as i know
the auther lede has make a bin file for zyxel G5,the led progress is done(i have get it,i mean the the pakg)
https://github.com/coolsnowwolf
an bilibili uper has Installing OpenWrt into G5
i follow the step
[[OpenWrt Wiki] ZyXEL NBG7815 (Armor G5)](https://openwrt.org/inbox/toh/zyxel/nbg7815_armor_g5)
to Installing OpenWrt
but the second step(a) Use WinSCP client(if you have ssh access) for putting your openwrt-ipq807x-generic-zyxel_nbg7815-squashfs-sysupgrade.bin in /tmp/ApplicationData) does not success
because G5 does not have sch protocol
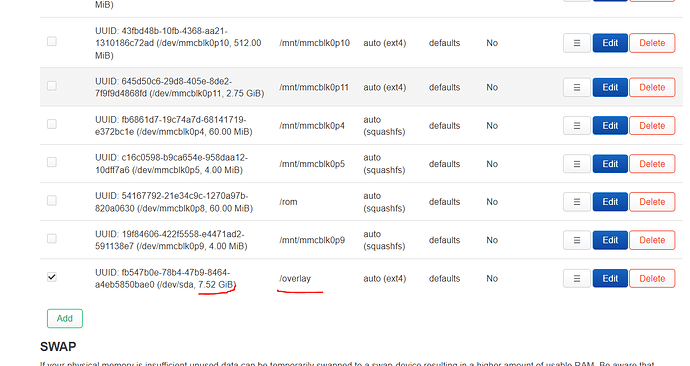
I wanted to increase the storage space of the device, and set it to overlay. But what I did didn't work. I tried with two different usb sticks. The available storage space is not increasing. I tried again as described in the link below and it still doesn't work.
There is no such problem with the old Zyxel NBG6716 device. I can increase the storage space by doing the same process. Does anyone have information? How can I increase the Armor G5's storage for add-ons?
@robimarko @avalentin
I don't know if the problem that I am going to expose only affects NBG7815 or all ath11k devices, but since commit 930e702d72 (mac80211: ath11k: sync with ath-next) there is a bug that does not allow intel ax210 clients connects to router . I have tested on win11, win 10 and ubuntu 22.10
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 7EDE0A8C3AF6E1E5
Fri Apr 14 09:23:53 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:23:53 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:23:53 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:00 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:00 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:00 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 0E4484F80FC910EF
Fri Apr 14 09:24:00 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:00 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:00 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:05 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:05 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:05 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 5C0E3AFCEBC83EE8
Fri Apr 14 09:24:05 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:08 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:08 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:08 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 67D40D35401ABC14
Fri Apr 14 09:24:08 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:08 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:08 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:13 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:13 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:13 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 55961ADAFA71604A
Fri Apr 14 09:24:13 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:13 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:13 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:18 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:18 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:18 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 763498C37335392E
Fri Apr 14 09:24:18 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:20 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:20 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:25 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:25 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:25 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 39582E6950E4ED8E
Fri Apr 14 09:24:25 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:25 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:25 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:28 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:28 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:28 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session E973E5F1C93102B8
Fri Apr 14 09:24:28 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:28 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:28 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:32 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:32 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:32 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session C66006828B118741
Fri Apr 14 09:24:32 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:34 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:34 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: authenticated
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX IEEE 802.11: associated (aid 1)
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX RADIUS: starting accounting session 0D55F1FD04C7CA9A
Fri Apr 14 09:24:39 2023 daemon.info hostapd: phy2-ap0: STA 84:5c:f3:XX:XX:XX WPA: pairwise key handshake completed (RSN)
Fri Apr 14 09:24:39 2023 daemon.info dnsmasq-dhcp[1]: DHCPREQUEST(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX
Fri Apr 14 09:24:39 2023 daemon.info dnsmasq-dhcp[1]: DHCPACK(br-lan) 192.168.1.220 84:5c:f3:XX:XX:XX DESKTOP-XXXXXX
wirelles 5ghz config
config wifi-device 'radio0'
option type 'mac80211'
option path 'platform/soc/c000000.wifi'
option band '5g'
option htmode 'HE80'
option cell_density '0'
option country 'ES'
option channel '100'
config wifi-iface 'default_radio0'
option device 'radio0'
option mode 'ap'
option ssid 'xxxxxxxxxxxxxxx'
option encryption 'psk2+ccmp'
option key 'xxxxxxxxxxxxxxxxxxxxx'
option ieee80211r '1'
option mobility_domain 'xxxx'
option reassociation_deadline '20000'
option ft_over_ds '0'
option ft_psk_generate_local '1'
option time_advertisement '2'
option time_zone 'CET-1CEST,M3.5.0,M10.5.0/3'
option wnm_sleep_mode '1'
option bss_transition '1'
option network 'home'
option ieee80211k '1'
EDIT: MediaTek MT7921 works without problem
At least an AX201 is still working here.
What does the client log say, for example on Ubuntu?
journalctl -xe -u wpa_supplicant (or iwd)
In your log there are DHCPREQUESTS and DHCPACK, means there is TCP/IP traffic.
I need time to be able to check it. Today I need the connection active for these clients ax210
Clients connets but drop connection. it makes useless even for connection to LUCI
asvio@MSI-GS72-6QE:~$ journalctl -xe -u wpa_supplicant
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:07:55 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-29 noise=9999 txrate=245000
abr 15 19:07:57 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
abr 15 19:07:57 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-DISCONNECTED bssid=00:03:7f:xx:xx:xx reason=4 locally_generated=1
abr 15 19:07:59 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:08:07 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-29 noise=9999 txrate=245000
abr 15 19:08:08 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
abr 15 19:08:09 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-DISCONNECTED bssid=00:03:7f:xx:xx:xx reason=4 locally_generated=1
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:08:16 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-29 noise=9999 txrate=245000
abr 15 19:08:18 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-DISCONNECTED bssid=00:03:7f:xx:xx:xx reason=4 locally_generated=1
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:08:25 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-30 noise=9999 txrate=245000
abr 15 19:08:29 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-DISCONNECTED bssid=00:03:7f:xx:xx:xx reason=4 locally_generated=1
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:08:36 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:08:37 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-29 noise=9999 txrate=245000
abr 15 19:08:38 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
abr 15 19:08:38 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
abr 15 19:08:39 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-DISCONNECTED bssid=00:03:7f:xx:xx:xx reason=4 locally_generated=1
abr 15 19:08:40 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: SME: Trying to authenticate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Trying to associate with 00:03:7f:xx:xx:xx (SSID='xxxxxxxx' freq=5500 MHz)
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: Associated with 00:03:7f:xx:xx:xx
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SUBNET-STATUS-UPDATE status=0
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: WPA: Key negotiation completed with 00:03:7f:xx:xx:xx [PTK=CCMP GTK=CCMP]
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-CONNECTED - Connection to 00:03:7f:xx:xx:xx completed [id=0 id_str=]
abr 15 19:08:48 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-SIGNAL-CHANGE above=1 signal=-30 noise=9999 txrate=245000
abr 15 19:08:58 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
abr 15 19:08:58 MSI-GS72-6QE wpa_supplicant[809]: wlp2s0: CTRL-EVENT-BEACON-LOSS
Well, I'm also seening those CTRL-EVENT-BEACON-LOSS
messages from time to time and a following disconnect, but there is a working re-connect afterwards.
What iwlwifi firmware version are you using?
I'm using QuZ-a0-hr-b0-72.ucode
Honestly no idea, I have AX200 and that works just fine.
Best thing would be to remove the newly added patches one by one and test, no other way around it if that commit is to blame as nothing is really IPQ8074 related
16/4/23 9:27 iwlwifi 0000 2:00.0: loaded firmware version 72.daa05125.0 ty-a0-gf-a0-72.ucode op_mode iwlmvm
This is what i find on kernel log
I had also problems with connecting certain ax clients. I wasn't able to figure out what the isue is. So I helped myself in relaying all dhcp requests to an external dhcp server. Now everything works fine.
I have been doing some tests.
The tests have been done by adding LUCI and wpad-openssl to the default configuration of the NBG7815.
Problems with ax210 clients start with commit 930e702d72 and still is present on last commit, and only occur after firmware installation. If the router is rebooted after the inicial sysupgrade's reboot the problem disappears.
As a result of the tests carried out, I have found other problems that I list below:
Every time the router is rebooted or sysupgraded, it changes the Wi-Fi radios's MACs in the range of 00:03:7f:12:xx:xx. It is true that the MACs can be set through the device-interface or wireless config but it is somewhat unexpected (at least for me) and can cause problems with some clients that when connecting do not just look at the SSID but also the BSSID. I have a samsung tv that does this.
If we add the block-mount package to config and if we build and install it, when the router is rebooted we won't have Wi-Fi. We will have to wait approximately 40-60 seconds and restart each of the Wi-Fi radios to get it operational again. As an alternative, the router can be restarted and after this new restart the Wi-Fi network will be operational.
I hope I have expressed myself correctly and everything has been understood.
EDIT: I hope someone can confirm these findings.
Again, since you are the only one having the issue and only one that can bisect it.
You have to undo what that commit did but one patch at a time to find the exact one so it can get fixed
I could add that the mac adress of other devices changed after I activated the wifi devices when they are not set manually. I had that problem serveral times. After I acctivated wifi I coudn't reach the router anymore over lan but still over wireguard. So I found out that the local ip adresses changed because it altered the mac addresses of its devices. Hence I would like to support asvios findings and I think it makes sense to find out what is going on. Let me now if can be of help. But I am not a linux or openwrt expert.
First of all I really appriciate all of your work and dedication. I successfully flashed openwrt using the instructions. What I did not understand is point 2 of the instructions:
"2. If you already have OpenWrt use sysupgrade or LuCi “Flash new firware image” option, after this operation use script from https://github.com/itorK/nbg7815_tools/blob/main/change_boot_partition.sh to change boot partition"
Why is it necessary to flash OpenWrt again when it is already running? And what is the benefit of running the skript "change_boot_partition.sh"?
Some time ago there was a problem with the openwrt installation since there are several sets of partitions where openwrt can be installed on this device (mmcblk0p3-mmcblk0p4 and mmcblk0p7-mmcblk0p8)
Initially it was only possible to install to the mmcblk0p7-mmcblk0p8 set and to be able to install correctly you had to run "change_boot_partition.sh".
It also happened that if it was installed in the set mmcblk0p3-mmcblk0p4 openwrt would not update and you had to change the boot partition for it to update correctly.
Currently these problems do not occur as the installation and sysupgrade scripts have improved and these issues no longer exist that I know of.
the NBG7815 wiki is a bit outdated in this regard.
This point 2 should say something like:
If you already have a very old version of openwrt for this device, to upgrade to a newer version of openwrt you can use sysupgrade or LuCi “Flash new firmware image”. It may be necessary to run https://github.com/itorK/nbg7815_tools/blob/main/change_boot_partition.sh to change the boot partition if it does not update correctly.
And if you are going to upgrade to a newer version don't forget to run wpad stop and wait a few seconds before running the sysupgrade command. (there is a problem for all ipq8074 devices with the sysupgrade process)
If there is any error in what I have exposed, someone with more knowledge correct it
Has anyone tried firmwares built with NSS?
The repo belongs to @AgustinLorenzo
I cannot comment on the stability of AgustínLorenzo's or bitthief's nss-firmware and the advantages it has over the upstream version since I have not used them enough, but I have installed both, and what I can tell you is that if you need to use the port usb to share files do not use them because both present problems during the first reboot after the update and also the file exchange does not work.
It all comes for including the blockmount package in the build.
This problem seems to only affect this router since I haven't read anything similar with the other ipq807x devices on the forum.
And the 160Mhz channel width still does not work (although it does not work in the upstream version either) or at least I have not been able to make it work.
If you don't use blockmount package you can install it and commet how it works. (don't forget wpad stop before upgrade)
Thank you @asvio, that explains it. Luckily I did not use the script. Updating to a new snapshot went without any surprises. I did not have to stop wpad before.
Btw, I had lately also issue connecting with an AX210 Intel client. It did not link to a R7800 running OpenWrt 19. I figured out that it always connects to another Router. I figured out that it prefered the other router since it offered WPA2/WPA3 mixed security. The R7800 offered only WPA2. Before it was never a problem. So this was a new issue and I solved it by just enabling WPA2/WPA3 on all routers.
Hi all. I bought a zyxel nbg7815, according to the wiki article I downloaded the latest itorK firmware, the router freezes when loading:
[ 7.940737] NET: Registered PF_PPPOX protocol family
[ 7.948997] ath11k c000000.wifi: ipq8074 hw2.0
[ 7.949031] ath11k c000000.wifi: FW memory mode: 0
[ 7.952761] remoteproc remoteproc0: powering up cd00000.q6v5_wcss
[ 7.965791] remoteproc remoteproc0: Booting fw image IPQ8074/q6_fw.mdt, size 668
[ 8.653344] remoteproc remoteproc0: remote processor cd00000.q6v5_wcss is now up
[ 8.657621] kmodloader: done loading kernel modules from /etc/modules.d/*
[ 8.697252] ath11k c000000.wifi: qmi ignore invalid mem req type 3
[ 8.704714] ath11k c000000.wifi: chip_id 0x0 chip_family 0x0 board_id 0xff soc_id 0xffffffff
[ 8.704757] ath11k c000000.wifi: fw_version 0x270204a5 fw_build_timestamp 2022-08-04 13:05 fw_build_id WLAN.HK.2.7.0.1-01744-QCAHKSWPL_SILICONZ-1
The problem is that the bootloader does not accept keyboard input via uart, I can only read logs. Is this a problem with the bootloader or my usb-ttl dongle?