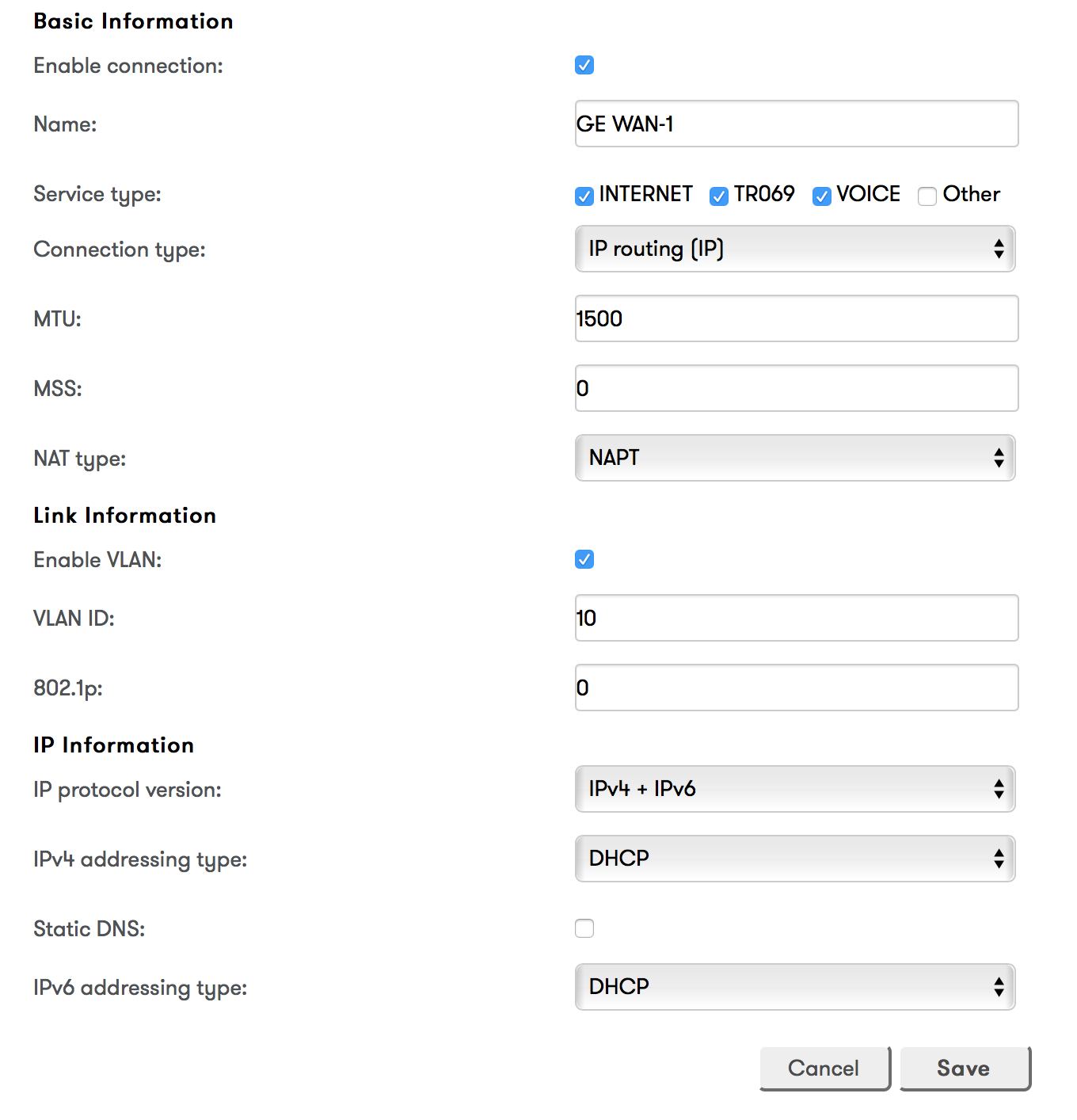
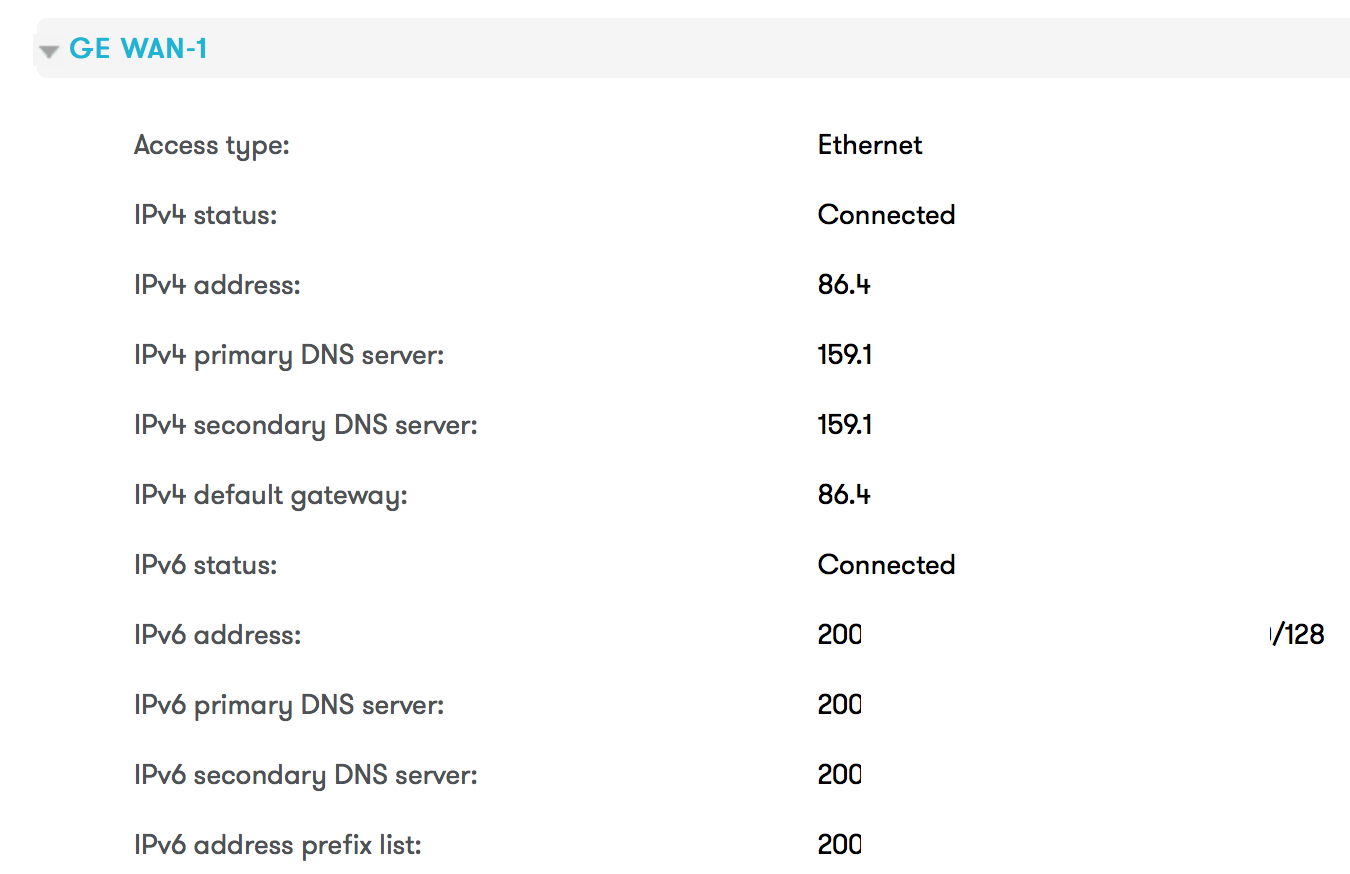
I installed LEDE v17.01.1 on a TP-Link TD-W8970B router including a DSL modem. Everything went fine, WLAN is working. Anyhow, I cannot get the internet connection working. With the original firmware installed, it worked.
I think the most important lines in the log are the following:
Tue Apr 18 04:20:06 2017 daemon.notice netifd: Interface 'wan' is enabled
Tue Apr 18 04:20:06 2017 daemon.notice netifd: Interface 'wan' is setting up now
Tue Apr 18 04:20:06 2017 daemon.info pppd[25265]: Plugin rp-pppoe.so loaded.
Tue Apr 18 04:20:06 2017 daemon.info pppd[25265]: RP-PPPoE plugin version 3.8p compiled against pppd 2.4.7
Tue Apr 18 04:20:06 2017 daemon.notice pppd[25265]: pppd 2.4.7 started by root, uid 0
Tue Apr 18 04:20:06 2017 daemon.debug pppd[25265]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Apr 18 04:20:06 2017 daemon.debug pppd[25265]: dst ff:ff:ff:ff:ff:ff src 00:20:da:86:23:75
Tue Apr 18 04:20:06 2017 daemon.debug pppd[25265]: [service-name]
Tue Apr 18 04:20:11 2017 daemon.debug pppd[25265]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Apr 18 04:20:11 2017 daemon.debug pppd[25265]: dst ff:ff:ff:ff:ff:ff src 00:20:da:86:23:75
Tue Apr 18 04:20:11 2017 daemon.debug pppd[25265]: [service-name]
Tue Apr 18 04:20:16 2017 daemon.debug pppd[25265]: Send PPPOE Discovery V1T1 PADI session 0x0 length 4
Tue Apr 18 04:20:16 2017 daemon.debug pppd[25265]: dst ff:ff:ff:ff:ff:ff src 00:20:da:86:23:75
Tue Apr 18 04:20:16 2017 daemon.debug pppd[25265]: [service-name]
Tue Apr 18 04:20:21 2017 daemon.warn pppd[25265]: Timeout waiting for PADO packets
Tue Apr 18 04:20:21 2017 daemon.err pppd[25265]: Unable to complete PPPoE Discovery
Tue Apr 18 04:20:21 2017 daemon.info pppd[25265]: Exit.
Tue Apr 18 04:20:22 2017 daemon.notice netifd: Interface 'wan' is now down
Tue Apr 18 04:20:22 2017 daemon.notice netifd: Interface 'wan' is disabled
My ISP is easybell.
My /etc/config/network file:
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config dsl 'dsl'
option firmware '/lib/firmware/lantiq-vrx200-b.bin'
option annex 'b'
option xfer_mode 'ptm'
option line_mode 'adsl'
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'ptm0'
option proto 'pppoe'
option ipv6 'auto'
option username 'XXX'
option password 'XXX'
config device 'wan_dev'
option name 'ptm0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '0 2 4 5 6t'
My /etc/config/firewall file:
config defaults
option syn_flood 1
option input ACCEPT
option output ACCEPT
option forward REJECT
# Uncomment this line to disable ipv6 rules
# option disable_ipv6 1
config zone
option name lan
list network 'lan'
option input ACCEPT
option output ACCEPT
option forward ACCEPT
config zone
option name wan
list network 'wan'
list network 'wan6'
option input REJECT
option output ACCEPT
option forward REJECT
option masq 1
option mtu_fix 1
config forwarding
option src lan
option dest wan
# We need to accept udp packets on port 68,
# see https://dev.openwrt.org/ticket/4108
config rule
option name Allow-DHCP-Renew
option src wan
option proto udp
option dest_port 68
option target ACCEPT
option family ipv4
# Allow IPv4 ping
config rule
option name Allow-Ping
option src wan
option proto icmp
option icmp_type echo-request
option family ipv4
option target ACCEPT
config rule
option name Allow-IGMP
option src wan
option proto igmp
option family ipv4
option target ACCEPT
# Allow DHCPv6 replies
# see https://dev.openwrt.org/ticket/10381
config rule
option name Allow-DHCPv6
option src wan
option proto udp
option src_ip fc00::/6
option dest_ip fc00::/6
option dest_port 546
option family ipv6
option target ACCEPT
config rule
option name Allow-MLD
option src wan
option proto icmp
option src_ip fe80::/10
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family ipv6
option target ACCEPT
# Allow essential incoming IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Input
option src wan
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
list icmp_type router-solicitation
list icmp_type neighbour-solicitation
list icmp_type router-advertisement
list icmp_type neighbour-advertisement
option limit 1000/sec
option family ipv6
option target ACCEPT
# Allow essential forwarded IPv6 ICMP traffic
config rule
option name Allow-ICMPv6-Forward
option src wan
option dest *
option proto icmp
list icmp_type echo-request
list icmp_type echo-reply
list icmp_type destination-unreachable
list icmp_type packet-too-big
list icmp_type time-exceeded
list icmp_type bad-header
list icmp_type unknown-header-type
option limit 1000/sec
option family ipv6
option target ACCEPT
# include a file with users custom iptables rules
config include
option path /etc/firewall.user
### EXAMPLE CONFIG SECTIONS
# do not allow a specific ip to access wan
#config rule
# option src lan
# option src_ip 192.168.45.2
# option dest wan
# option proto tcp
# option target REJECT
# block a specific mac on wan
#config rule
# option dest wan
# option src_mac 00:11:22:33:44:66
# option target REJECT
# block incoming ICMP traffic on a zone
#config rule
# option src lan
# option proto ICMP
# option target DROP
# port redirect port coming in on wan to lan
#config redirect
# option src wan
# option src_dport 80
# option dest lan
# option dest_ip 192.168.16.235
# option dest_port 80
# option proto tcp
# port redirect of remapped ssh port (22001) on wan
#config redirect
# option src wan
# option src_dport 22001
# option dest lan
# option dest_port 22
# option proto tcp
# allow IPsec/ESP and ISAKMP passthrough
config rule
option src wan
option dest lan
option proto esp
option target ACCEPT
config rule
option src wan
option dest lan
option dest_port 500
option proto udp
option target ACCEPT
### FULL CONFIG SECTIONS
#config rule
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 80
# option dest wan
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
# option target REJECT
#config redirect
# option src lan
# option src_ip 192.168.45.2
# option src_mac 00:11:22:33:44:55
# option src_port 1024
# option src_dport 80
# option dest_ip 194.25.2.129
# option dest_port 120
# option proto tcp
Any help would be appreciated!