Hello,
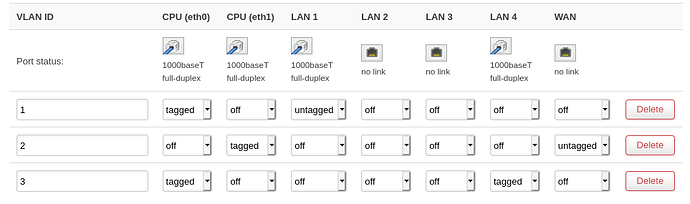
I want to create new VLAN (ID 3), assign this VLan to the port 4 and create a WiFi network in this same VLan.
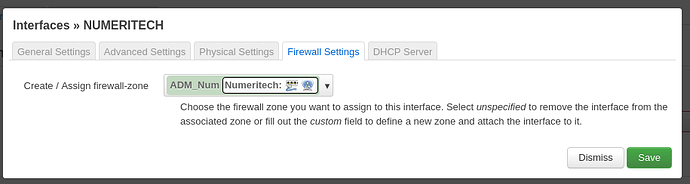
My config :
I can connect to the WiFi network and access to my router but I have an other equipment on this network and I can't connect to this equipment.
Someone to help me and explain where is the mistake ?
I change to untagged but no change
trendy
January 13, 2021, 2:06pm
8
Please run the following commands (copy-paste the whole block) and paste the output here, using the "Preformatted text </> " button:
ubus call system board; \
uci export network; uci export wireless; \
uci export dhcp; uci export firewall; \
head -n -0 /etc/firewall.user; \
ip -4 addr ; ip -4 ro li tab all ; ip -4 ru; \
ls -l /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/* ; head -n -0 /etc/resolv.* /tmp/resolv.* /tmp/resolv.*/*
{
"kernel": "4.14.209",
"hostname": "OpenWrt",
"system": "ARMv7 Processor rev 1 (v7l)",
"model": "Linksys WRT3200ACM",
"board_name": "linksys,rango",
"release": {
"distribution": "OpenWrt",
"version": "19.07.5",
"revision": "r11257-5090152ae3",
"target": "mvebu/cortexa9",
"description": "OpenWrt 19.07.5 r11257-5090152ae3"
}
}
package network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix ''
config interface 'lan'
option type 'bridge'
option ifname 'eth0.1'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.2.1'
list dns '192.168.2.17'
config interface 'Numeritech'
option type 'bridge'
option ifname 'eth0.4'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.3.1'
config interface 'wan'
option ifname 'eth1.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth1.2'
option proto 'dhcpv6'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '3 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '4 6t'
option vid '2'
config interface 'wwan'
option proto 'dhcp'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0 5t'
package wireless
config wifi-device 'radio0'
option type 'mac80211'
option channel '36'
option hwmode '11a'
option path 'soc/soc:pcie/pci0000:00/0000:00:01.0/0000:01:00.0'
option htmode 'VHT80'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option key ''
option ssid 'OpenWrt-5GHz'
option encryption 'psk2'
option network 'lan'
config wifi-device 'radio1'
option type 'mac80211'
option hwmode '11g'
option path 'soc/soc:pcie/pci0000:00/0000:00:02.0/0000:02:00.0'
option htmode 'HT40'
option channel '3'
config wifi-iface 'default_radio1'
option device 'radio1'
option mode 'ap'
option key ''
option encryption 'psk2'
option ssid 'ADMNumeritech'
option hidden '1'
option network 'ADM_Numeritech Numeritech'
config wifi-device 'radio2'
option type 'mac80211'
option path 'platform/soc/soc:internal-regs/f10d8000.sdhci/mmc_host/mmc0/mmc0:0001/mmc0:0001:1'
option hwmode '11g'
option channel 'auto'
config wifi-iface 'default_radio2'
option device 'radio2'
option network 'lan'
option mode 'ap'
option ssid 'OpenWrt'
option key ''
option encryption 'psk2'
config wifi-iface 'wifinet3'
option ssid 'Bbox'
option device 'radio2'
option mode 'sta'
option key ''
option encryption 'psk2'
option network 'wwan'
package dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option localservice '1'
option domain 'numeritech.lan'
config dhcp 'lan'
option interface 'lan'
option start '100'
option leasetime '12h'
option dhcpv6 'server'
option ra 'server'
option ra_management '1'
option limit '170'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'ADM_Numeritech'
option leasetime '12h'
option interface 'ADM_Numeritech'
option start '200'
option limit '230'
config dhcp 'Numeritech'
option leasetime '12h'
option interface 'Numeritech'
option start '200'
option limit '30'
package firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
option log '1'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6 wwan'
option log '1'
option input 'ACCEPT'
option forward 'ACCEPT'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow from wan'
option target 'ACCEPT'
option src '*'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config redirect
option dest_port '443'
option src 'wan'
option name 'Redirect to RevProxy'
option src_dport '443'
option target 'DNAT'
option dest_ip '192.168.2.18'
option dest 'lan'
config redirect
option dest_port '80'
option src 'wan'
option name 'Redirect to RevProxy 80'
option src_dport '80'
option target 'DNAT'
option dest_ip '192.168.2.18'
option dest 'lan'
config rule
option dest 'wan'
option target 'DROP'
option name 'Block Camera To WAN'
list src_ip '192.168.2.175'
option enabled '0'
config zone
option name 'ADM_Num'
option input 'ACCEPT'
option forward 'ACCEPT'
option output 'ACCEPT'
option network 'Numeritech'
list device 'br-Numeritech'
# This file is interpreted as shell script.
# Put your custom iptables rules here, they will
# be executed with each firewall (re-)start.
# Internal uci firewall chains are flushed and recreated on reload, so
# put custom rules into the root chains e.g. INPUT or FORWARD or into the
# special user chains, e.g. input_wan_rule or postrouting_lan_rule.
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
8: br-Numeritech: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.3.1/24 brd 192.168.3.255 scope global br-Numeritech
valid_lft forever preferred_lft forever
10: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
inet 192.168.2.1/24 brd 192.168.2.255 scope global br-lan
valid_lft forever preferred_lft forever
13: wlan2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000
inet 192.168.1.92/24 brd 192.168.1.255 scope global wlan2
valid_lft forever preferred_lft forever
default via 192.168.1.254 dev wlan2 src 192.168.1.92
192.168.1.0/24 dev wlan2 scope link src 192.168.1.92
192.168.2.0/24 dev br-lan scope link src 192.168.2.1
192.168.3.0/24 dev br-Numeritech scope link src 192.168.3.1
broadcast 127.0.0.0 dev lo table local scope link src 127.0.0.1
local 127.0.0.0/8 dev lo table local scope host src 127.0.0.1
local 127.0.0.1 dev lo table local scope host src 127.0.0.1
broadcast 127.255.255.255 dev lo table local scope link src 127.0.0.1
broadcast 192.168.1.0 dev wlan2 table local scope link src 192.168.1.92
local 192.168.1.92 dev wlan2 table local scope host src 192.168.1.92
broadcast 192.168.1.255 dev wlan2 table local scope link src 192.168.1.92
broadcast 192.168.2.0 dev br-lan table local scope link src 192.168.2.1
local 192.168.2.1 dev br-lan table local scope host src 192.168.2.1
broadcast 192.168.2.255 dev br-lan table local scope link src 192.168.2.1
broadcast 192.168.3.0 dev br-Numeritech table local scope link src 192.168.3.1
local 192.168.3.1 dev br-Numeritech table local scope host src 192.168.3.1
broadcast 192.168.3.255 dev br-Numeritech table local scope link src 192.168.3.1
0: from all lookup local
32766: from all lookup main
32767: from all lookup default
ls: /tmp/resolv.*/*: No such file or directory
lrwxrwxrwx 1 root root 16 Dec 6 08:31 /etc/resolv.conf -> /tmp/resolv.conf
-rw-r--r-- 1 root root 43 Jan 13 15:02 /tmp/resolv.conf
-rw-r--r-- 1 root root 189 Jan 13 15:02 /tmp/resolv.conf.auto
==> /etc/resolv.conf <==
search numeritech.lan
nameserver 127.0.0.1
==> /tmp/resolv.conf <==
search numeritech.lan
nameserver 127.0.0.1
==> /tmp/resolv.conf.auto <==
# Interface lan
nameserver 192.168.2.17
# Interface wwan
nameserver 192.168.1.254
search lan
head: /tmp/resolv.*/*: No such file or directory
root@OpenWrt:~#
mk24
January 13, 2021, 2:12pm
10
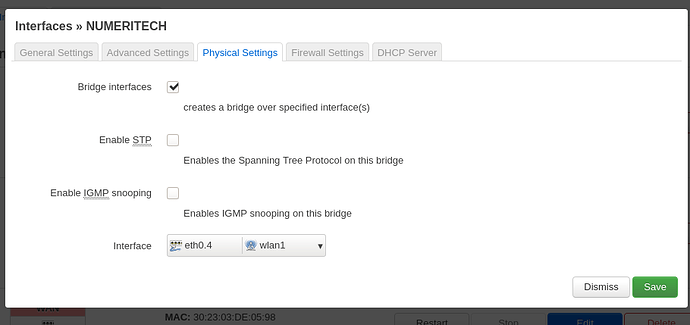
Your physical setting is eth0.4 but the VLAN number in the switch is 3. That will not work.
There is no firewall forward from the new numeritech zone to wan. This is necessary if you want the new network to have Internet access.
Convention is to use short interface names all lowercase. The entire name in the kernel including 'br-' that UCI adds needs to be 15 characters or less. LUCI shows them in uppercase which is a design choice I don't agree with.
trendy
January 13, 2021, 2:13pm
11
juicestyle:
option vid '3'
juicestyle:
option ifname 'eth0.4'
Mismatch of the vlans.
juicestyle:
option limit '230'
Change that in dhcp settings of the interface to 30, it is the number of the leases, not the last IP to use.
1 Like
I don't want internet on this interface.
mk24
January 13, 2021, 2:17pm
13
The SSID can be practically any text you want-- it will appear that way on users' devices. But your internal network and zone names should be lowercase to avoid confusion.
After change ifname that's work.
For the second thing :
trendy
January 13, 2021, 2:23pm
15
If your problem is solved, please consider marking this topic as [Solved]. See How to mark a topic as [Solved] for a short how-to.
Not really ...
Why since my LAN (192.168.2.0/24) I can access to the 192.168.3.0/24 network?
I want isolate two network
trendy
January 13, 2021, 2:27pm
17
Because you allow all forwards. Change it to REJECT and create forwardings or rules for the interzone traffic to be allowed.
1 Like
Thanks for this information, it's seems now I have what I want.
Thanks for help.
Have a good day.
1 Like
system
January 23, 2021, 2:37pm
19
This topic was automatically closed 10 days after the last reply. New replies are no longer allowed.