Hey guys,
I really love openWRT since its bringing the possibility to breath new life into my AVM Repeater.
my current setup is the following :
ISPModem -------> OPNsense------> managed Switch1---------->managed Switch2-----> Dumb AP with OpenWrt
the device is Fritzrepeater 1750E which regarding to this documentation(https://openwrt.org/toh/avm/avm_fritz_wlan_repeater_1750e) should be able to work with vlan
openwrt 23.05.0 installed
what I did was to segregate my network into 2 sections to test if everything works.
So I have my main Subnet 192.168.2.0/24 and my IOT Subnet 192.168.20.0/24
what I want to do is to use the 2.4Ghz network as IOT Wifi Channel. It already works with my Omada AP which is connected to the managed Switch1.
So I created a Vlan with the ID 20 which is tagged on the correct ports on the opnsense and the managed switches.
so now I want to setup the 1750E repeater as repeater but with the vlan 20 as the interface for my 2.4ghz channel.
cat /etc/config/firewall
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'IOT'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config forwarding
option src 'lan'
option dest 'IOT'
config forwarding
option src 'IOT'
option dest 'wan'
cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option cachesize '1000'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
option localservice '1'
option ednspacket_max '1232'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
option dhcpv4 'server'
option dhcpv6 'hybrid'
option ra 'hybrid'
list ra_flags 'managed-config'
list ra_flags 'other-config'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
cat /etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fdc9:867f:6476::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'dhcp'
config device
option type '8021q'
option ifname 'eth0'
option vid '20'
option name 'eth0.20'
config interface 'IOT'
option proto 'dhcp'
option device 'eth0.20'
option type 'bridge'
preparations to make 1750E a dumb access point:
- stopped firewall
- stopped dhcp
- stopped dnsmasq
my journey till now:
-
I create a vlan device with the correct id
-
since the 1750E has one port the vlan base device is eth0
-
after that I create an interface named IOT as dhcp client and as device I choose the vlan (eth0.20)
-
I observe that the interface is getting an ip address in the correct subnet from my opnsense(dhcp server)
-
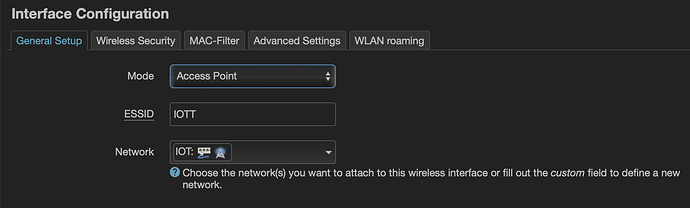
now I attach the interface to the correct wireless interface
-
sadly once I try to access the wireless channel, I can connect but wont get an ip address
.
alternatively I tried creating a bridge with just the vlan and also a bridge with eth0 and the vlan but this methods didn't even get an IP address from the dhcp server.
so now im really frustrated and I already tried looking for a solution online but I think im missing something.
im pretty new to this so already sorry in advance if some information is missing. Please let me know if there is something I can provide for an easier solution finding and thanks for the help.
cheers
derToaster1412