m0t0k0
February 14, 2023, 8:51pm
1
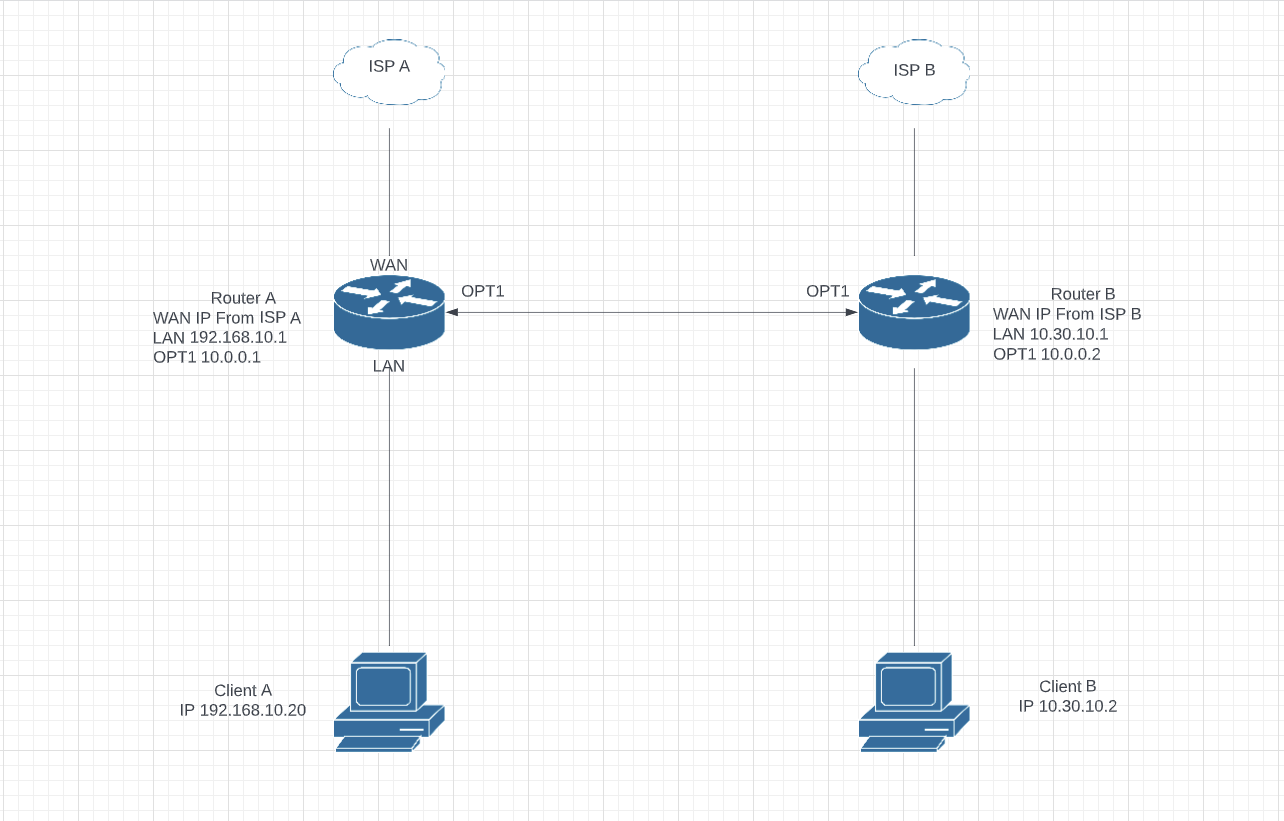
Hi I have a networking problem which I can't seem to figure out despite reading lots of information about it.
I then created a route on Router A with the following settings
From Client A I can ping 10.0.0.1 but I cannot ping 10.0.0.2 or 10.30.10.1
Is anyone able to help me out, please?
Assuming everything is generally configured properly, the routes would look like this:
Router A: 10.30.10.0/24 via 10.0.0.2
Let's start by taking a look at the config from router A:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
1 Like
m0t0k0
February 14, 2023, 9:08pm
3
Hi Thanks for the response I have included the config files you requested.
I apologise in advance there is quite a lot going on in Router A already also the interface is actually called VMBR1 not OPT1
/network
config interface 'loopback'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
option device 'lo'
config globals 'globals'
option ula_prefix '***************'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ipaddr '192.168.10.1'
option device 'eth0'
config interface 'wan'
option proto 'pppoe'
option ipv6 '0'
option username 'broadbanduser@btbroadband.com'
option password 'bt'
option device 'eth1'
config interface 'KIDS'
option proto 'static'
option ipaddr '192.168.69.1'
option netmask '255.255.255.0'
option device 'eth0.69'
config interface 'IOIT'
option proto 'static'
option ipaddr '192.168.101.1'
option netmask '255.255.255.0'
option device 'eth0.101'
config interface 'GUEST'
option proto 'static'
option ipaddr '192.168.57.1'
option netmask '255.255.255.0'
option device 'eth0.57'
config interface 'IPTV_LAN'
option proto 'static'
option ipaddr '192.168.99.1'
option netmask '255.255.255.0'
option device 'eth0.99'
config interface 'IPTV_WAN'
option proto 'static'
option ipaddr '10.22.22.1'
option netmask '255.255.255.0'
option device 'eth1'
config interface 'MGMT'
option proto 'static'
option device 'eth0.40'
option netmask '255.255.255.0'
option ipaddr '10.7.40.1'
config interface 'MYST'
option proto 'static'
option device 'eth0.80'
option ipaddr '192.168.80.1'
option netmask '255.255.255.0'
config interface 'VMBR1'
option proto 'static'
option device 'eth2'
option netmask '255.255.255.0'
option ipaddr '10.0.0.1'
option defaultroute '0'
config route
option interface 'VMBR1'
option netmask '255.255.255.0'
option gateway '10.0.0.2'
option target '10.30.10.0/24'
/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'wan'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option family 'ipv4'
option input 'REJECT'
list network 'wan'
config zone
option name 'IPTV_WAN'
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
list network 'IPTV_WAN'
config zone
option name 'IPTV_LAN'
option forward 'REJECT'
option output 'ACCEPT'
option input 'ACCEPT'
list network 'IPTV_LAN'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'lan'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option family 'ipv4'
option target 'ACCEPT'
option name 'Kids-Print'
option src 'KIDS'
option dest 'lan'
list dest_ip '192.168.10.2'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
config rule
option name 'Kids-net-off-Weekday'
list proto 'all'
option src 'KIDS'
option dest 'wan'
option target 'REJECT'
option weekdays 'Sun Mon Tue Wed Thu'
option start_time '19:30:00'
option stop_time '06:30:00'
option enabled '0'
config rule
option name 'Kids-Net-off-weekend'
list proto 'all'
option src 'KIDS'
option dest 'wan'
option target 'REJECT'
option weekdays 'Fri Sat'
option start_time '20:00:00'
option stop_time '07:00:00'
option enabled '0'
config rule
option src 'IOIT'
option name 'Allow-Game Stream'
list src_ip '192.168.101.20'
option dest 'lan'
list dest_ip '192.168.10.20'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-IGMP'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
option dest 'IPTV_LAN'
option src 'IPTV_WAN'
config include
option path '/etc/firewall.user'
config redirect
option src 'wan'
option src_dport '443'
option target 'DNAT'
option dest_ip '192.168.10.10'
list proto 'tcp'
option dest 'lan'
option name 'SWAG-HTTPS'
option dest_port '443'
config redirect
option dest_port '19132'
option src 'wan'
option name 'Minecraft'
option src_dport '19132'
option target 'DNAT'
option dest 'lan'
option dest_ip '192.168.10.55'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
config redirect
option dest_port '3478'
option src 'wan'
option name 'Unifi-STUN'
option src_dport '3478'
option target 'DNAT'
option dest_ip '192.168.10.10'
option dest 'lan'
list proto 'udp'
config redirect
option dest_port '8443'
option src 'wan'
option name 'UniFi-Remote-Managment'
option src_dport '8443'
option target 'DNAT'
option dest_ip '192.168.10.10'
option dest 'lan'
list proto 'tcp'
config redirect
option dest_port '8080'
option src 'wan'
option name 'UniFi-Adoption'
option src_dport '8080'
option target 'DNAT'
option dest_ip '192.168.10.10'
option dest 'lan'
list proto 'tcp'
config rule
option dest 'lan'
list dest_ip '192.168.10.10'
option target 'ACCEPT'
option family 'ipv4'
option name 'Allow-Emby-HTTPS'
option dest_port '443'
option src '*'
list proto 'tcp'
config rule
option src_port '5353'
option src '*'
option name 'Allow-mDNS'
option target 'ACCEPT'
option family 'ipv4'
list dest_ip '224.0.0.251'
option dest_port '5353'
list proto 'udp'
config rule
option name 'Kids to Minecraft'
option dest 'lan'
list dest_ip '192.168.10.55'
option target 'ACCEPT'
option family 'ipv4'
option src 'KIDS'
option dest_port '19132'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
config rule
option src 'GUEST'
option name 'Guest to Minecraft'
option dest 'lan'
list dest_ip '192.168.10.55'
option target 'ACCEPT'
option dest_port '19132'
list proto 'tcp'
list proto 'udp'
list proto 'icmp'
config rule
option name 'Prox-to-Unraid'
option src 'MGMT'
list src_ip '10.7.40.9'
option dest 'lan'
list dest_ip '192.168.10.10'
option target 'ACCEPT'
config rule
option name 'Allow-Ping'
option proto 'icmp'
option family 'ipv4'
option target 'ACCEPT'
list icmp_type 'echo-request'
option src 'wan'
option enabled '0'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config forwarding
option dest 'wan'
option src 'IPTV_LAN'
config zone
option name 'IOIT'
option forward 'REJECT'
option output 'ACCEPT'
option input 'ACCEPT'
list network 'IOIT'
config zone
option name 'GUEST'
option forward 'REJECT'
option output 'ACCEPT'
option input 'ACCEPT'
list network 'GUEST'
config forwarding
option dest 'wan'
option src 'GUEST'
config zone
option name 'KIDS'
option forward 'REJECT'
option output 'ACCEPT'
option input 'ACCEPT'
list network 'KIDS'
config forwarding
option dest 'IOIT'
option src 'KIDS'
config forwarding
option dest 'wan'
option src 'KIDS'
config forwarding
option dest 'IOIT'
option src 'GUEST'
config forwarding
option dest 'wan'
option src 'IOIT'
config forwarding
option dest 'IOIT'
option src 'lan'
config forwarding
option dest 'GUEST'
option src 'lan'
config forwarding
option dest 'KIDS'
option src 'lan'
config redirect
option dest_port '2443'
option src 'wan'
option name 'unRAID-Remote-Management'
option src_dport '2443'
option target 'DNAT'
option dest_ip '192.168.10.10'
option dest 'lan'
list proto 'tcp'
config redirect
option dest_port '8444'
option src 'wan'
option name 'Chia'
option src_dport '8444'
option target 'DNAT'
option dest 'lan'
option dest_ip '192.168.10.10'
config redirect
option src 'wan'
option name 'SWAG-HTTP'
option src_dport '80'
option target 'DNAT'
option dest_ip '192.168.10.10'
option dest 'lan'
list proto 'tcp'
option dest_port '80'
option enabled '0'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'notifiarr'
option src 'wan'
option src_dport '5454'
option dest_ip '192.168.10.10'
option dest_port '5454'
config zone
option name 'MYST'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'MYST'
config forwarding
option src 'MYST'
option dest 'wan'
config zone
option name 'MGMT'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'MGMT'
config forwarding
option src 'lan'
option dest 'MGMT'
config forwarding
option src 'MGMT'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'MYST'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'myst'
list proto 'udp'
option src 'wan'
option dest_ip '192.168.80.2'
option src_dport '10000-60000'
config include 'miniupnpd'
option type 'script'
option path '/usr/share/miniupnpd/firewall.include'
option family 'any'
option reload '1'
config zone
option name 'VMBR1'
option input 'ACCEPT'
option output 'ACCEPT'
list network 'VMBR1'
option forward 'ACCEPT'
config rule
option name 'Allow-JacobPC-VMBR1'
option src 'lan'
list src_ip '192.168.10.20'
option dest 'VMBR1'
option target 'ACCEPT'
config forwarding
option src 'VMBR1'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'VMBR1'
Remove the option default route '0' line from the VMBR1 network.
I'm not sure if it matters, but only use one subnet mask method... either the actual netmask field or the CIDR (/24) notation... don't use both.
Firewall looks fine. Make sure that the other router has similar configs (obviously different, but with the same general features).
Is the other router setup the same way?
1 Like
mk24
February 14, 2023, 9:59pm
5
I think this makes the rule to allow one PC redundant, since the default will forward any traffic from lan to VMBR1.
I really wish people wouldn't dump a whole complicated configuration to wade through. Take two routers in default configuration, and set them up just enough to test / demonstrate the particular functionality that you want to implement.
1 Like
m0t0k0
February 14, 2023, 10:35pm
6
Thank you I will have a look tomorrow.
m0t0k0
February 14, 2023, 10:37pm
7
Ah yes I had a rule for the single device but could not get it working so tried to just make it wide open.
Sorry but Router A is my main gateway to the Internet so I can't start with a fresh install.
m0t0k0
February 15, 2023, 12:07pm
8
Thank you for the help I have it sorted now.
I was not aware that my client OS (Win 10) did not respond to ping requests by default.
I think I may have had a working route from just following the wiki but as I was unable to ping the client I started tweaking things.
Today I removed all the interfaces and rules and started again. Then after a bit of googling, I was able to enable Echo Requests on Client B and it worked.
system
February 25, 2023, 12:07pm
9
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.