ubus call system board (router)
"kernel": "5.15.150",
"hostname": "Lenovo",
"system": "Intel(R) Core(TM) i5-6500T CPU @ 2.50GHz",
"model": "LENOVO 10MUS17L00",
"board_name": "lenovo-10mus17l00",
"rootfs_type": "ext4",
"release": {
"distribution": "OpenWrt",
"version": "23.05.3",
"revision": "r23809-234f1a2efa",
"target": "x86/64",
"description": "OpenWrt 23.05.3 r23809-234f1a2efa"
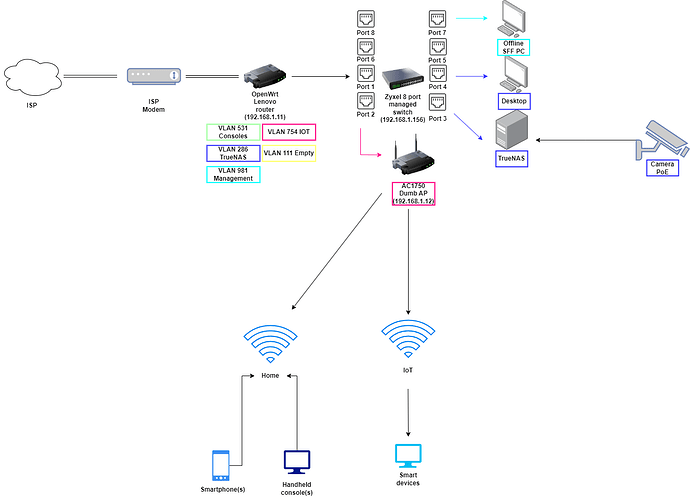
cat /etc/config/network (router)
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'x'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.11'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option device 'eth1'
option proto 'dhcp'
option peerdns '0'
list dns '1.1.1.1'
list dns '9.9.9.9'
config interface 'wan6'
option device 'eth1'
option proto 'dhcpv6'
option reqaddress 'try'
option reqprefix 'auto'
option peerdns '0'
list dns '2620:fe::fe'
list dns '2606:4700:4700::1111'
list dns '2606:4700:4700::1001'
list dns '2620:fe::9'
config interface 'IoT'
option proto 'static'
option ipaddr '192.168.3.1'
option netmask '255.255.255.0'
option device 'eth0.754'
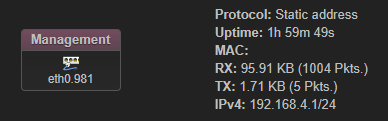
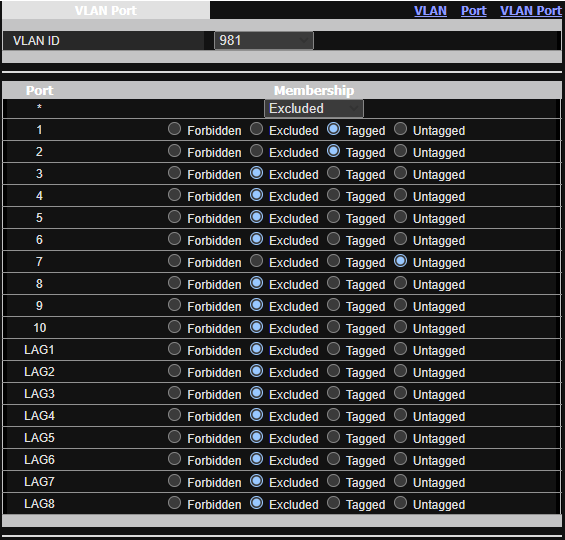
config interface 'Management'
option proto 'static'
option device 'eth0.981'
option ipaddr '192.168.4.1'
option netmask '255.255.255.0'
cat /etc/config/firewall (router)
config defaults
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
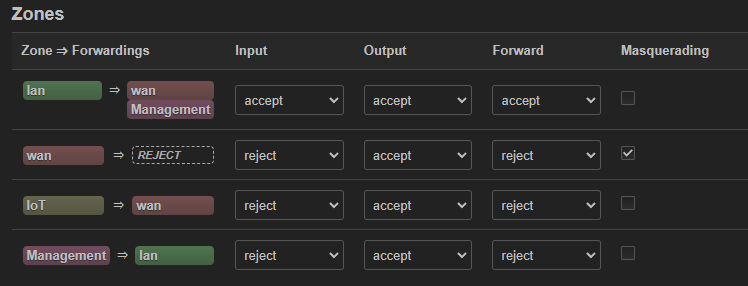
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'IoT'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'IoT'
config forwarding
option src 'IoT'
option dest 'wan'
config rule
option name 'Allow-IoT-DNS'
option src 'IoT'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Allow-IoT-DHCP'
list proto 'udp'
option src 'IoT'
option dest_port '67 68'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option name 'Intercept-DNS'
option family 'any'
option src 'lan'
option src_dport '53'
option enabled '0'
config redirect
option target 'DNAT'
option name 'Intercept-DNS-IoT'
option family 'any'
option src 'IoT'
option src_dport '53'
option dest 'lan'
option dest_port '53'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'Divert-DNS, port 53'
option src 'lan'
option src_dport '53'
option dest_port '53'
config zone
option name 'Management'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
list network 'Management'
config forwarding
option src 'Management'
option dest 'lan'
config forwarding
option src 'lan'
option dest 'Management'
config rule
option name 'Admin-VLAN-DNS'
option src 'Management'
option dest_port '53'
option target 'ACCEPT'
config rule
option name 'Admin-VLAN-Access'
option src 'lan'
list src_ip '192.168.1.218'
option dest 'Management'
option target 'ACCEPT'
list proto 'all'
ubus call system board (AP)
"kernel": "5.15.137",
"hostname": "AC1750v5",
"system": "Qualcomm Atheros QCA956X ver 1 rev 0",
"model": "TP-Link Archer C7 v5",
"board_name": "tplink,archer-c7-v5",
"rootfs_type": "squashfs",
"release": {
"distribution": "OpenWrt",
"version": "23.05.2",
"revision": "r23630-842932a63d",
"target": "ath79/generic",
"description": "OpenWrt 23.05.2 r23630-842932a63d"
network (AP)
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'x'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.12'
option netmask '255.255.255.0'
option ip6assign '60'
option gateway '192.168.1.11'
list dns '192.168.1.11'
config device
option name 'eth0.2'
option macaddr 'xx:xx:xx:xx:xx:xx'
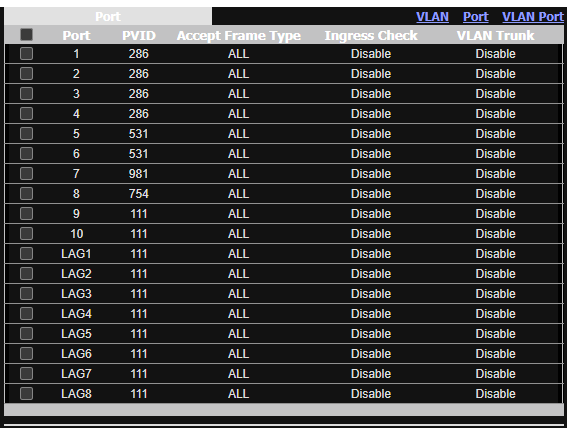
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '2 3 4 5 0t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '1 0t'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '754'
option ports '4t 0t'
config device
option type 'bridge'
option name 'br-iot'
list ports 'eth0.754'
config interface 'IoT'
option proto 'none'
option device 'br-iot'
firewall (AP)
config defaults
option syn_flood '1'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'