I've setup a wifi bridge using this guide https://www.nerd-quickies.net/2019/08/20/setup-lan-wlan-bridge-with-openwrt-luci/ and it works as expected however if i want to do a port forward i have to forward it form my main non openwrt router to the ip of the openwrt relayd router and then add a port forward on that to a device behind it.
How do i configure it so I only need to do it on my main router only?
What is the device and how is it connected to the relayd router?
Any ethernet device connecting to the relayd router should be using IP address in same subnet as your main router, so there shouldn't be any need to configure any port forward rule on the relayd router.
ie. on your main non-openwrt router, you should be able to configure port forward direct to the device connected to relayd router.
Update 17 Aug 2022. LuCI setup procedure has been refreshed for OpenWrt 21.02. bye bye LEDE17 images !
https://openwrt.org/docs/guide-user/network/wifi/relay_configuration
It's a linux box via ethernet to the relayd router.
It is using an ip on the same subnet as my main router however port forwards fail to work unless i add it twice but as you say i shouldn't have to.
What is the owrt device and version of OpenWrt installed?
The 3rd party link you provided seems to describe creating a new firewall zone, rather than editing existing LAN zone. Article makes no mention of 'cleaning up' unwanted interfaces and zones.
fwiw, the original owrt wiki on subject leaves a lot to be desired. There is a link to a detailed relayd setup guide for HH5a. I know the instructions are valid for 21.02.3, allowing for differences in LuCI.
https://openwrt.org/docs/guide-user/network/wifi/relay_configuration#known_issues
It's a pcenignes apu running OpenWrt 21.02.2 r16495-bf0c965af0 / LuCI openwrt-21.02 branch git-22.046.85957-59c3392
Currently it all works as expected with good performance it's just the forwarding issue so I would like to avoid a complete reinstall if possible.
Post the contents of /etc/network and /etc/firewall. Someone may be able to help. Use the </> format tool.
Also post the LAN IP address of main router and WWAN IP of relayd router.
/etc/config/network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd4e:20df:43ad::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth1'
list ports 'eth2'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '192.168.15.1'
option delegate '0'
config interface 'wan'
option device 'eth0'
option proto 'dhcp'
config interface 'wan6'
option device 'eth0'
option proto 'dhcpv6'
config interface 'wwan'
option proto 'dhcp'
config interface 'stabridge'
option proto 'relay'
list network 'lan'
list network 'wwan'
/etc/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
option input 'ACCEPT'
option forward 'ACCEPT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config rule
option name 'Allow-SSH-WAN'
option proto 'tcp'
option dest_port '22'
option target 'ACCEPT'
option src 'wan'
config rule
option name 'Allow-HTTP-WAN'
option proto 'tcp'
option dest_port '80'
option target 'ACCEPT'
option src 'wan'
config include
option path '/etc/firewall.user'
config zone
option name 'bridgezone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
list network 'lan'
list network 'wwan'
config forwarding
option src 'bridgezone'
option dest 'wan'
MAIN 192.168.1.100/24
WWANIP relayd IPv4: 192.168.1.190/24
What port forward rule did you add for your linux box, because it doesn't appear to be visible in the firewall file?
both files seem to look OK except for:
config forwarding
option src 'bridgezone'
option dest 'wan'
but wan interface is not being utilised, so the rule should do nothing in theory?
I suggest back up your settings, then delete both the wan and wan6 interfaces?
I ommited them as there is quite a lot but an example one is
config redirect
option dest 'lan'
option target 'DNAT'
option src 'wan'
option dest_ip '192.168.1.10'
option dest_port '22'
option name 'SSH'
option src_dport '22'
i'll try deleteing thos interfaces later when i'm at home.
fwiw, I've just been fiddling with relayd on 21.02.3.
Here is entire contents of my /etc/firewall file.
I did not manually remove any other rules, so I guess when I deleted the wan, wan6 interfaces and wan zones, openwrt perhaps removed the redundant rules too, leaving the following:
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wwan'
config include
option path '/etc/firewall.user'
Running older 21.02.2 shouldn't make a difference.....
Try removing this rule before deleting any interfaces or zones.
config forwarding
option src 'bridgezone'
option dest 'wan'
I deleted
config forwarding
option src 'bridgezone'
option dest 'wan'
and my existing port forward still worked so assume that rule wasn't doing anything.
What port number does your linux box use?
Do you have issues with port forwarding for 'other' devices connected to the relayd router?
I use a wide range of ports including typical ones 80,22,23 etc, all devices behind the relayd box have the same issue.
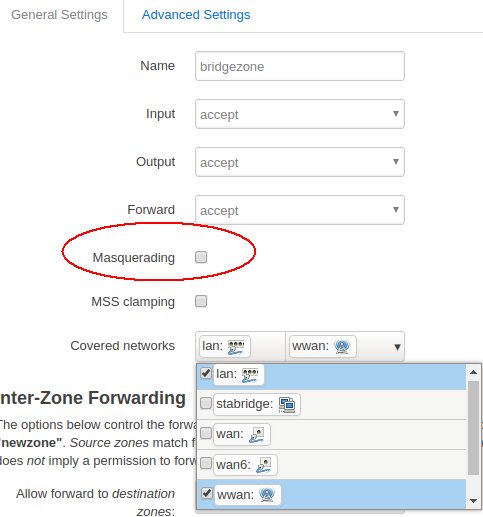
I just spotted a mistake in your firewall config file
config zone
option name 'bridgezone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option masq '1' # Delete this line !
list network 'lan'
list network 'wwan'
Image below is from 3rd party link in OP
Oh good spot! I will re add that zone and retry.
I deleted that zone earlier and it didn't make any difference to how the setup was working. I re-added without masq ticked deleted the port forward on the relayd device and edited it on my non openwrt router from the ip of relayd to the ip of the linux box and it no longer works.
Please repost your /etc/config/firewall.
Did you reboot the relayd router after making the changes?
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'wwan'
option input 'ACCEPT'
option forward 'ACCEPT'
option masq '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option name 'Support-UDP-Traceroute'
option src 'wan'
option dest_port '33434:33689'
option proto 'udp'
option family 'ipv4'
option target 'REJECT'
option enabled '0'
config rule
option name 'Allow-SSH-WAN'
option proto 'tcp'
option dest_port '22'
option target 'ACCEPT'
option src 'wan'
config rule
option name 'Allow-HTTP-WAN'
option proto 'tcp'
option dest_port '80'
option target 'ACCEPT'
option src 'wan'
config include
option path '/etc/firewall.user'
config zone
option name 'bridgezone'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
list network 'wwan'
yes i did reboot
I'm out of suggestions.
Deleting the wan interface and firewall zones was an earlier suggestion.
Perhaps there is a 'bug' with 21.02.2 and/or for the pcengines apu ?
I don't suppose you own any other spare openwrt compatible router, to test relayd ?
I just deleted all my port forwards on the relayd to start afresh
If on my main router I do an ssh port forward to the linux box sitting behind the relayd 192.168.1.10 when i ssh to 192.168.1.10 from my lan it actually ssh's to the relayd box and not the linux box so it appears if traffic isn't being forwarded correctly.