Frank
March 5, 2021, 10:30am
1
Hello all,
I have the following setup:
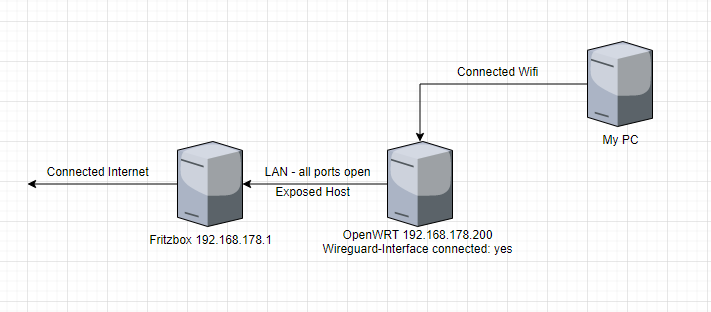
Internet =DSL==> Fritzbox router ==Exposed host==> OpenWRT router.
I have created a wireguard interface on the OpenWRT router, which is also connected.
Now I connect to the PC with the OpenWRT router (LAN or WLAN).
If I now check my external IP with the PC and browser, I still get the IP address of my own connection.
Actually, the external IP address of the end point of the Wireguard connection should be displayed.
The traffic seems to bypass the wireguard.
Does anyone have an idea where the error could be. Do you need any further information?
Many thanks in advance and best regards,
1 Like
What's the Allowed IPs option set to?
Frank
March 5, 2021, 10:46am
3
Peers => Allowed IPs => 0.0.0.0/0
Check the route table on your PC
Frank
March 5, 2021, 11:17am
5
Gateway: 192.168.178.1
This looks wrong to me because the Fritzbox has the IP address 192.168.178.1 and the OpenWRT router has the IP address 192.178.178.200.
However, I am connected directly to the OpenWRT router with the PC.
Or am I wrong?
I've just looked at your first post again. Is the PC in question shown as the "exposed host"?
It might help to draw a diagram showing what is connected where. I often find a diagram can be useful to help me work out problems. A good, free diagramming tool is diagrams.net (see my profile).
This is an odd one. Assuming OpenWRT has been set up as a router rather than as an AP, it ought to intercept and capture traffic for the VPN.
What are the contents of /etc/config/network and /etc/config/firewall on OpenWRT? You may wish to disguise any passwords or keys which are shown.
1 Like
Frank
March 5, 2021, 12:13pm
9
Thank you very much for your efforts.
network:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdb6:0e04:2d3b::/48'
config atm-bridge 'atm'
option vpi '1'
option vci '32'
option encaps 'llc'
option payload 'bridged'
option nameprefix 'dsl'
config dsl 'dsl'
option annex 'b'
option tone 'av'
option ds_snr_offset '0'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.178.200'
option netmask '255.255.255.0'
option ip6assign '60'
list dns '192.168.178.1'
option gateway '192.168.178.1'
config interface 'wan'
option ifname 'dsl0'
option proto 'pppoe'
option username 'username'
option password 'password'
option ipv6 '1'
config device 'wan_dsl0_dev'
option name 'dsl0'
option macaddr '34:81:c4:19:dc:d5'
config interface 'wan6'
option ifname '@wan'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 1 2 4 6t'
config interface 'WGINTERFACE'
option proto 'wireguard'
list addresses '10.71.24.58'
option private_key ''
option force_link '1'
config wireguard_WGINTERFACE
option public_key ''
option endpoint_port '51820'
list allowed_ips '0.0.0.0/0'
option route_allowed_ips '1'
option endpoint_host '86.xyz'
firewall:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config zone
option network 'WGINTERFACE'
option name 'WGZONE'
option mtu_fix '1'
option input 'REJECT'
option forward 'REJECT'
option masq '1'
option output 'ACCEPT'
config forwarding
option dest 'WGZONE'
option src 'lan'
The combination of your diagram, the Fritz!Box IP address, and the "lan" interface configuration suggest that you've got your OpenWRT box configured as a "dumb AP", passing the Fritz!Box's subnet details to the PC over WiFi. I knocked up a diagram to illustrate the concept in another thread - Ping fail, okpg update fail, but wlan and AP works - #7 by iplaywithtoys
If that's the case, that would explain why traffic from your PC isn't being captured by the VPN: the PC's router is the Fritz!Box and not OpenWRT.
2 Likes
Frank
March 5, 2021, 1:52pm
12
Hello iplaywithtoys,
I have now reconfigured to get the second diagram from your link (no dumb AP) more.
Unfortunately, it still does not work.
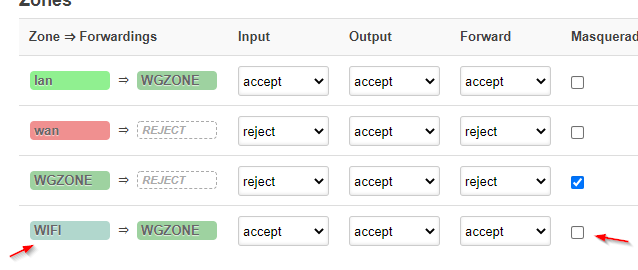
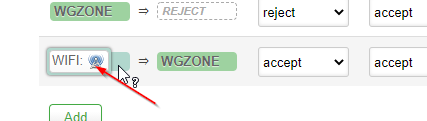
Judging by those screenshots, it looks like your "WIFI" interface isn't assigned to your "WIFI" zone.
Normally, the colours indicate which firewall zone is applicable. Your interface is grey, which suggests no firewall zone has been applied.
1 Like
Collect the diagnostics and post it to pastebin.com redacting the private parts:
uci show network; uci show wireless; uci show dhcp; uci show firewall; \
ip address show; ip route show table all; ip rule show; iptables-save; wg show; \
pgrep -f -a dnsmasq; head -v -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
uci set dhcp.@dnsmasq[0].noresolv="1"
uci set dhcp.lan.interface="WIFI"
uci commit dhcp
/etc/init.d/dnsmasq restart
uci -q delete network.lan.type
uci set network.lan.metric="100"
uci set network.WIFI.type="bridge"
uci commit network
/etc/init.d/network restart
2 Likes
Frank
March 5, 2021, 3:08pm
19
It works! Thank you for your efforts!
1 Like
system
March 15, 2021, 3:09pm
20
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.