I have a setup similar to what you are trying to achieve. I'd recommend you start over with your Pi and switch and even your modem.
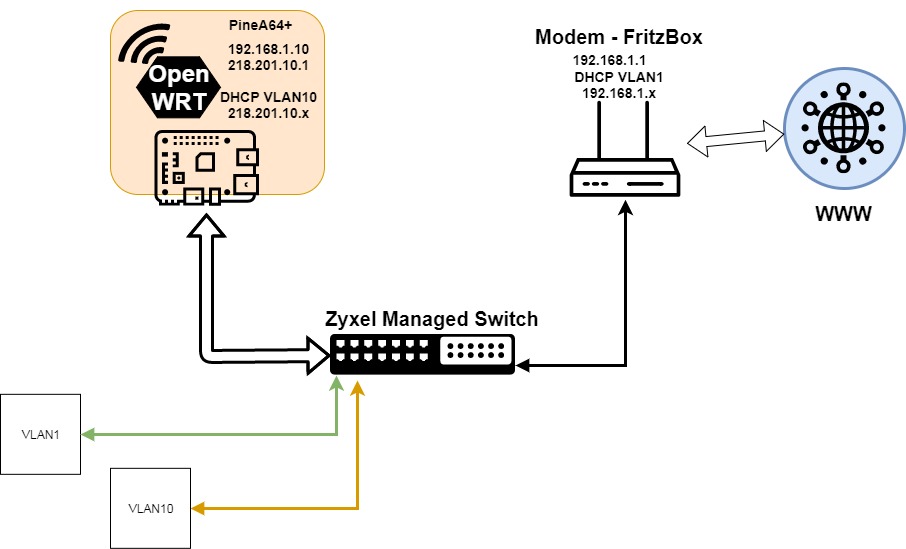
A quick side note: Why are you using 218.201.10.0/24 -- this is not an RFC1918 range. While possible to use, it may cause headaches in the future. Stick with RFC1918 address ranges (192.168.xxx.xxx, 10.xxx.xxx.xxx, 172.16.xxx.xxx)
First thing: can you modem be set to a true bridge mode such that a device connected to it gets a public IP (instead of being behind the router functions that will make the connection NAT'd and firewalled? If this is an option, you'll want to use it. If not, you'll be double-NAT'd, which is not usually a big deal, but can be less than ideal and can sometimes cause issues.
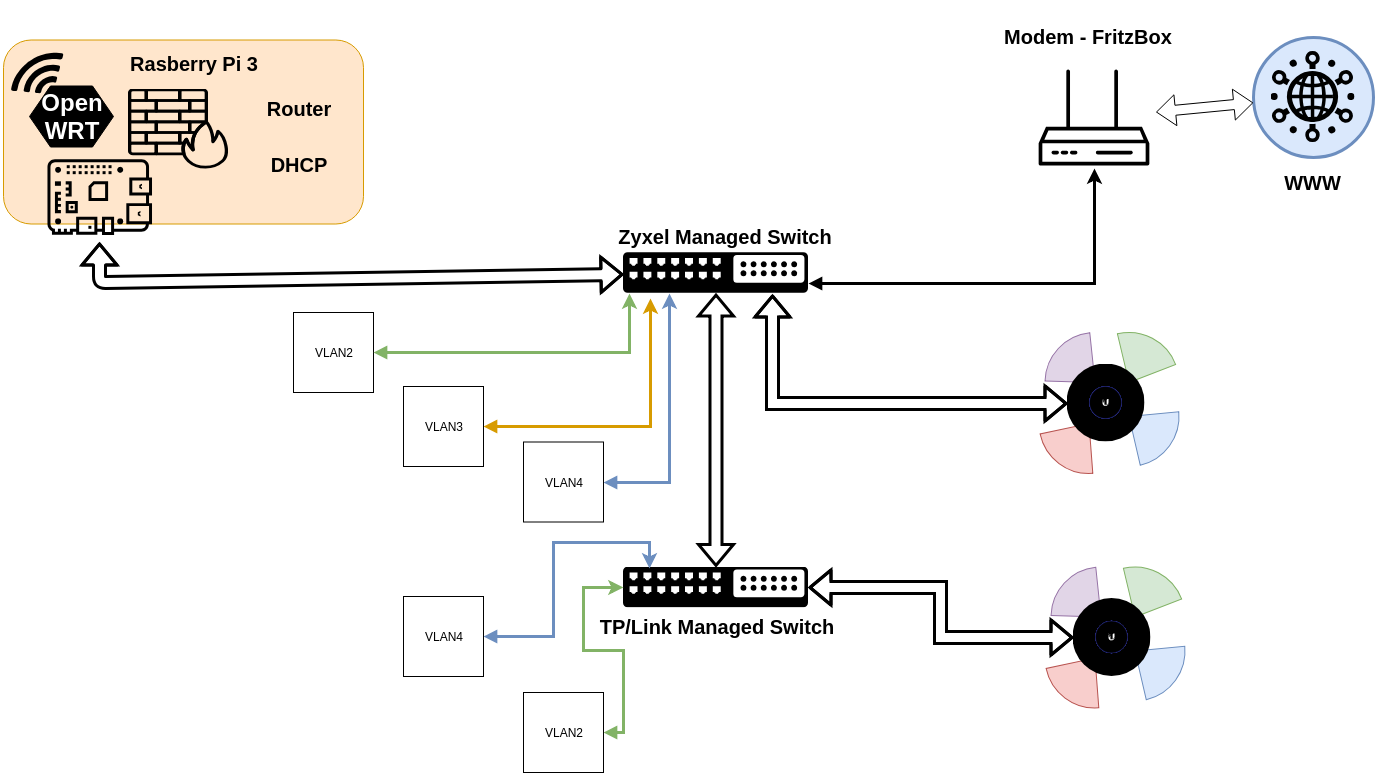
Next, define your VLANs. For the moment, I'm going to use LAN = 10, Guest = 20, and WAN = 100. And define your physical switchports for the connections (I'll assume Fritzbox = port 1, Pi = port 2)
On the managed switch, set the physical switchport (1) for the Fritzbox to have a PVID (default untagged) VLAN ID = 100. Similarly on the switchport that will connect to your Pi's ethernet port (2), set that to be a member of VLAN 100 (preference will dictate if this is tagged or untagged). Make sure that VLAN 100 is not assigned to any other switchports.
Also on the managed switch, set port 2 (pi) to use VLAN 10 and VLAN 20 (you've now got VLAN 10, 20, and 100 on that physical port -- at least 2 of those must be tagged, you can select which, if any, is untagged on that port.
Set all other ports on your switch to use VLAN10 and/or VLAN20 (often it is easiest to simply make them untagged on those ports, unless you are using a trunk port or will be connecting VLAN aware devices to those ports).
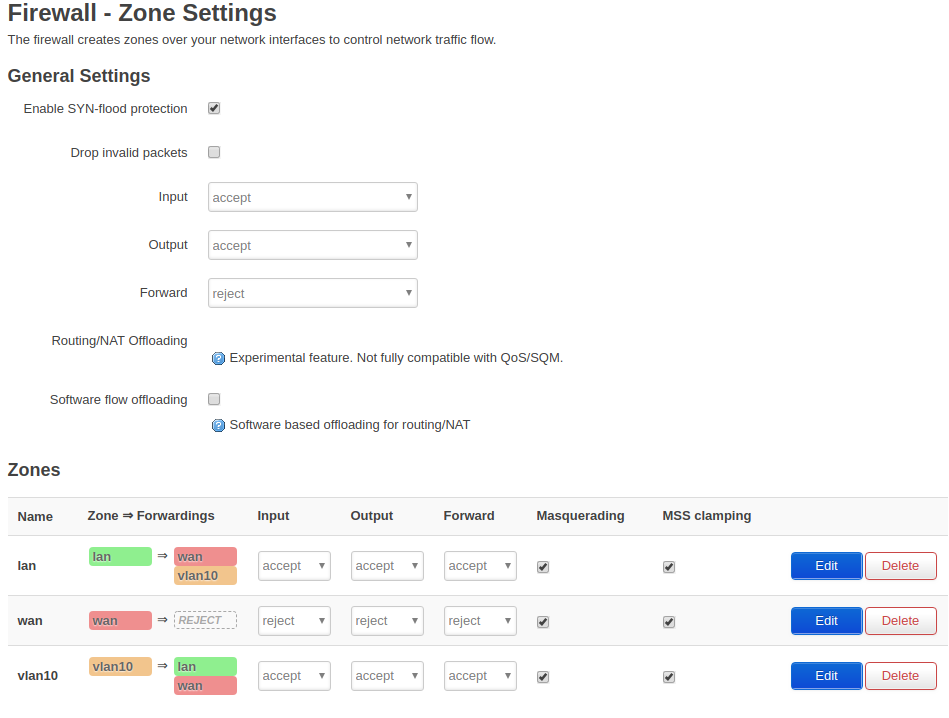
Now, on the Pi, set the VLANs on your ethernet port to be the same as those on the switch port 2. For example, if you tagged all 3 networks, then eth0.100 is your WAN interface (and should be associated with the WAN firewall zone) most likely with DHCP or PPPoE as the protocol. Your LAN will be eth0.10 (lan firewall zone), and eth0.20 is your guest (guest firewall zone -- you will still need to setup that zone). If you have chosen to have one of those networks untagged on port 2 of your switch, then it would be associated with eth0 directly (notice not eth0.xxx).
At this point, the switch will simply pass through the WAN/internet connection from port 1 to port 2 (and to no other ports participate on this), and then the other ports will get their LAN and/or Guest networks from the OpenWRT pi.
EDIT: don't forget that all networks need to exist on separate subnets as well as different VLAN IDs. So if your WAN comes through as a public IP, awesome. If not, make sure your LAN and Guest networks are not the same subnet as the fritzbox. Your fritzbox seems to be 192.168.1.1 and controlling a network 192.168.1.0/24. So you might want your LAN to be 10.0.10.0/24 and your Guest to be 10.0.20.0/24. Or really anything you want other than 192.168.1.0/24.
The port numbers, VLAN IDs, and IP subnets are just examples -- feel free to modify, but pay attention to the details around different subnets and the use of the VLANs and such.