Hello,
even though the problem I describe below probably does not concern OpenWRT, I still ask for your help. Maybe someone has an idea what the problem is.
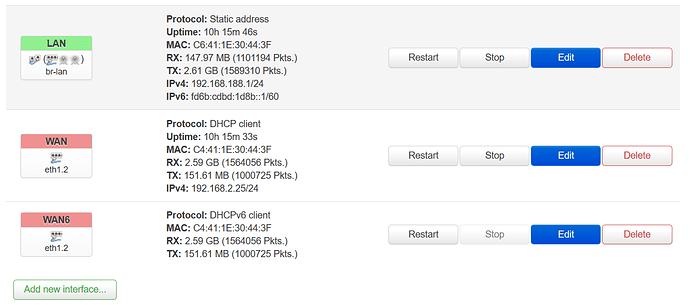
I use three routers in my home network. These are a Draytek Vigor 165, Linksys WRT1900ACS and AVM Fritzbox 7590. The Vigor, Linksys as well as the Fritzbox are connected in this order via WAN port and have their own IP address range. The latter, the Fritzbox, is used exclusively for DECT telephony. The Vigor establishes the Internet connection via PPPoE and then forwards it to the Linksys/Fritzbox.
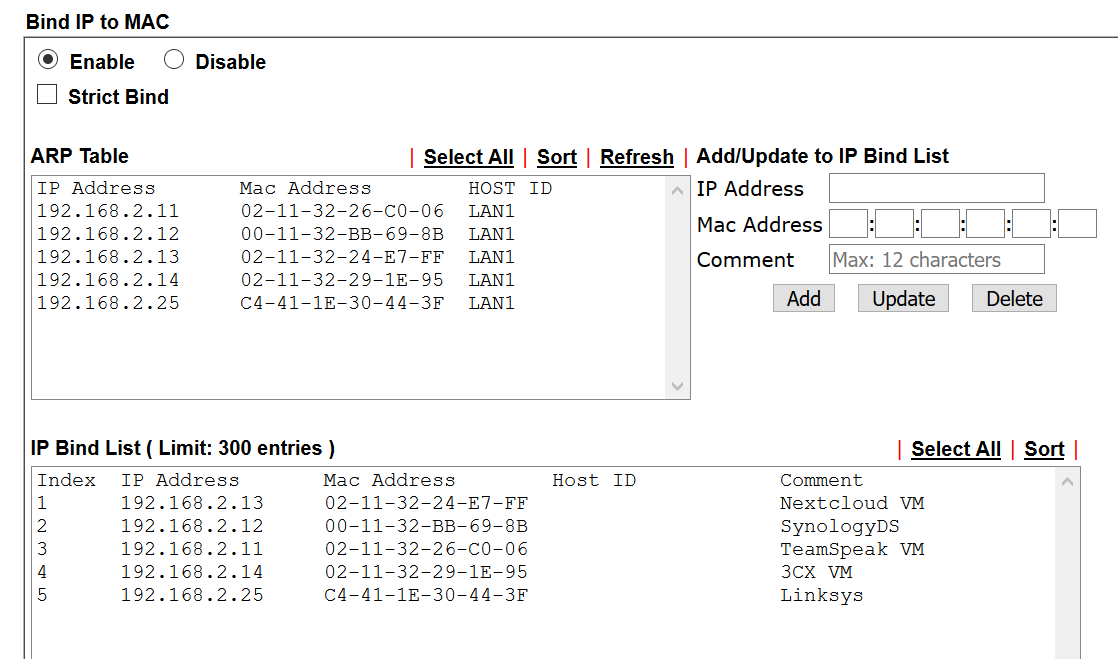
The clients of the home network are managed by the Linksys router, with a Synology NAS running various Docker and VM instances connected to the Vigor and Linksys via two LAN ports. Applications on the Synology NAS that do not need to be on the home network are thus in the IP address range of Vigor.
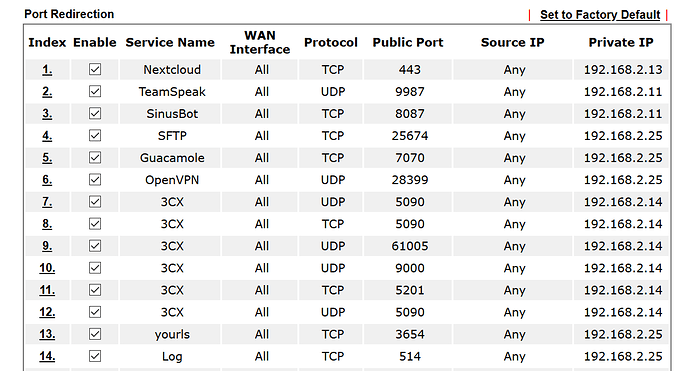
Unfortunately, the port forwarding between Vigor and Linksys works only sporadically, for reasons I can't explain. And if it works, then apparently only until one of the routers is rebooting. Devices and ports that only affect Vigor and are not forwarded to Linksys, however, always work properly.
It can be excluded that it is due to the Linksys router. The same error has also occurred if the Fritzbox accepts the client administration in the home network or the port forwarding of the Vigor.
On both devices the latest firmware is installed (Vigor 4.0.5, Linksys OpenWRT 19.07). A look into the log of the Vigor also shows that the ports are forwarded correctly.
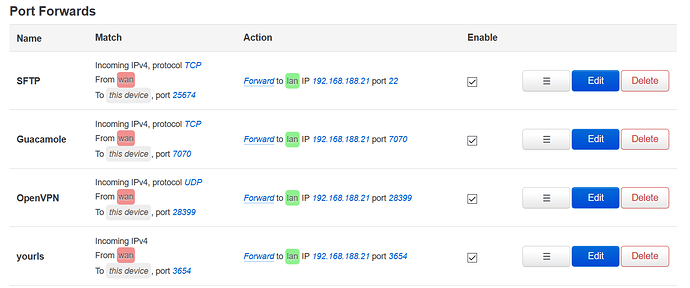
I would be very happy about your help. The ports are released exemplarily as follows:
root@OpenWrt:~# iptables-save -c | grep DNAT
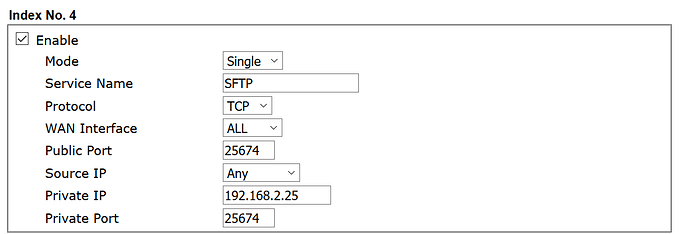
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p tcp -m tc p --dport 25674 -m comment --comment "!fw3: SFTP (reflection)" -j DNAT --to-dest ination 192.168.188.21:22
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p tcp -m tc p --dport 7070 -m comment --comment "!fw3: Guacamole (reflection)" -j DNAT --to- destination 192.168.188.21:7070
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p udp -m ud p --dport 28399 -m comment --comment "!fw3: OpenVPN (reflection)" -j DNAT --to-d estination 192.168.188.21:28399
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p tcp -m tc p --dport 3654 -m comment --comment "!fw3: yourls (reflection)" -j DNAT --to-des tination 192.168.188.21:3654
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p udp -m ud p --dport 3654 -m comment --comment "!fw3: yourls (reflection)" -j DNAT --to-des tination 192.168.188.21:3654
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p tcp -m tc p --dport 514 -m comment --comment "!fw3: Log (reflection)" -j DNAT --to-destina tion 192.168.188.242:514
[0:0] -A zone_lan_prerouting -s 192.168.188.0/24 -d 192.168.2.25/32 -p udp -m ud p --dport 514 -m comment --comment "!fw3: Log (reflection)" -j DNAT --to-destina tion 192.168.188.242:514
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 25674 -m comment --comment "! fw3: SFTP" -j DNAT --to-destination 192.168.188.21:22
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 7070 -m comment --comment "!f w3: Guacamole" -j DNAT --to-destination 192.168.188.21:7070
[56:2352] -A zone_wan_prerouting -p udp -m udp --dport 28399 -m comment --commen t "!fw3: OpenVPN" -j DNAT --to-destination 192.168.188.21:28399
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 3654 -m comment --comment "!f w3: yourls" -j DNAT --to-destination 192.168.188.21:3654
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 3654 -m comment --comment "!f w3: yourls" -j DNAT --to-destination 192.168.188.21:3654
[0:0] -A zone_wan_prerouting -p tcp -m tcp --dport 514 -m comment --comment "!fw 3: Log" -j DNAT --to-destination 192.168.188.242:514
[0:0] -A zone_wan_prerouting -p udp -m udp --dport 514 -m comment --comment "!fw 3: Log" -j DNAT --to-destination 192.168.188.242:514
[0:0] -A zone_lan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3 : Accept port forwards" -j ACCEPT
[0:0] -A zone_lan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
[332:13944] -A zone_wan_forward -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port forwards" -j ACCEPT
[0:0] -A zone_wan_input -m conntrack --ctstate DNAT -m comment --comment "!fw3: Accept port redirections" -j ACCEPT
I would be very happy about your help.
PD