Hello !
I am a new Openwrt user.
What I want is to have a router connected to a vpn provider (NordPN) in order to have a secure connection for the device plugged to the router.
Device <-> Router <-> ISP Modem - Router <-> VPN Provider <-> Internet
I have put OpenWrt 22.03.2 r19803-9a599fee93 on a Raspberry Pi 4 Model B.
I used this image : https://downloads.openwrt.org/releases/22.03.3/targets/bcm27xx/bcm2711/openwrt-22.03.3-bcm27xx-bcm2711-rpi-4-squashfs-sysupgrade.img.gz
What i have done first is to transform the Raspberry in a basic router with 2 ethernet ports (one from the Raspberry Pi and another with an ethernet - usb adapter.
eth0 for the lan
eth1 for the wan
It works for the basic router configuration but the problem I encounter comes from the vpn side.
I followed exactly the tutorial given on the NordVPN web site : https://support.nordvpn.com/Connectivity/Router/1047411192/OpenWrt-CI-setup-with-NordVPN.htm
Unfortunately, it doesn't work.
I tried many things but nothing works.
I tried to ping google dns server 8.8.8.8 but no response.
So I supposed the vpn connection doesn't work but I don't know why.
Is anyone can help me ?
Here are my configuration files
/etc/config/network
GNU nano 7.1 network
1
2 config interface 'loopback'
3 option device 'lo'
4 option proto 'static'
5 option ipaddr '127.0.0.1'
6 option netmask '255.0.0.0'
7
8 config globals 'globals'
9 option ula_prefix 'fdbc:f3c8:9afa::/48'
10
11 config device
12 option name 'br-lan'
13 option type 'bridge'
14 list ports 'eth0'
15
16 config interface 'lan'
17 option device 'br-lan'
18 option proto 'static'
19 option ipaddr '192.168.1.200'
20 option netmask '255.255.255.0'
21 list dns '8.8.8.8'
22
23 config interface 'wan'
24 option proto 'dhcp'
25 option device 'eth1'
26
27 config interface 'nordvpntun'
28 option proto 'none'
29 option device 'tun0'
30
31
/etc/config/firewall
GNU nano 7.1 firewall
1
2 config defaults
3 option input 'ACCEPT'
4 option output 'ACCEPT'
5 option forward 'REJECT'
6 option synflood_protect '1'
7
8 config zone
9 option name 'lan'
10 list network 'lan'
11 option input 'ACCEPT'
12 option output 'ACCEPT'
13 option forward 'ACCEPT'
14
15 config zone
16 option name 'wan'
17 list network 'wan'
18 list network 'wan6'
19 option input 'REJECT'
20 option output 'ACCEPT'
21 option forward 'REJECT'
22 option masq '1'
23 option mtu_fix '1'
24
25 config forwarding
26 option src 'lan'
27 option dest 'wan'
28
29 config rule
30 option name 'Allow-DHCP-Renew'
31 option src 'wan'
32 option proto 'udp'
33 option dest_port '68'
34 option target 'ACCEPT'
35 option family 'ipv4'
36
37 config rule
38 option name 'Allow-Ping'
39 option src 'wan'
40 option proto 'icmp'
41 option icmp_type 'echo-request'
42 option family 'ipv4'
43 option target 'ACCEPT'
44
45 config rule
46 option name 'Allow-IGMP'
47 option src 'wan'
48 option proto 'igmp'
49 option family 'ipv4'
50 option target 'ACCEPT'
51
52 config rule
53 option name 'Allow-DHCPv6'
54 option src 'wan'
55 option proto 'udp'
56 option dest_port '546'
57 option family 'ipv6'
58 option target 'ACCEPT'
59
60 config rule
61 option name 'Allow-MLD'
62 option src 'wan'
63 option proto 'icmp'
64 option src_ip 'fe80::/10'
65 list icmp_type '130/0'
66 list icmp_type '131/0'
67 list icmp_type '132/0'
68 list icmp_type '143/0'
69 option family 'ipv6'
70 option target 'ACCEPT'
71
72 config rule
73 option name 'Allow-ICMPv6-Input'
74 option src 'wan'
75 option proto 'icmp'
76 list icmp_type 'echo-request'
77 list icmp_type 'echo-reply'
78 list icmp_type 'destination-unreachable'
79 list icmp_type 'packet-too-big'
80 list icmp_type 'time-exceeded'
81 list icmp_type 'bad-header'
82 list icmp_type 'unknown-header-type'
83 list icmp_type 'router-solicitation'
84 list icmp_type 'neighbour-solicitation'
85 list icmp_type 'router-advertisement'
86 list icmp_type 'neighbour-advertisement'
87 option limit '1000/sec'
88 option family 'ipv6'
89 option target 'ACCEPT'
90
91 config rule
92 option name 'Allow-ICMPv6-Forward'
93 option src 'wan'
94 option dest '*'
95 option proto 'icmp'
96 list icmp_type 'echo-request'
97 list icmp_type 'echo-reply'
98 list icmp_type 'destination-unreachable'
99 list icmp_type 'packet-too-big'
100 list icmp_type 'time-exceeded'
101 list icmp_type 'bad-header'
102 list icmp_type 'unknown-header-type'
103 option limit '1000/sec'
104 option family 'ipv6'
105 option target 'ACCEPT'
106
107 config rule
108 option name 'Allow-IPSec-ESP'
109 option src 'wan'
110 option dest 'lan'
111 option proto 'esp'
112 option target 'ACCEPT'
113
114 config rule
115 option name 'Allow-ISAKMP'
116 option src 'wan'
117 option dest 'lan'
118 option dest_port '500'
119 option proto 'udp'
120 option target 'ACCEPT'
121
122 config zone
123 option name 'vpnfirewall'
124 option input 'REJECT'
125 option output 'ACCEPT'
126 option forward 'REJECT'
127 option masq '1'
128 option mtu_fix '1'
129 list network 'nordvpntun'
130
131 config forwarding
132 option src 'lan'
133 option dest 'vpnfirewall'
/etc/config/dhcp
GNU nano 7.1 dhcp
1
2 config dnsmasq
3 option domainneeded '1'
4 option localise_queries '1'
5 option rebind_protection '1'
6 option rebind_localhost '1'
7 option local '/lan/'
8 option domain 'lan'
9 option expandhosts '1'
10 option authoritative '1'
11 option readethers '1'
12 option leasefile '/tmp/dhcp.leases'
13 option localservice '1'
14 option ednspacket_max '1232'
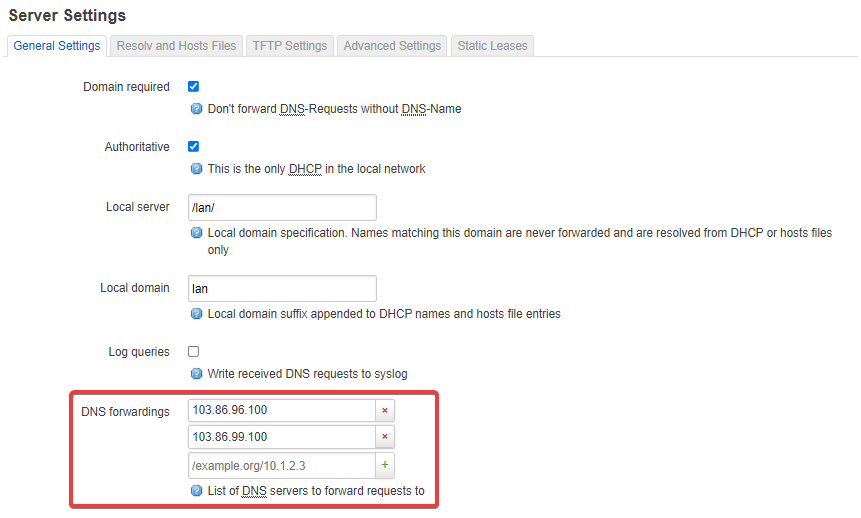
15 list server '103.86.96.100'
16 list server '103.86.99.100'
17 option noresolv '1'
18
19 config dhcp 'lan'
20 option interface 'lan'
21 option leasetime '12h'
22 option dhcpv4 'server'
23 list ra_flags 'managed-config'
24 list ra_flags 'other-config'
25 option ra 'hybrid'
26 option dhcpv6 'hybrid'
27 option start '201'
28 option limit '50'
29
30 config dhcp 'wan'
31 option interface 'wan'
32 option ignore '1'
33
34 config odhcpd 'odhcpd'
35 option maindhcp '0'
36 option leasefile '/tmp/hosts/odhcpd'
37 option leasetrigger '/usr/sbin/odhcpd-update'
38 option loglevel '4'
/etc/config/openvpn
GNU nano 7.1 openvpn
1
2 config openvpn 'custom_config'
3 option config '/etc/openvpn/my-vpn.conf'
4
5 config openvpn 'sample_server'
6 option port '1194'
7 option proto 'udp'
8 option dev 'tun'
9 option ca '/etc/openvpn/ca.crt'
10 option cert '/etc/openvpn/server.crt'
11 option key '/etc/openvpn/server.key'
12 option dh '/etc/openvpn/dh2048.pem'
13 option server '10.8.0.0 255.255.255.0'
14 option ifconfig_pool_persist '/tmp/ipp.txt'
15 option keepalive '10 120'
16 option persist_key '1'
17 option persist_tun '1'
18 option user 'nobody'
19 option status '/tmp/openvpn-status.log'
20 option verb '3'
21
22 config openvpn 'sample_client'
23 option client '1'
24 option dev 'tun'
25 option proto 'udp'
26 list remote 'my_server_1 1194'
27 option resolv_retry 'infinite'
28 option nobind '1'
29 option persist_key '1'
30 option persist_tun '1'
31 option user 'nobody'
32 option ca '/etc/openvpn/ca.crt'
33 option cert '/etc/openvpn/client.crt'
34 option key '/etc/openvpn/client.key'
35 option verb '3'
36
37 config openvpn 'nordvpn_fr'
38 option config '/etc/openvpn/nordvpn_fr.ovpn'
39 option enabled '1'
/etc/openvpn/nordvpn_fr.ovpn
GNU nano 7.1 nordvpn_fr.ovpn
1 client
2 dev tun
3 proto udp
4 remote 185.61.156.24 1194
5 resolv-retry infinite
6 remote-random
7 nobind
8 tun-mtu 1500
9 tun-mtu-extra 32
10 mssfix 1450
11 persist-key
12 persist-tun
13 ping 15
14 ping-restart 0
15 ping-timer-rem
16 reneg-sec 0
17 comp-lzo no
18 verify-x509-name CN=fr906.nordvpn.com
19
20 remote-cert-tls server
21
22 auth-user-pass /etc/openvpn/nordvpn_fr.auth
23 verb 3
24 pull
25 fast-io
26 cipher AES-256-CBC
27 auth SHA512
28 <ca>
29 -----BEGIN CERTIFICATE-----
30-----END CERTIFICATE-----
58 </ca>
59 key-direction 1
60 <tls-auth>
61 #
62 # 2048 bit OpenVPN static key
63 #
64 -----BEGIN OpenVPN Static key V1-----
81 -----END OpenVPN Static key V1-----
82 </tls-auth>
83