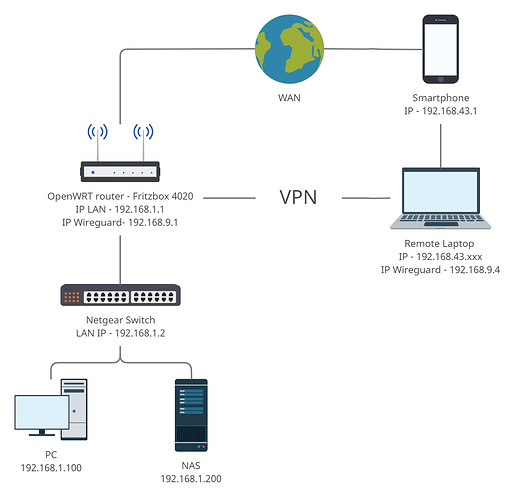
Hi, recently I've installed OpenWRT on my Fritzbox router and it sparked my interest for networking stuff, considering I've also got a NAS storage (a Western Digital Mycloud EX2 Ultra) the natural evolution was to setup a VPN to be able to access my network (and the NAS in particular) from the outside.
Right now I have the Wireguard server running on my Fritzbox 4020 with the IP 198.168.9.1 and I've tried to connect using my laptop (using the smartphone 4g network) which has the IP 198.168.9.4 on the WG tunnel.
So far so good, I can connect to the VPN, I can browse the internet, I can access the NAS remotely, I can ping the NAS, I can access the Luci configuration page from the VPN (either using 198.168.1.1 and 198.168.9.1) and I can mount the NAS as a Windows volume.
There are however a few issues I'm having that are confusing me:
- I can't ping any of the 3 computers attached to the Netgear switch on the LAN from the VPN. As I said, I can ping the NAS (and I can also ping the router and the Netgear switch as well), I don't understand if it's a problem due to the firewall on the computers or if there is something else going on since the ping command works with no issues from within the LAN.
- I can't send the Wake-on-LAN packet via Wireguard to remotely wake up the NAS. It works fine if I send the command using the software "WakeMeOnLan" on a PC connected to the local network but it doesn't work from the WG laptop. That might be an issue of the software tho, in case if you know another "user firendly" way to send a WoL packet via Wireguard feel free to tell me!
- I can't ping the Laptop connected to Wireguard from any device on the LAN. Not sure if that depends on the WG tunnel configuration or if that depends on the FW but I can ping the Wireguard 192.168.9.1 interface.
Basically what I want to obtain is that my laptop connected via Wireguard acts like it's part of the LAN, which it kinda already does but not completely. I thought assigning the Wireguard interface to the LAN zone was enough but apparently it's not 
I have a static public IP for the WAN interface, so no problem there. I'm running a DDNS anyway just because I wanted to see how that works but using the IP in the WG configuration changes nothing.
This is a quick map of my network, there are more computers and other devices attached to the Netgear but they shouldn't be important for the problems I'm having.
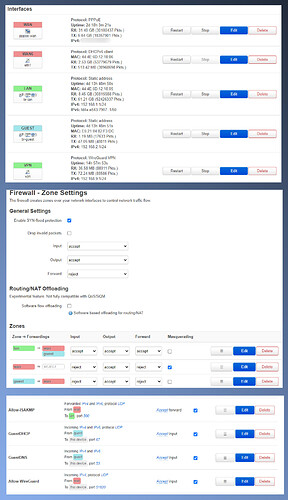
This is a quick look at the firewall configuration
This is the tunnel file on my laptop
[Interface]
PrivateKey = **********=
Address = 192.168.9.4/24
DNS = 1.1.1.1, 8.8.8.8
[Peer]
PublicKey = **********=
AllowedIPs = 0.0.0.0/0
Endpoint = mywan:51820
This is the Uci Show All result:
P.S. please tell me if I forgot to delete any sensible data 
adblock.global=adblock
adblock.global.adb_debug='0'
adblock.global.adb_safesearch='0'
adblock.global.adb_dnsfilereset='0'
adblock.global.adb_mail='0'
adblock.global.adb_report='0'
adblock.global.adb_backup='1'
adblock.global.adb_maxqueue='4'
adblock.global.adb_dns='dnsmasq'
adblock.global.adb_fetchutil='uclient-fetch'
adblock.global.adb_sources='adaway' 'adguard' 'android_tracking' 'bitcoin' 'firetv_tracking' 'openphish' 'phishing_army' 'reg_it' 'spam404'
adblock.global.adb_forcedns='0'
adblock.global.adb_enabled='1'
ddns.global=ddns
ddns.global.ddns_dateformat='%F %R'
ddns.global.ddns_loglines='250'
ddns.global.upd_privateip='0'
ddns.myddns_ipv4=service
ddns.myddns_ipv4.interface='wan'
ddns.myddns_ipv4.service_name='no-ip.com'
ddns.myddns_ipv4.enabled='1'
ddns.myddns_ipv4.username='**********'
ddns.myddns_ipv4.password='********'
ddns.myddns_ipv4.lookup_host='*************'
ddns.myddns_ipv4.domain='*************'
ddns.myddns_ipv4.ip_source='web'
dhcp.@dnsmasq[0]=dnsmasq
dhcp.@dnsmasq[0].domainneeded='1'
dhcp.@dnsmasq[0].boguspriv='1'
dhcp.@dnsmasq[0].filterwin2k='0'
dhcp.@dnsmasq[0].localise_queries='1'
dhcp.@dnsmasq[0].rebind_protection='1'
dhcp.@dnsmasq[0].rebind_localhost='1'
dhcp.@dnsmasq[0].local='/lan/'
dhcp.@dnsmasq[0].domain='lan'
dhcp.@dnsmasq[0].expandhosts='1'
dhcp.@dnsmasq[0].nonegcache='0'
dhcp.@dnsmasq[0].authoritative='1'
dhcp.@dnsmasq[0].readethers='1'
dhcp.@dnsmasq[0].leasefile='/tmp/dhcp.leases'
dhcp.@dnsmasq[0].resolvfile='/tmp/resolv.conf.auto'
dhcp.@dnsmasq[0].nonwildcard='1'
dhcp.@dnsmasq[0].localservice='1'
dhcp.@dnsmasq[0].confdir='/tmp/dnsmasq.d'
dhcp.lan=dhcp
dhcp.lan.interface='lan'
dhcp.lan.start='100'
dhcp.lan.limit='150'
dhcp.lan.leasetime='12h'
dhcp.lan.dhcpv6='server'
dhcp.lan.ra='server'
dhcp.lan.ra_management='1'
dhcp.wan=dhcp
dhcp.wan.interface='wan'
dhcp.wan.ignore='1'
dhcp.odhcpd=odhcpd
dhcp.odhcpd.maindhcp='0'
dhcp.odhcpd.leasefile='/tmp/hosts/odhcpd'
dhcp.odhcpd.leasetrigger='/usr/sbin/odhcpd-update'
dhcp.odhcpd.loglevel='4'
dhcp.Ospiti=dhcp
dhcp.Ospiti.start='100'
dhcp.Ospiti.leasetime='12h'
dhcp.Ospiti.limit='150'
dhcp.Ospiti.interface='Ospiti'
dhcp.guest=dhcp
dhcp.guest.start='100'
dhcp.guest.leasetime='12h'
dhcp.guest.limit='150'
dhcp.guest.interface='guest'
dropbear.@dropbear[0]=dropbear
dropbear.@dropbear[0].PasswordAuth='on'
dropbear.@dropbear[0].Port='22'
etherwake.setup=etherwake
etherwake.setup.pathes='/usr/bin/etherwake /usr/bin/ether-wake'
etherwake.setup.sudo='off'
etherwake.setup.broadcast='off'
etherwake.@target[0]=target
etherwake.@target[0].name='example'
etherwake.@target[0].mac='11:22:33:44:55:66'
etherwake.@target[0].password='AABBCCDDEEFF'
etherwake.@target[0].wakeonboot='off'
firewall.@defaults[0]=defaults
firewall.@defaults[0].input='ACCEPT'
firewall.@defaults[0].output='ACCEPT'
firewall.@defaults[0].forward='REJECT'
firewall.@defaults[0].synflood_protect='1'
firewall.lan=zone
firewall.lan.name='lan'
firewall.lan.input='ACCEPT'
firewall.lan.output='ACCEPT'
firewall.lan.forward='ACCEPT'
firewall.lan.network='lan vpn'
firewall.wan=zone
firewall.wan.name='wan'
firewall.wan.output='ACCEPT'
firewall.wan.masq='1'
firewall.wan.mtu_fix='1'
firewall.wan.network='wan wan6'
firewall.wan.input='REJECT'
firewall.wan.forward='REJECT'
firewall.@forwarding[0]=forwarding
firewall.@forwarding[0].src='lan'
firewall.@forwarding[0].dest='wan'
firewall.@rule[0]=rule
firewall.@rule[0].name='Allow-DHCP-Renew'
firewall.@rule[0].src='wan'
firewall.@rule[0].proto='udp'
firewall.@rule[0].dest_port='68'
firewall.@rule[0].target='ACCEPT'
firewall.@rule[0].family='ipv4'
firewall.@rule[1]=rule
firewall.@rule[1].name='Allow-Ping'
firewall.@rule[1].src='wan'
firewall.@rule[1].proto='icmp'
firewall.@rule[1].icmp_type='echo-request'
firewall.@rule[1].family='ipv4'
firewall.@rule[1].target='ACCEPT'
firewall.@rule[2]=rule
firewall.@rule[2].name='Allow-IGMP'
firewall.@rule[2].src='wan'
firewall.@rule[2].proto='igmp'
firewall.@rule[2].family='ipv4'
firewall.@rule[2].target='ACCEPT'
firewall.@rule[3]=rule
firewall.@rule[3].name='Allow-DHCPv6'
firewall.@rule[3].src='wan'
firewall.@rule[3].proto='udp'
firewall.@rule[3].src_ip='fc00::/6'
firewall.@rule[3].dest_ip='fc00::/6'
firewall.@rule[3].dest_port='546'
firewall.@rule[3].family='ipv6'
firewall.@rule[3].target='ACCEPT'
firewall.@rule[4]=rule
firewall.@rule[4].name='Allow-MLD'
firewall.@rule[4].src='wan'
firewall.@rule[4].proto='icmp'
firewall.@rule[4].src_ip='fe80::/10'
firewall.@rule[4].icmp_type='130/0' '131/0' '132/0' '143/0'
firewall.@rule[4].family='ipv6'
firewall.@rule[4].target='ACCEPT'
firewall.@rule[5]=rule
firewall.@rule[5].name='Allow-ICMPv6-Input'
firewall.@rule[5].src='wan'
firewall.@rule[5].proto='icmp'
firewall.@rule[5].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type' 'router-solicitation' 'neighbour-solicitation' 'router-advertisement' 'neighbour-advertisement'
firewall.@rule[5].limit='1000/sec'
firewall.@rule[5].family='ipv6'
firewall.@rule[5].target='ACCEPT'
firewall.@rule[6]=rule
firewall.@rule[6].name='Allow-ICMPv6-Forward'
firewall.@rule[6].src='wan'
firewall.@rule[6].dest='*'
firewall.@rule[6].proto='icmp'
firewall.@rule[6].icmp_type='echo-request' 'echo-reply' 'destination-unreachable' 'packet-too-big' 'time-exceeded' 'bad-header' 'unknown-header-type'
firewall.@rule[6].limit='1000/sec'
firewall.@rule[6].family='ipv6'
firewall.@rule[6].target='ACCEPT'
firewall.@rule[7]=rule
firewall.@rule[7].name='Allow-IPSec-ESP'
firewall.@rule[7].src='wan'
firewall.@rule[7].dest='lan'
firewall.@rule[7].proto='esp'
firewall.@rule[7].target='ACCEPT'
firewall.@rule[8]=rule
firewall.@rule[8].name='Allow-ISAKMP'
firewall.@rule[8].src='wan'
firewall.@rule[8].dest='lan'
firewall.@rule[8].dest_port='500'
firewall.@rule[8].proto='udp'
firewall.@rule[8].target='ACCEPT'
firewall.@include[0]=include
firewall.@include[0].path='/etc/firewall.user'
firewall.@zone[2]=zone
firewall.@zone[2].network='guest'
firewall.@zone[2].name='guest'
firewall.@zone[2].output='ACCEPT'
firewall.@zone[2].input='REJECT'
firewall.@zone[2].forward='REJECT'
firewall.@forwarding[1]=forwarding
firewall.@forwarding[1].dest='wan'
firewall.@forwarding[1].src='guest'
firewall.@rule[9]=rule
firewall.@rule[9].dest_port='67'
firewall.@rule[9].src='guest'
firewall.@rule[9].name='GuestDHCP'
firewall.@rule[9].target='ACCEPT'
firewall.@rule[9].proto='udp'
firewall.@rule[10]=rule
firewall.@rule[10].dest_port='53'
firewall.@rule[10].src='guest'
firewall.@rule[10].name='GuestDNS'
firewall.@rule[10].target='ACCEPT'
firewall.wg=rule
firewall.wg.name='Allow-WireGuard'
firewall.wg.src='wan'
firewall.wg.target='ACCEPT'
firewall.wg.dest_port='51820'
firewall.wg.family='ipv4'
firewall.wg.proto='udp'
firewall.@forwarding[2]=forwarding
firewall.@forwarding[2].dest='guest'
firewall.@forwarding[2].src='lan'
firewall.@rule[12]=rule
firewall.@rule[12].dest_port='51820'
firewall.@rule[12].src='guest'
firewall.@rule[12].name='TestWireguardGuest'
firewall.@rule[12].target='ACCEPT'
firewall.@rule[12].proto='udp'
firewall.@rule[12].enabled='0'
luci.main=core
luci.main.lang='auto'
luci.main.mediaurlbase='/luci-static/bootstrap'
luci.main.resourcebase='/luci-static/resources'
luci.main.ubuspath='/ubus/'
luci.flash_keep=extern
luci.flash_keep.uci='/etc/config/'
luci.flash_keep.dropbear='/etc/dropbear/'
luci.flash_keep.openvpn='/etc/openvpn/'
luci.flash_keep.passwd='/etc/passwd'
luci.flash_keep.opkg='/etc/opkg.conf'
luci.flash_keep.firewall='/etc/firewall.user'
luci.flash_keep.uploads='/lib/uci/upload/'
luci.languages=internal
luci.sauth=internal
luci.sauth.sessionpath='/tmp/luci-sessions'
luci.sauth.sessiontime='3600'
luci.ccache=internal
luci.ccache.enable='1'
luci.themes=internal
luci.themes.Bootstrap='/luci-static/bootstrap'
luci.apply=internal
luci.apply.rollback='90'
luci.apply.holdoff='4'
luci.apply.timeout='5'
luci.apply.display='1.5'
luci.diag=internal
luci.diag.dns='openwrt.org'
luci.diag.ping='openwrt.org'
luci.diag.route='openwrt.org'
luci.@command[0]=command
luci.@command[0].name='Lanciare iperf3'
luci.@command[0].command='iperf3 -s'
network.loopback=interface
network.loopback.ifname='lo'
network.loopback.proto='static'
network.loopback.ipaddr='127.0.0.1'
network.loopback.netmask='255.0.0.0'
network.globals=globals
network.globals.ula_prefix='fd4a:e543:7907::/48'
network.wan=interface
network.wan.ifname='eth1'
network.wan.proto='pppoe'
network.wan.password='***********'
network.wan.ipv6='auto'
network.wan.username='***********'
network.wan_eth1_dev=device
network.wan_eth1_dev.name='eth1'
network.wan_eth1_dev.macaddr='44:4E:6D:12:18:06'
network.wan6=interface
network.wan6.ifname='eth1'
network.wan6.proto='dhcpv6'
network.lan=interface
network.lan.type='bridge'
network.lan.proto='static'
network.lan.ipaddr='192.168.1.1'
network.lan.netmask='255.255.255.0'
network.lan.ip6assign='60'
network.lan.ifname='eth0.1'
network.lan_eth0_1_dev=device
network.lan_eth0_1_dev.name='eth0.1'
network.lan_eth0_1_dev.macaddr='44:4E:6D:12:18:05'
network.@switch[0]=switch
network.@switch[0].name='switch0'
network.@switch[0].reset='1'
network.@switch[0].enable_vlan='1'
network.@switch_vlan[0]=switch_vlan
network.@switch_vlan[0].device='switch0'
network.@switch_vlan[0].vlan='1'
network.@switch_vlan[0].vid='1'
network.@switch_vlan[0].ports='0t 1 4'
network.guest=interface
network.guest.proto='static'
network.guest.netmask='255.255.255.0'
network.guest.ipaddr='192.168.2.1'
network.guest.dns='1.1.1.1' '8.8.8.8'
network.guest.type='bridge'
network.guest.ifname='eth0.2'
network.@switch_vlan[1]=switch_vlan
network.@switch_vlan[1].device='switch0'
network.@switch_vlan[1].vlan='2'
network.@switch_vlan[1].vid='2'
network.@switch_vlan[1].ports='0t 3 2'
network.vpn=interface
network.vpn.proto='wireguard'
network.vpn.listen_port='51820'
network.vpn.addresses='192.168.9.1/24' 'fdf1:e8a1:8d3f:9::1/64'
network.vpn.private_key='********************'
network.@wireguard_vpn[0]=wireguard_vpn
network.@wireguard_vpn[0].description='PortatileLan'
network.@wireguard_vpn[0].public_key='********************'
network.@wireguard_vpn[0].allowed_ips='192.168.9.4/32'
network.@wireguard_vpn[0].route_allowed_ips='1'
network.@wireguard_vpn[1]=wireguard_vpn
network.@wireguard_vpn[1].route_allowed_ips='1'
network.@wireguard_vpn[1].public_key='********************'
network.@wireguard_vpn[1].description='Galaxy S8'
network.@wireguard_vpn[1].allowed_ips='192.168.9.3/24'
openvpn.custom_config=openvpn
openvpn.custom_config.enabled='0'
openvpn.custom_config.config='/etc/openvpn/my-vpn.conf'
openvpn.sample_server=openvpn
openvpn.sample_server.enabled='0'
openvpn.sample_server.port='1194'
openvpn.sample_server.proto='udp'
openvpn.sample_server.dev='tun'
openvpn.sample_server.ca='/etc/openvpn/ca.crt'
openvpn.sample_server.cert='/etc/openvpn/server.crt'
openvpn.sample_server.key='/etc/openvpn/server.key'
openvpn.sample_server.dh='/etc/openvpn/dh1024.pem'
openvpn.sample_server.server='10.8.0.0 255.255.255.0'
openvpn.sample_server.ifconfig_pool_persist='/tmp/ipp.txt'
openvpn.sample_server.keepalive='10 120'
openvpn.sample_server.compress='lzo'
openvpn.sample_server.persist_key='1'
openvpn.sample_server.persist_tun='1'
openvpn.sample_server.user='nobody'
openvpn.sample_server.status='/tmp/openvpn-status.log'
openvpn.sample_server.verb='3'
openvpn.sample_client=openvpn
openvpn.sample_client.enabled='0'
openvpn.sample_client.client='1'
openvpn.sample_client.dev='tun'
openvpn.sample_client.proto='udp'
openvpn.sample_client.remote='my_server_1 1194'
openvpn.sample_client.resolv_retry='infinite'
openvpn.sample_client.nobind='1'
openvpn.sample_client.persist_key='1'
openvpn.sample_client.persist_tun='1'
openvpn.sample_client.user='nobody'
openvpn.sample_client.ca='/etc/openvpn/ca.crt'
openvpn.sample_client.cert='/etc/openvpn/client.crt'
openvpn.sample_client.key='/etc/openvpn/client.key'
openvpn.sample_client.compress='lzo'
openvpn.sample_client.verb='3'
rpcd.@rpcd[0]=rpcd
rpcd.@rpcd[0].socket='/var/run/ubus.sock'
rpcd.@rpcd[0].timeout='30'
rpcd.@login[0]=login
rpcd.@login[0].username='root'
rpcd.@login[0].password='$p$root'
rpcd.@login[0].read='*'
rpcd.@login[0].write='*'
sqm.eth1=queue
sqm.eth1.interface='eth1'
sqm.eth1.qdisc_advanced='0'
sqm.eth1.linklayer='none'
sqm.eth1.upload='19500'
sqm.eth1.debug_logging='0'
sqm.eth1.verbosity='5'
sqm.eth1.qdisc='cake'
sqm.eth1.script='piece_of_cake.qos'
sqm.eth1.enabled='1'
sqm.eth1.download='85000'
sqm.@queue[1]=queue
sqm.@queue[1].debug_logging='0'
sqm.@queue[1].verbosity='5'
sqm.@queue[1].linklayer='none'
sqm.@queue[1].enabled='1'
sqm.@queue[1].qdisc='cake'
sqm.@queue[1].script='piece_of_cake.qos'
sqm.@queue[1].qdisc_advanced='0'
sqm.@queue[1].interface='br-guest'
sqm.@queue[1].download='40000'
sqm.@queue[1].upload='40000'
system.@system[0]=system
system.@system[0].hostname='OpenWrt'
system.@system[0].timezone='UTC'
system.@system[0].ttylogin='0'
system.@system[0].log_size='64'
system.@system[0].urandom_seed='0'
system.ntp=timeserver
system.ntp.enabled='1'
system.ntp.enable_server='0'
system.ntp.server='0.openwrt.pool.ntp.org' '1.openwrt.pool.ntp.org' '2.openwrt.pool.ntp.org' '3.openwrt.pool.ntp.org'
system.led_wan=led
system.led_wan.name='WAN'
system.led_wan.sysfs='fritz4020:green:wan'
system.led_wan.trigger='netdev'
system.led_wan.mode='link tx rx'
system.led_wan.dev='eth1'
system.led_lan=led
system.led_lan.name='LAN'
system.led_lan.sysfs='fritz4020:green:lan'
system.led_lan.trigger='switch0'
system.led_lan.port_mask='0x1E'
ucitrack.@network[0]=network
ucitrack.@network[0].init='network'
ucitrack.@network[0].affects='dhcp' 'radvd'
ucitrack.@wireless[0]=wireless
ucitrack.@wireless[0].affects='network'
ucitrack.@firewall[0]=firewall
ucitrack.@firewall[0].init='firewall'
ucitrack.@firewall[0].affects='luci-splash' 'qos' 'miniupnpd' 'sqm'
ucitrack.@olsr[0]=olsr
ucitrack.@olsr[0].init='olsrd'
ucitrack.@dhcp[0]=dhcp
ucitrack.@dhcp[0].init='dnsmasq'
ucitrack.@dhcp[0].affects='odhcpd'
ucitrack.@odhcpd[0]=odhcpd
ucitrack.@odhcpd[0].init='odhcpd'
ucitrack.@dropbear[0]=dropbear
ucitrack.@dropbear[0].init='dropbear'
ucitrack.@httpd[0]=httpd
ucitrack.@httpd[0].init='httpd'
ucitrack.@fstab[0]=fstab
ucitrack.@fstab[0].exec='/sbin/block mount'
ucitrack.@qos[0]=qos
ucitrack.@qos[0].init='qos'
ucitrack.@system[0]=system
ucitrack.@system[0].init='led'
ucitrack.@system[0].exec='/etc/init.d/log reload'
ucitrack.@system[0].affects='luci_statistics' 'dhcp'
ucitrack.@luci_splash[0]=luci_splash
ucitrack.@luci_splash[0].init='luci_splash'
ucitrack.@upnpd[0]=upnpd
ucitrack.@upnpd[0].init='miniupnpd'
ucitrack.@ntpclient[0]=ntpclient
ucitrack.@ntpclient[0].init='ntpclient'
ucitrack.@samba[0]=samba
ucitrack.@samba[0].init='samba'
ucitrack.@tinyproxy[0]=tinyproxy
ucitrack.@tinyproxy[0].init='tinyproxy'
ucitrack.@sqm[0]=sqm
ucitrack.@sqm[0].init='sqm'
uhttpd.main=uhttpd
uhttpd.main.listen_http='0.0.0.0:80' '[::]:80'
uhttpd.main.listen_https='0.0.0.0:443' '[::]:443'
uhttpd.main.redirect_https='1'
uhttpd.main.home='/www'
uhttpd.main.rfc1918_filter='1'
uhttpd.main.max_requests='3'
uhttpd.main.max_connections='100'
uhttpd.main.cert='/etc/uhttpd.crt'
uhttpd.main.key='/etc/uhttpd.key'
uhttpd.main.cgi_prefix='/cgi-bin'
uhttpd.main.lua_prefix='/cgi-bin/luci=/usr/lib/lua/luci/sgi/uhttpd.lua'
uhttpd.main.script_timeout='60'
uhttpd.main.network_timeout='30'
uhttpd.main.http_keepalive='20'
uhttpd.main.tcp_keepalive='1'
uhttpd.defaults=cert
uhttpd.defaults.days='730'
uhttpd.defaults.key_type='rsa'
uhttpd.defaults.bits='2048'
uhttpd.defaults.ec_curve='P-256'
uhttpd.defaults.country='ZZ'
uhttpd.defaults.state='Somewhere'
uhttpd.defaults.location='Unknown'
uhttpd.defaults.commonname='OpenWrt'
wireless.radio0=wifi-device
wireless.radio0.type='mac80211'
wireless.radio0.hwmode='11g'
wireless.radio0.path='platform/ahb/18100000.wmac'
wireless.radio0.htmode='HT20'
wireless.radio0.txpower='22'
wireless.radio0.channel='auto'
wireless.default_radio0=wifi-iface
wireless.default_radio0.device='radio0'
wireless.default_radio0.network='lan'
wireless.default_radio0.mode='ap'
wireless.default_radio0.key='********************'
wireless.default_radio0.ssid='OpenWrt - Eolo'
wireless.default_radio0.encryption='psk2'
wireless.default_radio0.wps_pushbutton='1'
wireless.wifinet1=wifi-iface
wireless.wifinet1.ssid='OpenWrt-Ospiti'
wireless.wifinet1.device='radio0'
wireless.wifinet1.mode='ap'
wireless.wifinet1.isolate='1'
wireless.wifinet1.network='guest'
wireless.wifinet1.key='********************'
wireless.wifinet1.wps_pushbutton='1'
wireless.wifinet1.encryption='psk2'```