Hello all,
I am new to Openwrt, and am having trouble trying to figure out a few things. Hopefully someone can point me in the right direction.
I am trying to create a fairly simple setup. I have a home scenario with three hard-wired computers and one computer on wireless. My primary goal is to get as close as possible to complete isolation for each computer. I don't want any computer to see or be able to get to any other computer or to the router. I have a very slow (about 6 Mbps) Internet, so my goal with Openwrt doesn't center around improving the wireless. I don't need to do anything fancy with that. I only want Internet access for each computer and that's all. Each VLAN has one virtual interface that has a firewall zone forwardings rule that is only interface x --> wan and that's it.
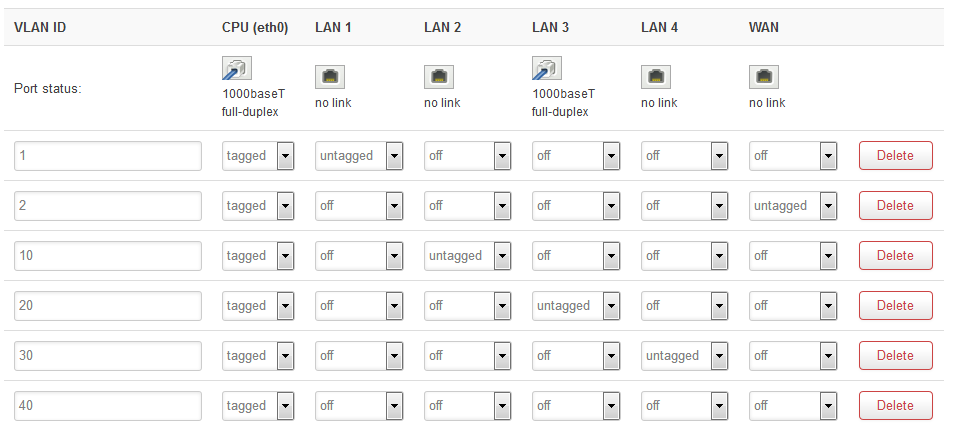
I started by building upon the default VLAN configuration, adding three more VLANs (ignore the additional extra VLAN 40, I thought I needed one for the wireless, so I guess I will just delete that one out. I unbridged the wireless and it sits by itself in the interfaces page.).
My approach is to have each physical port on the router be assigned to its own VLAN. Three ports would be for the three computers, and the remaining port would be the only access for the Luci interface (which I assumed will be the lan port 1, the default lan). I have an additional 'extra' computer dedicated just for this access, and it will only be plugged in when I want to access the router to make changes, and only when the other computers are unplugged and the modem is turned off i.e. no Internet access. I have been told this is overkill, but I would like to do it this way.
Let me say that I am doing most of this via Luci, as I am not too skilled with CLI. I can SSH into the router and use a text editor to make changes when I need to if it's something that can't be done via Luci (like change the access port number from 443, for example). So far this has worked well.
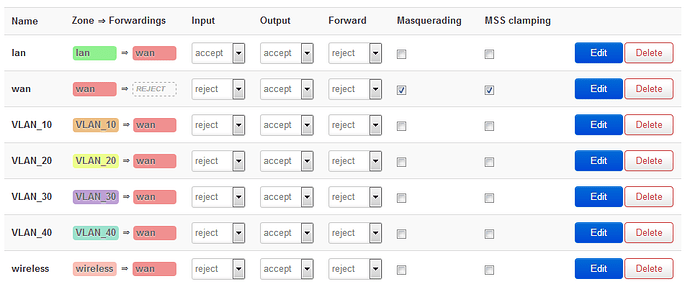
Here's what I am trying to figure out. From any VLAN/router port/computer I can still access the router via the Luci interface. My goal is to only be able to access the router by let's say port 1 (no wireless access either). I noticed, by accident, if I set the the input to reject for that interface I could no longer access the Luci interface. I only did this because in reading one post the person said there is no reason in a situation like this to accept input. I found that I can access the Internet fine set to reject input. The only reason I initially had it set to accept is because the default lan zone was set that way. So, is this the correct way to block router access from the other ports/wireless? Make sure input is set to reject? Or is there a better way?
The other thing I need to be sure of is that computers on different VLANs can't communicate with each other. I thought that the very nature of a VLAN on a different subnet would accomplish this. Right now I am not able to ping any computer from any other computer when set up as described. But I read a post where the person described quite an elaborate set of firewall rules to block access from one VLAN to another. Is this necessary (or just a good second layer to do the same thing)? Or was that done because the person wanted to accept input and this is the only way to block cross VLAN traffic when accepting input? That doesn't sound right because I wasn't able to ping any other computers even with input set to accept... What's the best way to assure isolation?
Finally, I was changing my Luci access port as mentioned above, based on instructions from this page:
https://openwrt.org/docs/guide-user/base-system/uci
Scroll down to 'Securing uHTTPd' and it says:
"By default, uHTTPd is bind to 0.0.0.0 which also includes the WAN port of your router. To bind uHTTPd to the LAN port only you have to change the listen_http and listen_https options to your LAN IP address. ...edit /etc/config/uhttpd and bind listen_http to specific 192.168.1.1 IP instead of 0.0.0.0 and comment out IPv6 bindings"
config uhttpd main
# HTTP listen addresses, multiple allowed
list listen_http 192.168.1.1:80
# list listen_http [::]:80
# HTTPS listen addresses, multiple allowed
list listen_https 192.168.1.1:443
# list listen_https [::]:443
I thought that this would then only allow access from the lan port, but it didn't change anything. I could still access the Luci interface from any port, and I didn't notice any other differences. Can someone explain in simple terms what this actually does, then, and if this in any way ties into what I am trying to do?
I am sorry for so many questions. I have spent more hours than I can count trying to figure this out on my own. I am here because I just can't get anywhere on this. I've read all the documentation and forum posts I could find. Thanks.