Hello everyone,
I have just moved in and I have an electrical panel with rj45 plugs connecting the house.
My internet box is in the entrance hall, next to the electric board. My openwrt router (dhcp, dns, guest wifi, logs, vpn...) is my office with several equipments connected to the LAN of the router.
My question is about the equipments in the living room (PS3, raspberry...): how to connect them to my router so that they are in the LAN?
I suppose that VLANs are the solution but I would like your opinion on this question. Is it possible with a single cable to pass traffic coming from my living room equipment to the WAN port of the router and have it go out through the same port?
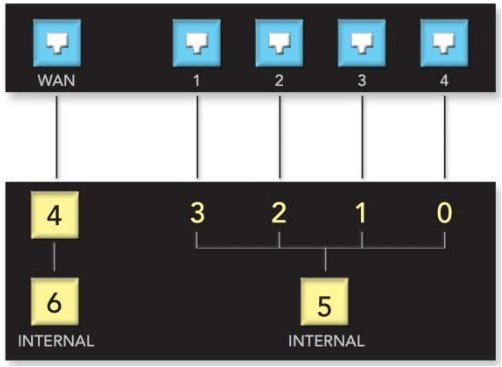
Here is a diagram to be more explicit (I hope it will...):
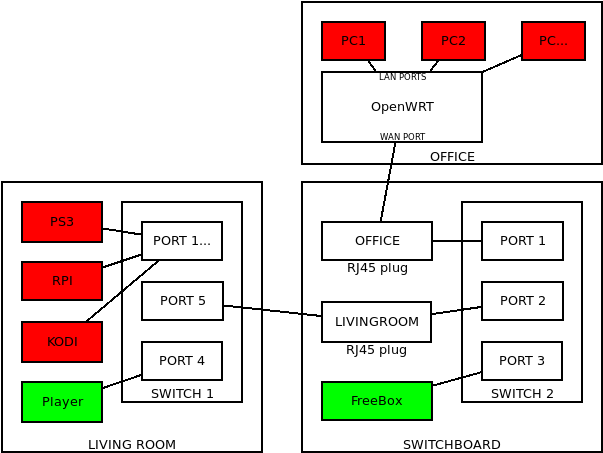
The player is an equipment supplied by my french operator (Free) and is currently operated by CPL, so its integration is not mandatory in the diagram.
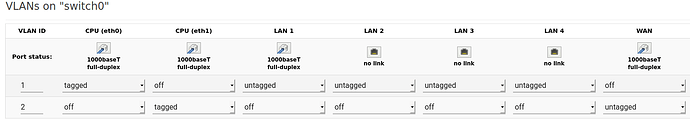
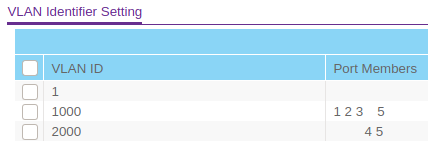
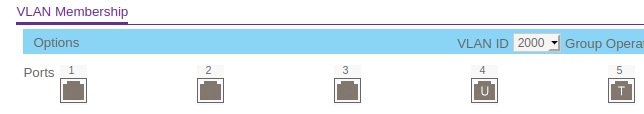
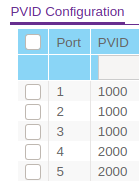
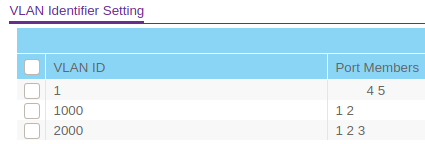
I've added 2 manageable switches (not purchased yet) on what I think is correct:
- SWITCH 1
- PORT 1...: VLAN1
- PORT 5: trunk
- PORT 4: VLAN2
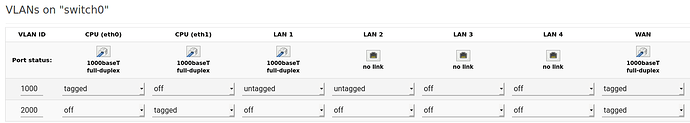
- SWITCH 2
- PORT 1: VLAN 1/2
- PORT 2: VLAN 1/2
- PORT 3: trunk
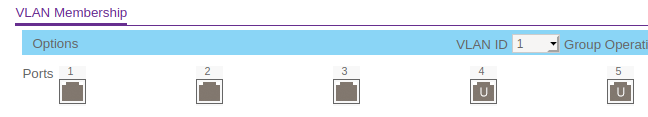
- OpenWRT:
- WAN PORT: VLAN 1/2
Is my understanding good ? I am of course open to any other configuration or suggestions 
Thank you !