@psherman
Starting a clean configuration of Wireguard on OpenWrt 22.03.2
Already installed from Luci -> System -> Software
wireguard-tools 1.0.20210424-3
luci-app-wireguard git-21.322.66896-8ae208d
luci-proto-wireguard git-22.327.45657-14403fe
qrencode 4.1.1-1
Following this guide:
root@OpenWrt:~# WG_IF="vpn"
root@OpenWrt:~# WG_PORT="51820"
root@OpenWrt:~# WG_ADDR="192.168.9.1/24"
root@OpenWrt:~# WG_ADDR6="fdf1:e8a1:8d3f:9::1/64"
root@OpenWrt:~# umask go=
root@OpenWrt:~# wg genkey | tee wgserver.key | wg pubkey > wgserver.pub
root@OpenWrt:~# wg genkey | tee wgclient.key | wg pubkey > wgclient.pub
root@OpenWrt:~# wg genpsk > wgclient.psk
root@OpenWrt:~# WG_KEY="$(cat wgserver.key)"
root@OpenWrt:~# WG_PSK="$(cat wgclient.psk)"
root@OpenWrt:~# WG_PUB="$(cat wgclient.pub)"
root@OpenWrt:~# uci rename firewall.@zone[0]="lan"
root@OpenWrt:~# uci rename firewall.@zone[1]="wan"
root@OpenWrt:~# uci del_list firewall.lan.network="${WG_IF}"
root@OpenWrt:~# uci add_list firewall.lan.network="${WG_IF}"
root@OpenWrt:~# uci -q delete firewall.wg
root@OpenWrt:~# uci set firewall.wg="rule"
root@OpenWrt:~# uci set firewall.wg.name="Allow-WireGuard"
root@OpenWrt:~# uci set firewall.wg.src="wan"
root@OpenWrt:~# uci set firewall.wg.dest_port="${WG_PORT}"
root@OpenWrt:~# uci set firewall.wg.proto="udp"
root@OpenWrt:~# uci set firewall.wg.target="ACCEPT"
root@OpenWrt:~# uci commit firewall
root@OpenWrt:~# /etc/init.d/firewall restart
root@OpenWrt:~# uci -q delete network.${WG_IF}
root@OpenWrt:~# uci set network.${WG_IF}="interface"
root@OpenWrt:~# uci set network.${WG_IF}.proto="wireguard"
root@OpenWrt:~# uci set network.${WG_IF}.private_key="${WG_KEY}"
root@OpenWrt:~# uci set network.${WG_IF}.listen_port="${WG_PORT}"
root@OpenWrt:~# uci add_list network.${WG_IF}.addresses="${WG_ADDR}"
root@OpenWrt:~# uci add_list network.${WG_IF}.addresses="${WG_ADDR6}"
root@OpenWrt:~# uci -q delete network.wgclient
root@OpenWrt:~# uci set network.wgclient="wireguard_${WG_IF}"
root@OpenWrt:~# uci set network.wgclient.public_key="${WG_PUB}"
root@OpenWrt:~# uci set network.wgclient.preshared_key="${WG_PSK}"
root@OpenWrt:~# uci add_list network.wgclient.allowed_ips="${WG_ADDR%.*}.2/32"
root@OpenWrt:~# uci add_list network.wgclient.allowed_ips="${WG_ADDR6%:*}:2/128"
root@OpenWrt:~# uci commit network
root@OpenWrt:~# /etc/init.d/network restart
'radio0' is disabled
Results
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd8d:7220:16c4::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option delegate '0'
config interface 'WAN'
option proto 'dhcp'
option device 'eth1'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'vpn'
option proto 'wireguard'
option private_key 'private_key_removed'
option listen_port '51820'
list addresses '192.168.9.1/24'
list addresses 'fdf1:e8a1:8d3f:9::1/64'
config wireguard_vpn 'wgclient'
option public_key 'public_key_removed'
option preshared_key 'preshared_key_removed'
list allowed_ips '192.168.9.2/32'
list allowed_ips 'fdf1:e8a1:8d3f:9::2/128'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'vpn'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'WAN'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'plex2022'
option src 'wan'
option src_dport '32400'
option dest_ip '192.168.1.243'
option dest_port '32400'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'torrents'
option src 'wan'
option src_dport '64974'
option dest_ip '192.168.1.123'
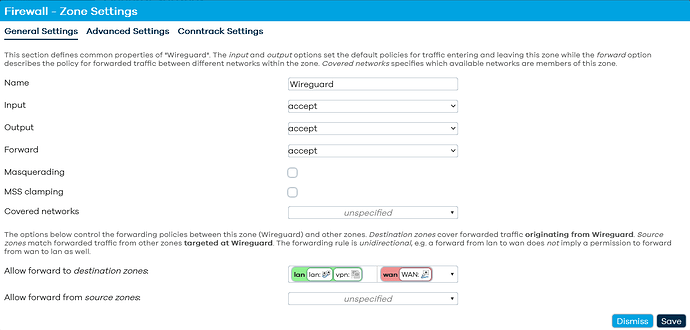
config zone
option name 'Wireguard'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'Wireguard'
option dest 'lan'
config forwarding
option src 'Wireguard'
option dest 'wan'
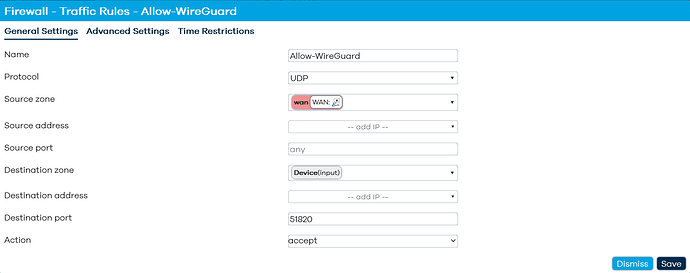
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
rebooted firewall
I haven't made any changes at this time. I did notice something that doesn't seem right looking at Luci
Network ->Interfaces-> VPN -> General Settings
Protocol - Wireguard VPN
Private Key - Populated
Public Key - Populated
Listen Port - 51820
IP Addresses - 192.168.9.1/24
fdf1:e8a1:8d3f:9::1/64
Network ->Interfaces-> VPN -> Edit Peer
Public Key -> Populated (but a different key than under General Settings)
Allowed IPs - 192.168.9.2/32
fdf1:e8a1:8d3f:9::2/128
Route Allowed IPs (Should this be checked?)
Endpoint Host - blank
Endpoint Port - 51820
Persistent Keep Alive 0
To get a QR, I need to add the Private Key to the Peer setting.
Added PK to get a QR code
QR code now has the same Public Key as key under General settings.
Scanned QR Code Android WG app
Public Key matches key in General Settings
Preshared key matches key under Edit Peer
saved profile
rebooted firewall, because why not?
On Phone: Turned on Wireguard Profile
Received an actual response this time
root@OpenWrt:~# wg show
interface: vpn
public key: same Public Key as key under General settings.
private key: (hidden)
listening port: 51820
peer: Same key shown in Edit Peer, but not the same as Public Key under General Settings
preshared key: (hidden)
allowed ips: 192.168.9.2/32, fdf1:e8a1:8d3f:9::2/128
If I make the public key under Edit Peers the same as under General Settings
Reboot
It doesn't complete the handshake to connect
Thoughts?