wanb'
option proto 'static'
option device 'eth2'
option ipaddr '9.9.9.8'
option netmask '255.255.255.0'
option gateway '9.9.9.1'
option metric '20'
config interface 'lanb'
option proto 'static'
option device 'eth3'
option ipaddr '10.10.10.8'
option netmask '255.255.255.0'
option gateway '8.8.8.1'
config interface 'wg0'
option proto 'wireguard'
option private_key 'GGv/4oUSIBdkUpt6231o/QObwtZ4Rpio9Kbh/Mm/c38='
option listen_port '51820'
option defaultroute '0'
list addresses '10.9.8.1/24'
config wireguard_wg0
option public_key '0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw='
option route_allowed_ips '1'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.9.8.2/32'
list allowed_ips '192.168.2.0/24'
option endpoint_host '192.168.0.2'
config device
option name 'eth3'
option acceptlocal '1'
**********************************
cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lanb'
list network 'wg0'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
list network 'wan'
list network 'wanb'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Router 2's configuration
# wg
interface: wg0
public key: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
private key: (hidden)
listening port: 51820
peer: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
endpoint: 192.168.0.1:51820
allowed ips: 10.9.8.1/32, 192.168.1.0/24
latest handshake: 1 minute, 37 seconds ago
transfer: 6.91 KiB received, 1.89 KiB sent
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth1
6.6.6.0 0.0.0.0 255.255.255.0 U 0 0 0 eth2
10.9.8.1 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:25 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.2/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da25/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:26 brd ff:ff:ff:ff:ff:ff
inet 6.6.6.8/24 brd 6.6.6.255 scope global eth2
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da26/64 scope link
valid_lft forever preferred_lft forever
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:27 brd ff:ff:ff:ff:ff:ff
6: eth4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:28 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:29 brd ff:ff:ff:ff:ff:ff
9: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd15:619b:2d98::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da24/64 scope link
valid_lft forever preferred_lft forever
14: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.2/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:619b:2d98::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.2'
config interface 'lanb'
option proto 'static'
option device 'eth2'
option ipaddr '6.6.6.8'
option netmask '255.255.255.0'
config interface 'wg0'
option proto 'wireguard'
option private_key 'YEtZJtUPjmzEYa80tMbVSZdPWG7gge92ZnU2kpkd7WQ='
option listen_port '51820'
list addresses '10.9.8.2/32'
config wireguard_wg0
option public_key 'JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng='
list allowed_ips '10.9.8.1/32'
list allowed_ips '192.168.1.0/24'
option route_allowed_ips '1'
option endpoint_host '192.168.0.1'
option endpoint_port '51820'
**********************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'lanb'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
This is because you've got the wg0 network associated with the lan zone which has input = accept. Basically, the router itself recognizes that 192.168.2.1 belongs to itself, so it can reply directly without having to do any routing.
WG is most certainly necessary -- if you stop the WG interface, you will not be able to ping the router's lan address from the other router.
The traffic rule is necessary on the router that is 'listening' for an inbound connection. It is not necessary for the other router (which is initiating the connection).
Were you capturing UDP packets on the wan? You'll only see WG packets passing between the two wan ports.
After deleting the traffic rules, I even restarted /etc/init.d/firewall, but both sides can still ping each other. As for packet capture, I was on Router1 and pinged Router2. On Router2, to capture the all inbound packets, I used the command "tcpdump -w /etc/keepalived/capture_all.cap".
I think maybe these are not problems, but rather my testing method is incorrect. I will test again.
Did you stop and try to restart the WG connection after deleting the traffic rules?
no,perhaps this is the reason. I will test again,Thanks!!
Hi Psherman,
Today, I've done more testing, but things still seem strange. I did restart the WG connection on both side, but I still can't capture WireGuard packets, and it works even without traffic rule.
The Post is getting too long, I am trying to create a new post to explain the problem in more detail since this one is getting lengthy
I'm not an expert on this part, so I can't help here... but...
This shouldn't be the case. We should review the latest configs (just the network and firewall files) on each device.
Let's keep things in this thread. Creating another thread will only make things more confusing and may end up bifurcating the conversation and solutions.
Thanks a lot, I just saw your reply. I can put the new post (Unable to capture WireGuard packets) in this thread.
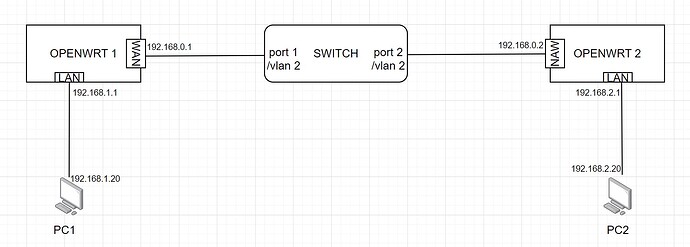
As shown in the topology diagram, the following is my configuration on OpenWrt. WireGuard seems to work normally, but no traffic rules are configured, and WireGuard packets cannot be captured.
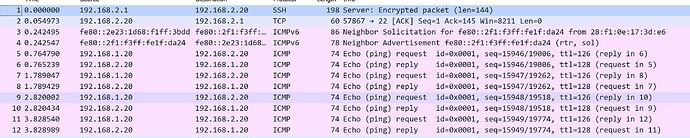
For example, on PC1 :
I can ping/trace 192.168.2.20 (PC2) as shown below. Once I typed "ifdown wg0", I cannot ping/trace it anymore. This seems to prove that the WireGuard tunnel is working.
>tracert 192.168.2.20
1 1 ms * * OpenWrt_A_LocalSide.lan [192.168.1.1]
2 1 ms 1 ms 1 ms 10.9.8.2
3 2 ms 1 ms 2 ms LOANERLAPTOP-SC [192.168.2.20]
At this point, there are only icmp packet , no WireGuard packets on its peer (OpenWrt 2)
After ’ifdown wg0‘
>tracert 192.168.2.20
1 * * OpenWrt_A_LocalSide.lan [192.168.1.1] reports: Destination net unreachable.
Openwrt 1's info.
# wg
interface: wg0
public key: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
private key: (hidden)
listening port: 51820
peer: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
endpoint: 192.168.0.2:51820
allowed ips: 10.9.8.2/32, 192.168.2.0/24
latest handshake: 33 seconds ago
transfer: 197.39 KiB received, 168.29 KiB sent
persistent keepalive: every 25 seconds
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
10.9.8.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
10.9.8.2 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
192.168.0.0 0.0.0.0 255.255.255.0 U 10 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
# ip route get 192.168.2.20
192.168.2.20 dev wg0 src 10.9.8.1
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:90:27:e7:17:02 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.1/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1702/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:90:27:e7:17:03 brd ff:ff:ff:ff:ff:ff
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:90:27:e7:17:04 brd ff:ff:ff:ff:ff:ff
6: eth4: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc mq master br-lan state DOWN qlen 1000
link/ether 00:90:27:e7:17:05 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:90:27:e7:17:06 brd ff:ff:ff:ff:ff:ff
43: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:90:27:e7:17:01 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.1/24 brd 192.168.1.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fda6:e011:5fa9::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::290:27ff:fee7:1701/64 scope link
valid_lft forever preferred_lft forever
47: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.1/24 brd 10.9.8.255 scope global wg0
valid_lft forever preferred_lft forever
Openwrt 2's info.
# wg
interface: wg0
public key: 0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw=
private key: (hidden)
listening port: 51820
peer: JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng=
endpoint: 192.168.0.1:51820
allowed ips: 10.9.8.1/32, 192.168.1.0/24
latest handshake: 8 seconds ago
transfer: 119.45 KiB received, 163.67 KiB sent
# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.0.1 0.0.0.0 UG 0 0 0 eth1
10.9.8.1 0.0.0.0 255.255.255.255 UH 0 0 0 wg0
192.168.0.0 0.0.0.0 255.255.255.0 U 0 0 0 eth1
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 wg0
192.168.2.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
# ip route get 192.168.1.20
192.168.1.20 dev wg0 src 10.9.8.2
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq master br-lan state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
link/ether 00:f1:f3:1f:da:25 brd ff:ff:ff:ff:ff:ff
inet 192.168.0.2/24 brd 192.168.0.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da25/64 scope link
valid_lft forever preferred_lft forever
4: eth2: <BROADCAST,MULTICAST> mtu 1500 qdisc mq state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:26 brd ff:ff:ff:ff:ff:ff
5: eth3: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:27 brd ff:ff:ff:ff:ff:ff
6: eth4: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:28 brd ff:ff:ff:ff:ff:ff
7: eth5: <BROADCAST,MULTICAST> mtu 1500 qdisc noop state DOWN qlen 1000
link/ether 00:f1:f3:1f:da:29 brd ff:ff:ff:ff:ff:ff
21: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 00:f1:f3:1f:da:24 brd ff:ff:ff:ff:ff:ff
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd15:619b:2d98::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::2f1:f3ff:fe1f:da24/64 scope link
valid_lft forever preferred_lft forever
27: wg0: <POINTOPOINT,NOARP,UP,LOWER_UP> mtu 1420 qdisc noqueue state UNKNOWN qlen 1000
link/[65534]
inet 10.9.8.2/32 brd 255.255.255.255 scope global wg0
valid_lft forever preferred_lft forever
Openwrt 1's Configuratin
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fda6:e011:5fa9::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
list ports 'eth4'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option metric '10'
option ipaddr '192.168.0.1'
config interface 'wg0'
option proto 'wireguard'
option private_key 'GGv/4oUSIBdkUpt6231o/QObwtZ4Rpio9Kbh/Mm/c38='
option listen_port '51820'
option defaultroute '0'
list addresses '10.9.8.1/24'
config wireguard_wg0
option public_key '0Mjp6LkFoUGx4OFECV71MKqyeJOtbgHnTCQZXxOe8Sw='
option route_allowed_ips '1'
option endpoint_port '51820'
option persistent_keepalive '25'
list allowed_ips '10.9.8.2/32'
list allowed_ips '192.168.2.0/24'
option endpoint_host '192.168.0.2'
config device
option name 'eth3'
option acceptlocal '1'
******************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
option masq '1'
option input 'REJECT'
option forward 'REJECT'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Openwrt 2's Configuratin
# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd15:619b:2d98::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
config interface 'wan'
option device 'eth1'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.0.2'
config interface 'wg0'
option proto 'wireguard'
option private_key 'YEtZJtUPjmzEYa80tMbVSZdPWG7gge92ZnU2kpkd7WQ='
option listen_port '51820'
list addresses '10.9.8.2/32'
config wireguard_wg0
option public_key 'JcZsifvDI9RyKT0AWeK7A0+AVYJhjFc81O1ZHj0DDng='
list allowed_ips '10.9.8.1/32'
list allowed_ips '192.168.1.0/24'
option route_allowed_ips '1'
option endpoint_host '192.168.0.1'
option endpoint_port '51820'
******************************
# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wg0'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
Someone gave me an idea,
Just a thought but traffic from router 2 to router 1 is always possible even without WG.
So maybe this is a case of asymmetric routing e.g. packets come in via a different interface then they are going out?
OpenWRT does not block INVALID packets by default, I think, so this is allowed.
I think it is, but each of my OpenWrt devices has only one WAN for WireGuard and only one LAN for connecting to PCs. It seems unlikely that asymmetric routing would occur.
You need at least one firewall rule: allow input of UDP 51820 on one of the routers wan to allow encrypted Wireguard packets in.
The encrypted packets only exist on the wan interfaces, should you want to sniff them. Inside each router the wg0 interface will carry unencrypted packets from 192.168.1.X to 192.168.2.Y as if a direct connection exists, which is the operating principle of a VPN.
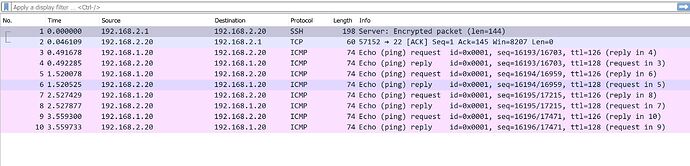
Good news, I found out that if I add an extra "-i eth1" option, where eth1 is the WAN interface. For example, if I run "tcpdump -i eth1 -w /etc/keepalived/29.cap", I will be able to capture WireGuard packets. However, if I run "tcpdump -w /etc/keepalived/30.cap", I won't be able to capture WireGuard packets.
It's still unclear to me why WireGuard is able to work without any traffic rules configured on both ends.
I guess since you have endpoint_host set on both sides, and are using the same port on both sides, this outgoing traffic punches a hole in the firewalls.
Just based on my above testing, it appears that there is no need to set up specific traffic rules on both sides to allow inbound WireGuard traffic on the WAN port. Even if the WAN zone is set to input:reject, the WAN port can still receives WireGuard traffic.
Your meaning is that if there is outbound traffic going out of the WAN port, then within a limited time(within 30 seconds), the inbound traffic can pass through?
That is because the incoming packets are treated as a response to outgoing ones: same IP and port that is configured as endpoint_host. When an endpoint_host and port is configured, the Wireguard peer config instance will attempt to initiate a connection.'
Yes that is how a stateful firewall works. For example if you go to a website on port 443, the website will reply to you from port 443, and that packet will be allowed in.