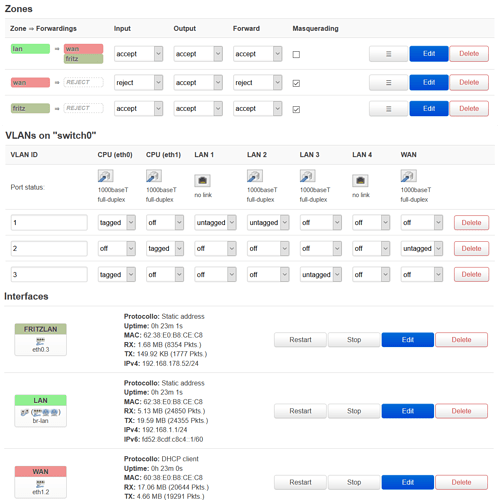
tcpdump: listening on eth0.3, link-type EN10MB (Ethernet), capture size 262144 bytes
15:29:02.630563 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40269, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63484 > 192.168.178.1.80: Flags [S], cksum 0x661f (correct), seq 491790971, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:02.893106 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40270, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63485 > 192.168.178.1.80: Flags [S], cksum 0x1d6d (correct), seq 1541221535, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:02.976859 70:26:05:f8:93:18 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.54, length 46
15:29:03.640847 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40271, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63484 > 192.168.178.1.80: Flags [S], cksum 0x661f (correct), seq 491790971, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:03.894752 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40272, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63485 > 192.168.178.1.80: Flags [S], cksum 0x1d6d (correct), seq 1541221535, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:05.645197 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40273, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63484 > 192.168.178.1.80: Flags [S], cksum 0x661f (correct), seq 491790971, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:07.028409 5c:49:79:23:8c:52 > 62:38:e0:b8:ce:c8, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.1.80 > 192.168.178.52.63485: Flags [S.], cksum 0x3b62 (correct), seq 270374965, ack 1541221536, win 14600, options [mss 1460,nop,nop,sackOK], length 0
15:29:07.029072 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 40275, offset 0, flags [DF], proto TCP (6), length 40)
192.168.178.52.63485 > 192.168.178.1.80: Flags [.], cksum 0xa16d (correct), ack 1, win 65472, length 0
15:29:07.030223 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 409: (tos 0x0, ttl 127, id 40276, offset 0, flags [DF], proto TCP (6), length 395)
192.168.178.52.63485 > 192.168.178.1.80: Flags [P.], cksum 0x6611 (correct), seq 1:356, ack 1, win 65472, length 355: HTTP, length: 355
GET / HTTP/1.1
Host: 192.168.178.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
15:29:07.698203 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:08.738202 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:09.653669 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40277, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63484 > 192.168.178.1.80: Flags [S], cksum 0x661f (correct), seq 491790971, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:09.778202 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:10.038916 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 409: (tos 0x0, ttl 127, id 40278, offset 0, flags [DF], proto TCP (6), length 395)
192.168.178.52.63485 > 192.168.178.1.80: Flags [P.], cksum 0x6611 (correct), seq 1:356, ack 1, win 65472, length 355: HTTP, length: 355
GET / HTTP/1.1
Host: 192.168.178.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
15:29:11.892750 5c:49:79:23:8c:52 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 102: (tos 0x0, ttl 1, id 41889, offset 0, flags [none], proto UDP (17), length 88)
192.168.178.1.5353 > 224.0.0.251.5353: 59769+ ANY (QM)? fb7692a4-34d4-581d-b52d-b4f4f95fdf31.local. (60)
15:29:13.092240 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:14.098205 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:15.138203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:17.038412 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:18.098203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:19.138203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:20.330044 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:21.378203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:22.428203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:23.669202 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:24.748202 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:25.788203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:27.345434 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:28.418203 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:29.468202 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:30.690064 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:31.698206 62:38:e0:b8:ce:c8 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:32.243162 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:32.243180 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40300, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63490 > 192.168.178.1.80: Flags [S], cksum 0x6984 (correct), seq 1648286241, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:32.243185 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 409: (tos 0x0, ttl 127, id 40301, offset 0, flags [none], proto TCP (6), length 395)
192.168.178.52.63485 > 192.168.178.1.80: Flags [FP.], cksum 0x6610 (correct), seq 1:356, ack 1, win 65472, length 355: HTTP, length: 355
GET / HTTP/1.1
Host: 192.168.178.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
15:29:33.061725 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 55: (tos 0x0, ttl 127, id 40302, offset 0, flags [none], proto TCP (6), length 41)
192.168.178.52.63485 > 192.168.178.1.80: Flags [.], cksum 0xa16d (correct), seq 0:1, ack 1, win 65472, length 1: HTTP
15:29:33.242719 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:34.107166 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40303, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63487 > 192.168.178.1.80: Flags [S], cksum 0x5165 (correct), seq 202000504, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:34.242579 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:35.265244 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:36.262321 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:37.262177 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:37.298203 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:38.300232 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:38.338203 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:38.695689 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40305, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63490 > 192.168.178.1.80: Flags [S], cksum 0x6984 (correct), seq 1648286241, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:39.292080 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:39.378202 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:29:40.133173 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40306, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63495 > 192.168.178.1.80: Flags [S], cksum 0x728e (correct), seq 3020783427, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:40.292082 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:41.360071 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:42.352094 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:43.117952 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 409: (tos 0x0, ttl 127, id 40309, offset 0, flags [none], proto TCP (6), length 395)
192.168.178.52.63485 > 192.168.178.1.80: Flags [FP.], cksum 0x6610 (correct), seq 1:356, ack 1, win 65472, length 355: HTTP, length: 355
GET / HTTP/1.1
Host: 192.168.178.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: keep-alive
Upgrade-Insecure-Requests: 1
15:29:43.158141 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40310, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63495 > 192.168.178.1.80: Flags [S], cksum 0x728e (correct), seq 3020783427, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:29:43.352096 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:44.409718 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:45.098076 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 55: (tos 0x0, ttl 127, id 40311, offset 0, flags [none], proto TCP (6), length 41)
192.168.178.52.63485 > 192.168.178.1.80: Flags [.], cksum 0xa16d (correct), seq 0:1, ack 1, win 65472, length 1: HTTP
15:29:45.402116 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:46.179288 5c:49:79:23:8c:52 > 01:00:5e:00:00:01, ethertype IPv4 (0x0800), length 60: (tos 0xc0, ttl 1, id 5103, offset 0, flags [DF], proto IGMP (2), length 36, options (RA))
192.168.178.1 > 224.0.0.1: igmp query v3
15:29:46.402174 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
^C
60 packets captured
60 packets received by filter
0 packets dropped by kernel
root@OpenWrt:~# ^C
root@OpenWrt:~# tcpdump -i eth0.3 -evn host 192.168.178.1
tcpdump: listening on eth0.3, link-type EN10MB (Ethernet), capture size 262144 bytes
15:29:58.552965 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:29:59.589937 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:00.583124 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:01.583196 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:02.618847 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:03.613320 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:04.613393 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:05.641572 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:06.633530 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:07.223527 5c:49:79:23:8c:52 > 62:38:e0:b8:ce:c8, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.1.80 > 192.168.178.52.63490: Flags [S.], cksum 0x3af8 (correct), seq 1387242020, ack 1648286242, win 14600, options [mss 1460,nop,nop,sackOK], length 0
15:30:07.633610 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:08.668769 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:09.212420 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40321, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63510 > 192.168.178.1.80: Flags [S], cksum 0x9b7e (correct), seq 1299430622, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:09.475260 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40322, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63511 > 192.168.178.1.80: Flags [S], cksum 0xaaf0 (correct), seq 2788709542, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:09.663761 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:10.228108 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40323, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63510 > 192.168.178.1.80: Flags [S], cksum 0x9b7e (correct), seq 1299430622, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:10.475593 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40324, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63511 > 192.168.178.1.80: Flags [S], cksum 0xaaf0 (correct), seq 2788709542, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:10.663839 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:11.701940 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:11.889717 5c:49:79:23:8c:52 > 01:00:5e:00:00:fb, ethertype IPv4 (0x0800), length 102: (tos 0x0, ttl 1, id 45200, offset 0, flags [none], proto UDP (17), length 88)
192.168.178.1.5353 > 224.0.0.251.5353: 63586+ ANY (QM)? fb7692a4-34d4-581d-b52d-b4f4f95fdf31.local. (60)
15:30:12.480600 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40326, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63511 > 192.168.178.1.80: Flags [S], cksum 0xaaf0 (correct), seq 2788709542, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:12.693896 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:13.693902 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:14.487419 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40327, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63515 > 192.168.178.1.80: Flags [S], cksum 0x7c66 (correct), seq 4118819812, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:14.732293 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:15.488328 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40328, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63515 > 192.168.178.1.80: Flags [S], cksum 0x7c66 (correct), seq 4118819812, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:15.723938 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:16.258923 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40329, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63510 > 192.168.178.1.80: Flags [S], cksum 0x9b7e (correct), seq 1299430622, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:16.723959 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:17.492971 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype IPv4 (0x0800), length 62: (tos 0x0, ttl 127, id 40330, offset 0, flags [DF], proto TCP (6), length 48)
192.168.178.52.63515 > 192.168.178.1.80: Flags [S], cksum 0x7c66 (correct), seq 4118819812, win 65472, options [mss 1364,nop,nop,sackOK], length 0
15:30:17.746011 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:18.744004 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:19.538202 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:30:19.744027 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:20.588202 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:30:20.782377 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
15:30:21.628204 62:38:e0:b8:ce:c8 > 5c:49:79:23:8c:52, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.1 tell 192.168.178.52, length 28
15:30:21.774094 5c:49:79:23:8c:52 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 192.168.178.34 tell 192.168.178.1, length 46
^C
38 packets captured
38 packets received by filter
0 packets dropped by kernel