Howdy, I have an MR16 on 22.03.3 which I will call AP, and my opnsense router I will call R, and a VLAN capable switch.
The MR16 only has 1 ethernet port
AP is in port 48 (Tagged 50, UnTagged 1)
R is in port 5 (Taged 50, UnTagged 1)
I created an interface in opnsense for VLAN 50 on 192.168.94.1
My VLAN 1 interface is on 192.168.1.1
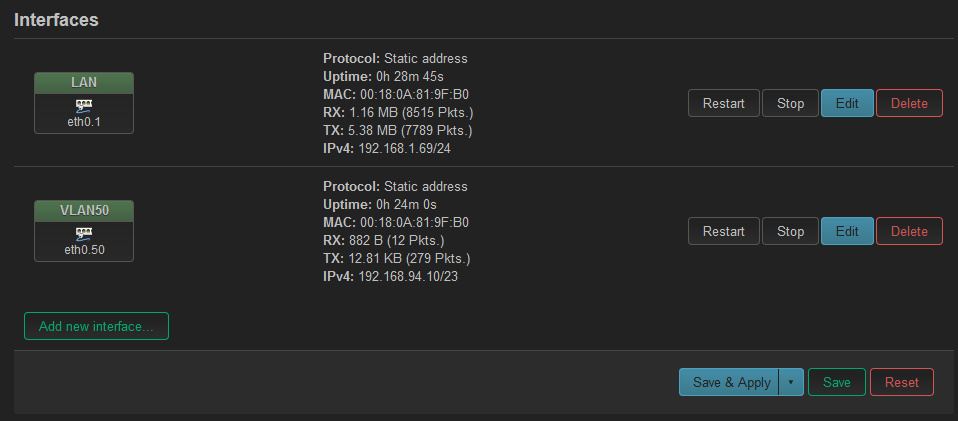
On the AP my interfaces are:
LAN at 192.168.1.69/24 using eth0.1
VLAN50 at 192.168.94.10/23 using eth0.50
I have 2 SSIDs one for each AP interface
As is, I've verified via the AP that the VLAN portion is working;
I am able to ping 192.168.1.1, and 192.168.94.1 via "ping -I eth0.X Y".
The issue I think I've run up against here is routing as I've broken both SSID's client's ability to communicate with the router/DHCP.
They are unable to ping either the AP's or Router's interfaces.
I'm not sure where I broke it, and I am at a loss for how to proceed.
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
Remember to redact passwords, MAC addresses and any public IP addresses you may have:
cat /etc/config/network
cat /etc/config/wireless
cat /etc/config/dhcp
cat /etc/config/firewall
Sorry for the delay
Network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.69'
option gateway '192.168.1.1'
list dns '192.168.1.1'
option device 'eth0.1'
config device
option name 'wlan1'
option ipv6 '0'
config device
option name 'wlan0'
option ipv6 '0'
config device
option name 'eth0'
config interface 'vlan50'
option type 'bridge'
option device 'eth0.50'
option proto 'static'
list ipaddr '192.168.94.10/23'
option gateway '192.168.94.1'
option defaultroute '0'
Wireless:
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:11.0'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'SSID_1'
option encryption 'psk2'
option key '*********'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:12.0'
option cell_density '0'
option htmode 'HT40'
option country 'US'
option txpower '14'
option channel '149'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'ap'
option encryption 'psk2'
option key '*********'
option network 'lan'
option wmm '0'
option skip_inactivity_poll '1'
option disassoc_low_ack '0'
option ssid 'Disabled'
option ieee80211r '1'
option mobility_domain '4F57'
option ft_over_ds '1'
option ft_psk_generate_local '1'
option disabled '1'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option ssid 'SSID_50'
option encryption 'psk2'
option key '*********'
option network 'vlan50'
option isolate '1'
DHCP:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.1.1'
config relay
option interface 'lan'
option local_addr '192.168.1.69'
option server_addr '192.168.1.1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
option dynamicdhcp '0'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vlan50'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
The network file has several issues...
Starting with the lan (VLAN 1)... if you want this to work on wifi, you need to define a bridge for it. It will look like this:
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.69'
option gateway '192.168.1.1'
list dns '192.168.1.1'
option device 'br-lan'
next, delete all of these:
For VLAN50, you'll need to do the same bridge, but it must be defined outside the network interface. It should also be unmanaged (no address) and the default route line should be removed. it will look like this when you're done:
config device
option name 'br-vlan50'
option type 'bridge'
list ports 'eth0.50'
config interface 'vlan50'
option device 'br-vlan50'
option proto 'none'
The relay should be deleted in the DHCP file
You can remove vlan50 from the networks covered in the lan firewall zone.
After making those changes, restart the AP and see if it works.
I've made the suggested changes, and it doesn't look like its coming back up. I will investigate to confirm
I've verified what is happening.
Connecting to SSID_1 is actually routing traffic through vlan50, but DHCP works IP's are assigned in the 192.168.94.100-200 range.
Connecting to SSID_50 yields no results.
Because the AP was sending traffic down vlan50 Its 192.168.1.69 interface was not accessible.
Here are the updated configs
Network:
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
configure device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.1.69'
option gateway '192.168.1.1'
list dns '192.168.1.1'
option device 'br-lan'
configure device
option name 'br-vlan50'
option type 'bridge'
list ports 'eth0.50'
config interface 'vlan50'
option device 'br-vlan50'
option proto 'none'
Wireless:
config wifi-device 'radio0'
option type 'mac80211'
option channel '11'
option hwmode '11g'
option path 'pci0000:00/0000:00:11.0'
option htmode 'HT20'
option cell_density '0'
config wifi-iface 'default_radio0'
option device 'radio0'
option network 'lan'
option mode 'ap'
option ssid 'SSID_1'
option encryption 'psk2'
option key '**********'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11a'
option path 'pci0000:00/0000:00:12.0'
option cell_density '0'
option htmode 'HT40'
option country 'US'
option txpower '14'
option channel '149'
config wifi-iface 'wifinet2'
option device 'radio1'
option mode 'ap'
option encryption 'psk2'
option key '**********'
option network 'lan'
option wmm '0'
option skip_inactivity_poll '1'
option disassoc_low_ack '0'
option ssid 'Disabled'
option ieee80211r '1'
option mobility_domain '4F57'
option ft_over_ds '1'
option ft_psk_generate_local '1'
option disabled '1'
config wifi-iface 'wifinet3'
option device 'radio1'
option mode 'ap'
option ssid 'SSID_50'
option encryption 'psk2'
option key '**********'
option network 'vlan50'
option isolate '1'
DHCP:
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
list server '192.168.1.1'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option ignore '1'
option dynamicdhcp '0'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
Firewall:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled 'false'
config include
option path '/etc/firewall.user'
I think I see what is wrong with VLAN 1... it is untagged on your upstream switch, which means that br-lan is wrong... it should be eth0, not eth0.1
configure device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
That should fix VLAN 1 so that it works properly.
With VLAN 50, I don't see any reason you'd have issues.
Let's verify that the upstream is working properly using wired connections... Using your switch (assuming you have some extra ports), the best way to verify the VLAN operation is to set 2 access ports -- one for VLAN 1 and the other for VLAN 50 (by access ports, they will only have one network assigned, untagged). Then plug a computer into the access port for VLAN 1 and check the IP address it gets and the network connectivity. Then, move the connection to the port for VLAN 50 and do the same. Do they both work as expected?
You know what, I misremembered, I just verified on the switch it was tagged for 1, and 50 on both port 5 and port 48.
I will also go verify the VLANs working directly on the switch
ok... good. then leave eth0.1 as it is.
But do the test with the wired connections to each VLAN to verify it is working properly.
I have verified VLANs are working as intended directly on switch.
I used port 41 (Untagged 50)
and port 38 (UnTagged 1)
ok... so now if you connect to SSID_1, what do you get for the DHCP lease?
then repeat for SSID_50.
I currently have the AP in failsafe, without any network changes I don't think the results will differ.
Before I put it into failsafe port 48, and 5 had VLAN 1, and 50 Tagged, so no change.
SSID_1 gave a DHCP lease for VLAN50, and SSID_50 failed to give a lease.
If you insist I can reboot the AP and verify
Yes, it is worth testing again.
Also, do you have any other APs broadcasting those same SSIDs?
The other thing to consider is that you have 802.11r and a whole bunch of other related options enabled on your SSIDs. This can cause connectivity problems (not all devices play well with fast roaming). You may want to consider removing all of those options if you are still unable to connect properly.
I will reboot the AP to verify, and no I do not have any other APs broadcasting the same SSIDs
I have verified the results are unchanged.
SSID_1 Clients are given DHCP leases for vlan50
SSID_50 Clients are not given a lease and do not have connectivity to 192.168.1.0/24
I honestly don't understand how that could happen.
I'd suggest that you reset the AP to defaults and start over. Start by only setting up VLAN 1 for the dumb AP config (turn off the DHCP server, set the static IP and make sure br-lan is using eth0.1, set the SSID + password and enable wifi). Then see what happens with devices connected to that VLAN.
will do, not much to lose
So yeah, that fixed it. For w/e reason the AP didn't want to factory reset.
I reflashed the AP, set everything exactly like we had here anew and it's working.
Thank you for your time
Great! Glad it is working now.
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.