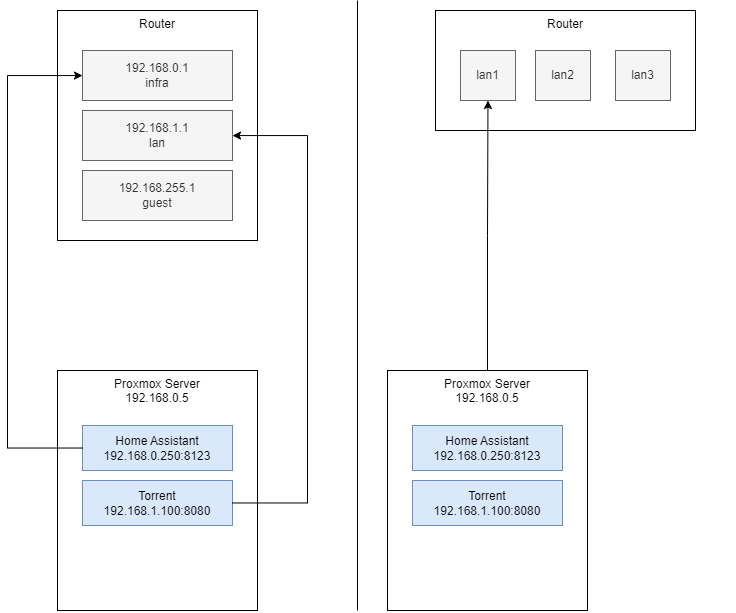
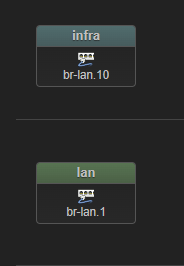
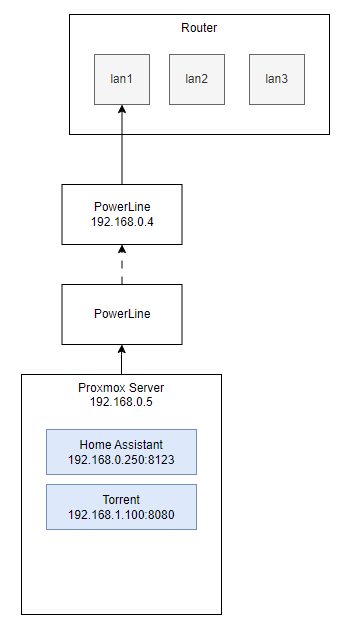
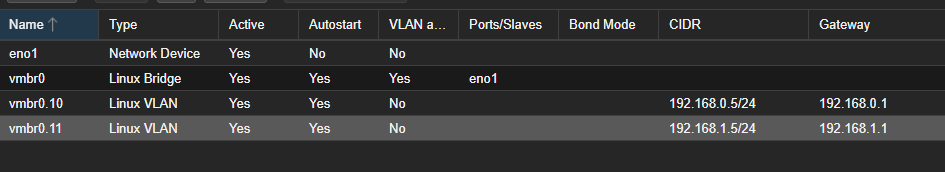
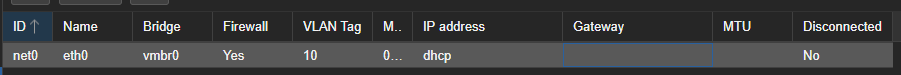
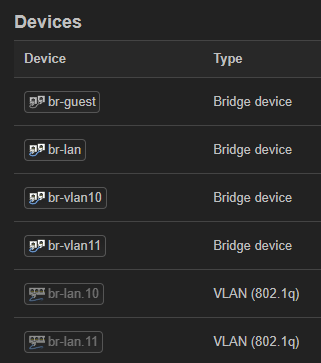
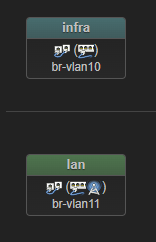
Just to clarify, OpenWrt runs on my ASUS AX53U Router; Proxmox has nothing to do with OpenWrt, i.e. there is no OpenWrt VM running on it or anything fancy. I just named Proxmox as it's the one system that has multiple IPs in my network. Here is a simple diagram; left is the loglical view, and on the right side is the physical view
This is the output you asked for. I plan on adding another subnet for IoT wifi connected devices in the future, but that's off topic here:
~# ubus call system board
{
"kernel": "5.10.176",
"hostname": "OpenWrt",
"system": "MediaTek MT7621 ver:1 eco:3",
"model": "ASUS RT-AX53U",
"board_name": "asus,rt-ax53u",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "22.03.5",
"revision": "r20134-5f15225c1e",
"target": "ramips/mt7621",
"description": "OpenWrt 22.03.5 r20134-5f15225c1e"
}
}
~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option packet_steering '1'
option ula_prefix 'fdd0:a84f:5d28::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'lan1'
list ports 'lan2'
list ports 'lan3'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'wan'
option proto 'dhcp'
option peerdns '0'
config interface 'wan6'
option device 'wan'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
config device
option type 'bridge'
option name 'br-guest'
config interface 'guest'
option device 'br-guest'
option proto 'static'
option ipaddr '192.168.255.1'
option netmask '255.255.255.0'
config interface 'infra'
option proto 'static'
option device 'br-lan'
option ipaddr '192.168.0.1'
option netmask '255.255.255.0'
~# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
# my internal DNS Server (AdGuard Home)
list server '192.168.0.204#53'
option rebind_protection '0'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'server'
option ra 'server'
option ra_slaac '1'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'guest'
option interface 'guest'
option start '100'
option limit '150'
option leasetime '12h'
# All my static leases redacted, for example:
config host
option dns '1'
option name 'HOST'
option ip '192.168.0.250'
option mac 'REDACTED'
config dhcp 'infra'
option interface 'infra'
option start '100'
option limit '150'
option leasetime '12h'
~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option synflood_protect '1'
option forward 'DROP'
config zone
option name 'guest'
option output 'ACCEPT'
list network 'guest'
option input 'REJECT'
option forward 'REJECT'
config zone
option name 'infra'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'infra'
config zone
option name 'lan'
list network 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'wan'
list network 'wan'
list network 'wan6'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option input 'DROP'
option forward 'DROP'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option proto 'icmp'
option family 'ipv4'
option target 'ACCEPT'
list icmp_type 'echo-request'
option src '*'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option proto 'icmp'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
list icmp_type 'bad-header'
list icmp_type 'destination-unreachable'
list icmp_type 'echo-reply'
list icmp_type 'echo-request'
list icmp_type 'neighbour-advertisement'
list icmp_type 'neighbour-solicitation'
list icmp_type 'packet-too-big'
list icmp_type 'router-advertisement'
list icmp_type 'router-solicitation'
list icmp_type 'time-exceeded'
list icmp_type 'unknown-header-type'
option src '*'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
# Exclude Caddy from DNS forwarding, to not intercept letsencrypt cert renewal
config redirect
option target 'DNAT'
option name 'Skip DNS Port Forwarding'
option src 'infra'
option src_dport '53'
option dest_ip '1.1.1.1'
option dest_port '53'
option src_ip '192.168.0.99'
config redirect
option name 'Forward LAN DNS'
option src 'lan'
option src_dport '53'
option dest 'infra'
option dest_ip '192.168.0.204'
option dest_port '53'
option src_ip '!192.168.0.204'
config redirect
option name 'Redirect INFRA DNS'
option src 'infra'
option src_ip '!192.168.0.204'
option src_dport '53'
option dest_ip '192.168.0.204'
option dest_port '53'
option dest 'infra'
config forwarding
option src 'lan'
option dest 'wan'
config forwarding
option src 'guest'
option dest 'wan'
config forwarding
option src 'infra'
option dest 'lan'
config forwarding
option src 'infra'
option dest 'wan'
config forwarding
option src 'lan'
option dest 'infra'
config rule
option name 'Guest DNS'
option src 'guest'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Guest DHCP'
list proto 'udp'
option src 'guest'
option target 'ACCEPT'
option dest_port '67-68'
config rule
option name 'Guest Block All'
option src 'guest'
option target 'DROP'
config nat
option name 'DNS MASQUERADE'
list proto 'tcp'
list proto 'udp'
option dest_ip '192.168.0.204'
option dest_port '53'
option target 'MASQUERADE'
option src 'infra'
option enabled '0'
Edit: I also thought I should mention: I tried VLAN configuration before, but the smallest change in the VLAN config of br-lan causes my connection to the router to drop and it resets the config after the 90s timeout. I'm connected to my router via WiFi in this instance, so I thought VLAN should not affect my client whatsoever. Guess I am wrong 

![]()