Now, I am going to take you to " back in the day " hearkening the good ole' times of yore - maybe some will remember " The Blue Lights In The Basement " we pay tribute in the time honored tradition of the " Intro " ( yes - it is mandatory ) showcasing these classics -- https://www.youtube.com/watch?v=ZY7fZ95XfMY and the lyrics to sing and hum along - https://www.lyricsfreak.com/l/linda+jones/for+your+precious+love+spoken_21111123.html and on a lighter note ( no pun intended ) - free yourself - https://www.youtube.com/watch?v=K9F5xcpjDMU - and keep the feeling - https://genius.com/Black-sheep-the-choice-is-yours-lyrics Surprise Bonus - https://www.youtube.com/watch?v=WjI3pzhXO14
AdGuardHome works flawlessly with both OpenVPN and WireGuard protocols.
No need for firewall rules or port forwarding with this set up. It works " as is "
right " OUT THE BOX ".
Attention : From OG Poster ( brokenpipe )
!!!! It is possible to install AdguardHome under /opt/,
but this directory can grow. Old binaries are moved as
backup after an update. blocklists can become relatively large. It is better
to move AdGuardHome to a USB stick. So it will survive
future OpenWRT updates !!!!
That Means Setup Exroot for your AdGuardHome Install If At All Possible
Here is a great deal on 4gb USB 3.0 Drives -
Made and Shipped In The Good Ole' USA :
USB KEYCHAIN KEY DRIVE 3.0 4 GB
YO ! : I strongly suggest that you watch this video before you begin. Although lengthy - it is very informative and worthwhile. Van Tech Corner OpenWRT AdGuard Home Video Van Tech Corner OpenWRT AdGuard Home. You also will be able to follow this guide much better - as a ( moving ) picture is worth a thousand words.
Follow directions carefully - you will have AdGuard Home up and running on OpenWRT by the end of this guide / tutorial. The setup uses UNBOUND. There is already a guide / tutorial incorporating DNSMASQ with AdGuard Home found here : OpenWrt AdGuard Home 101 ( DNSMASQ ) Many have stated " you don't need UNBOUND ". I answer that with " Well, I don't need custom made Armani suits or a Ferrari either. You see where I'm going with this ?
1 - First you will need to get the appropriate AdGuard Home package for your router's architecture. For example, I have WRT3200ACM, WRT32x, Wrt1900ACS V2, WRT1200AC, and NightHawk R7800. All of these have ARMv7 processors. You should find out your architecture before proceeding. Now there is a script on AdGuard Home - found here - https://github.com/AdguardTeam/AdGuardHome. However, I have never been able to get the automatic download and install script to work properly. So, I manually download and install AdGuard Home on OpenWRT, because this method is GUARANTEED ! to work.
In order to find your router's Architecture - go to Luci > Status >
Overview then under System - on the third line down underneath
Model ( indicating your router )
You will find your router's Architecture - for the router
I am currently running for example these are the entries below :
Model Netgear Nighthawk X4S R7800
Architecture ARMv7 Processor rev 0 (v7l)
Target Platform ipq806x/generic
You can also enter command below :
# cat /proc/cpuinfo
or you can install hwinfo / opkg update && opkg install hwinfo
and issue command below :
# hwinfo
### this will render all the specs for your router -
look at the beginning of readout for CPU
First, Install These Packages To Get Started - The Main One Needed is sudo - otherwise you will not be able to install AdGuardHome successfully - as always # opkg update
opkg update ; opkg install ca-certificates ca-bundle sudo libustream-mbedtls libustream-openssl libwolfssl libustream-wolfssl luci-ssl px5g-wolfssl wpad-basic-wolfssl luasocket curl libevent2-7 haveged unzip ip-full curl wget libmbedtls12 tar tcpdump-mini
then run # opkg update again - and then install packages for UNBOUND as indicated below :
opkg update ; opkg install unbound-daemon unbound-control unbound-control-setup luci-i18n-unbound-en luci-app-unbound unbound-anchor unbound-host unbound-checkconf
NOTE : When running DNS OVER TLS ( my setup ) - You first must stop and disable odhcpd. This setup depends on DNS functionality. odhcpd conflicts with dnsmasq for dhcp hence also DOT.
The commands are as below :
# /etc/init.d/odhcpd stop
# /etc/init.d/odhcpd disable
2 - There are two channels to download AdGuard Home - Beta and Edge. The consensus on the thread - found here : [HowTo] Running Adguard Home on OpenWrt - is to run Edge. As I mentioned earlier, make sure that you download the correct AdGuard Home package for your router's processor.
In my case that is the following link - https://static.adguard.com/adguardhome/edge/AdGuardHome_linux_armv7.tar.gz - notice that edge is named in the link.
A - Just copy and paste your correct link in your browser from this section of AdGuard Home - after downloading - you will have AdGuardHome_linux_armv7.tar.gz on your desktop. Create a folder to extract the archive into - and use WinRAR, 7Zip, PeaZip or some such file archiver to unzip AdGuardHome_linux_armv7.tar.gz ( remember to choose the proper package for your router ). You will now have a decompressed folder named " AdGuardHome " .
3 - Now we are going to use WINSCP, but first we need to create the default proper directory for AdGuard Home installation. Go into SSH shell - enter commands :
A - # mkdir -p /opt/
B - After creating directory, fire up WINSCP - open /opt/ directory on the
right side of the application - then Drag & Drop the AdGuardHome
decompressed folder from the directory you had it in on your desktop.
If you know how to use SCP on OpenWRT ( Linux ) you may use
that method here as well. After closing WINSCP - then issue this command
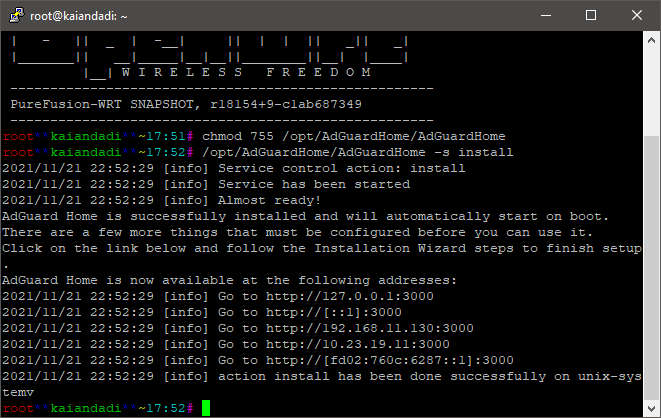
C - # chmod 755 /opt/AdGuardHome/AdGuardHome ## and then enter next
command for installation of AdGuardHome
D - # /opt/AdGuardHome/AdGuardHome -s install
You should be seeing something like below. Naturally you may see a different IP Address depending on your network interfaces - but you must use the LAN for initial AdGuardHome Configuration - here it is :
http://192.168.11.130:3000
4 - Pick out your LAN interface so that you can perform initial configuration of AdGuardHome . Now first I am going to show you how to use AdGuard Home with UNBOUND. Once again I implore you to look at Van Tech Corner OpenWRT AdGuard Home Video Van Tech Corner OpenWRT AdGuardHome
A - Choose LAN Address For Web Interface - Port 8080 / Choose Localhost ( 127.0.0.1 ) For DNS - Change to Port 5353
B - enter commands below ( again adjust for your actual LAN IP Address )
( a ) # uci add_list dhcp.@dnsmasq[-1].server='/pool.ntp.org/129.6.15.30'
## --- Your router date & time must be correct in order to have sucessful tls init
( b ) # uci add_list dhcp.@dnsmasq[-1].server='127.0.0.1#5353' # UNBOUND IPV4
( c ) # uci add_list dhcp.@dnsmasq[-1].server='::1#5353' # UNBOUND IPV6
( d ) # uci add_list dhcp.@dnsmasq[-1].server='192.168.11.130#8080' # Port used for Web Interface - use your actual LAN IP
( e ) # uci set dhcp.@dnsmasq[-1].noresolv=1 # Use only servers listed here in this file
( f ) # uci commit && reload_config
Note : Go into nano /etc/config/dhcp and modify file as detailed below :
### option resolvfile '/tmp/resolv.conf.d/resolv.conf.auto'
Make sure you disable (apply "###" in front) of entry above
in order to ignore ISP Supplied DNS Servers
5 - Configure Unbound - My WORKING CONFIG /etc/unbound/unbound_srv.conf
( Adjust For Your Router ) see here: https://nlnetlabs.nl/documentation/unbound/howto-optimise/
cat >> /etc/unbound/unbound_srv.conf <<UNBOUND_SERVER_CONF
# Use the root servers key for DNSSEC
tls-cert-bundle: /etc/ssl/certs/ca-certificates.crt
# use all CPUs
num-threads: 2
# more outgoing connections
# depends on number of cores: 1024/cores - 50
outgoing-range: 120
num-queries-per-thread: 30
max-udp-size: 3072
# power of 2 close to num-threads
key-cache-slabs: 1
# more cache memory, rrset=msg*2
msg-buffer-size: 8192
msg-cache-size: 100k
msg-cache-slabs: 1
num-queries-per-thread: 30
rrset-cache-size: 100k
rrset-cache-slabs: 1
infra-cache-slabs: 1
# Larger socket buffer. OS may need config.
so-rcvbuf: 4m
so-sndbuf: 4m
hide-identity: yes
hide-version: yes
hide-trustanchor: yes
harden-glue: yes
harden-dnssec-stripped: yes
harden-below-nxdomain: yes
serve-expired: yes
serve-expired-ttl: 3600
neg-cache-size: 10k
aggressive-nsec: yes
so-reuseport: yes
unwanted-reply-threshold: 10000
target-fetch-policy: "2 1 0 0 0 0"
val-clean-additional: yes
ip-ratelimit: 300
ip-ratelimit-factor: 10
outgoing-num-tcp: 1
incoming-num-tcp: 1
infra-cache-numhosts: 200
minimal-responses: yes
rrset-roundrobin: yes
use-caps-for-id: no
do-ip6: yes
do-ip4: yes
do-tcp: yes
do-udp: yes
prefetch: yes
prefetch-key: yes
qname-minimisation: yes
qname-minimisation-strict: yes
cache-min-ttl: 3600
cache-max-ttl: 14400
deny-any: yes
edns-buffer-size: 1232
UNBOUND_SERVER_CONF
then enter these two commands below :
# uci set 'unbound.@unbound[0].query_minimize=1'
# uci commit
6- Configure Unbound To Use AdGuardHome enter the following below :
cat >> /etc/unbound/unbound_ext.conf <<UNBOUND_FORWARD_CONF
server:
do-not-query-localhost: no
forward-zone:
name: "." # Allow all DNS queries
forward-addr: 127.0.0.1@5353
forward-addr: ::1@5353
UNBOUND_FORWARD_CONF
7 - Enter these commands below -
# Move dnsmasq to port 53535 where it will still serve local DNS from DHCP
# Network -> DHCP & DNS -> Advanced Settings -> DNS server port to 53535
( a ) # uci set 'dhcp.@dnsmasq[0].port=53535'
# Configure dnsmasq to send a DNS Server DHCP option with its LAN IP
# since it does not do this by default when port is configured.
( b ) # uci add_list "dhcp.lan.dhcp_option=option:dns-server,$(uci get network.lan.ipaddr)"
( c ) # uci set 'unbound.@unbound[0].dhcp_link=dnsmasq'
# Save & Apply (will restart dnsmasq, DNS unreachable until unbound is up)
( d ) # uci commit && reload_config
# Restart (or start) unbound (System -> Startup -> unbound -> Restart) - or
( e ) # /etc/init.d/unbound enable - then ( f ) # /etc/init.d/unbound start
8 - Disable Sending DNS Requests to ISP Provided DNS Servers
8 - Disable Sending DNS Requests to ISP Provided DNS Servers
( a ) # uci set network.wan.peerdns='0'
( b ) # uci set network.wan.dns='127.0.0.1'
( c ) # uci set network.wan6.peerdns='0'
( d ) # uci set network.wan6.dns='::1'
( e ) #uci commit && reload_config
9 - nano /etc/config/unbound - Configure Main UNBOUND FILE
config unbound 'ub_main'
option add_extra_dns '0'
option add_local_fqdn '1'
option add_wan_fqdn '1'
option dhcp4_slaac6 '0'
option dns64 '0'
option dns64_prefix '64:ff9b::/96'
option domain 'your.domain.here'
option domain_type 'transparent'
option edns_size '1232'
option extended_stats '1'
option hide_binddata '1'
option interface_auto '1'
option extended_luci '1'
option luci_expanded '1'
option listen_port '53'
option localservice '1'
option manual_conf '0'
option num_threads '2'
option protocol 'mixed'
option query_minimize '1'
option query_min_strict '1'
option rate_limit '0'
option rebind_localhost '0'
option rebind_protection '1'
option recursion 'aggressive'
option resource 'medium'
option root_age '9'
option ttl_min '120'
option unbound_control '1'
option validator '1'
option validator_ntp '1'
option verbosity '1'
list trigger_interface 'lan'
list trigger_interface 'wan'
option query_minimize '1'
list domain_insecure '3.us.pool.ntp.org'
list domain_insecure 'your.domain.here'
option dhcp_link 'dnsmasq'
10 - Run these three commands to complete UNBOUND
( a ) # unbound-checkconf
( b ) # unbound-control-setup
( c ) # unbound-anchor -a "/etc/unbound/root.key"
11 - Configure AdGuardHome via AdGuardHome.yaml for UNBOUND
We will edit the sections listed below :
( a ) dns: ( bind_hosts: )
( b ) upstream_dns:
( c ) bootstrap_dns:
( d ) all_servers:
( e ) filters:
( f ) # nano /opt/AdGuardHome/AdGuardHome.yaml
web_session_ttl: 720
dns:
bind_hosts:
- 127.0.0.1
- ::1
port: 5353
B - We will edit the sections listed below
( a ) upstream_dns: ( b ) bootstrap_dns: ( c ) all_servers:
upstream_dns:
- quic://dns.adguard.com:784
- quic://dot-jp.blahdns.com:784
- quic://dot-fi.blahdns.com:784
- quic://dot-sg.blahdns.com:784
- quic://dot-de.blahdns.com:784
- quic://doh.tiar.app:784
- quic://dns.emeraldonion.org:8853
- quic://uk.adhole.org:784
- quic://de.adhole.org:784
- quic://sg.adhole.org:784
- quic://dandelionsprout.asuscomm.com:48582
- quic://dns.arapurayil.com:784
- quic://dns.comss.one:784
- quic://dns.east.comss.one:784
- tls://getdnsapi.net
- tls://dns-nyc.aaflalo.me
- tls://dns.cmrg.net
- tls://dot.ny.ahadns.net
- tls://dot.la.ahadns.net
- tls://dot.chi.ahadns.net
- tls://ordns.he.net
- tls://us-east.adhole.org
- tls://dns.neutopia.org
- tls://dns.digitale-gesellschaft.ch
- tls://dot.sb
- tls://draco.plan9-ns2.com
upstream_dns_file: ""
bootstrap_dns:
- 1.1.1.2:853
- 1.0.0.2:853
- 2606:4700:4700::1112:853
- 2606:4700:4700::1002:853
all_servers: true
Above I used Cloudflare with Malware Blocking DNS using Encryption -
if you prefer Cloudflare Plain DNS then it is :
bootstrap_dns:
- 1.1.1.1
- 1.0.0.1
- 2606:4700:4700::1111
- 2606:4700:4700::1001
all_servers: true
and for Cloudflare Plain DOT Servers using Encryption -
where you enter your own valid SSL certificates chain for your domain :
bootstrap_dns:
- 1.1.1.1:853
- 1.0.0.1:853
- 2606:4700:4700::1111:853
- 2606:4700:4700::1001:853
all_servers: true
C - Enter the following below for filters :
filters:
- enabled: true
url: https://adguardteam.github.io/AdGuardSDNSFilter/Filters/filter.txt
name: AdGuard DNS filter
id: 1
- enabled: true
url: https://badmojr.github.io/1Hosts/Lite/adblock.txt
name: 1Hosts (Lite)
id: 1635566025
- enabled: true
url: https://raw.githubusercontent.com/durablenapkin/scamblocklist/master/adguard.txt
name: Scam Blocklist by DurableNapkin
id: 1625359388
- enabled: true
url: https://block.energized.pro/basic/formats/hosts.txt
name: Energized Basic Protection
id: 1625359389
- enabled: true
url: https://raw.githubusercontent.com/StevenBlack/hosts/master/hosts
name: https://github.com/StevenBlack/hosts
id: 1625359390
- enabled: true
url: https://osint.digitalside.it/Threat-Intel/lists/latestdomains.txt
name: https://firebog.net/ - OSINT.digitalside.it
id: 1625359391
- enabled: true
url: https://v.firebog.net/hosts/Easyprivacy.txt
name: https://firebog.net/ - EasyPrivacy
id: 1625359393
whitelist_filters:
- enabled: true
url: https://raw.githubusercontent.com/anudeepND/whitelist/master/domains/whitelist.txt
name: https://github.com/anudeepND/whitelist
id: 1625359392
user_rules: []
D - From Original Post [HowTo] Running Adguard Home on OpenWrt
Adguard Home Regex:
Those are really good regex rules which already block 50% of all ads/trackers/bots etc.
You have to add the to http://192.168.11.130:8080/#custom_rules
( as per this example - use your actual LAN IP )
https://github.com/mmotti/adguard-home-filters/blob/master/regex.txt
Configure Via /opt/AdGuardHome/AdGuardHome.yaml :
nano /opt/AdGuardHome/AdGuardHome.yaml
user_rules:
- https://github.com/mmotti/adguard-home-filters/blob/master/regex.txt
dhcp:
After configuring AdGuardHome via AdGuardHome.yaml one or both of the commands below :
a - # /etc/init.d/AdGuardHome restart
b - # /etc/init.d/dnsmasq restart
12- I strongly recommend enabled Encryption. With Encryption AdGuard Home admin interface will work over HTTPS, and the DNS server will listen for requests over DNS-over-HTTPS and DNS-over-TLS. For Encryption = Go To Top of AdGuardHome WEB GUI - Settings > Encryption settings the follow instructions
( a ) - enable Encryption - check the Box
( b ) - Fill in full server name such as this example - freedom.babybaby.mywire.org from my tutorial below : Dynu OpenWRT ACME LET’S ENCRYPT
( c ) Certificates :
In order to use encryption, you need to provide a valid SSL certificates chain for your domain.
You can get a free certificate on LetsEncrypt.org or you can buy it from one of the trusted Certificate Authorities.
If you follow my tutorial above you can issue yourself a LetsEncrypt Certificate cost free.
Cross referencing my tutorial above your certificate and key would be the following below :
a - /root/.acme.sh/freedom.babybaby.mywire.org/fullchain.cer
b - /root/.acme.sh/freedom.babybaby.mywire.org/freedom.babybaby.mywire.org.key
You have the option to " set the path " ( use a & b above ) or copy and paste them into the appropriate boxes found at the bottom of Encryption settings page.
You must move Luci to different port than 443 see commands below :
c - # nano /etc/config/uhttpd
list listen_https '0.0.0.0:1443'
list listen_https '[::]:1443'
You may now log into Encrypted AdGuardHome WEB GUI -
this option is available by entering the following ( from example above ) :
https://freedom.babybaby.mywire.org:443 - with Encryption Enabled
you will see " green padlock " when logging in / your certificate pulls double duty.
Since you moved OpenWRT Admin Port to Port 1443 you may still log into your Luci Encrypted WEBGUI at :
https://freedom.babybaby.mywire.org:1443
How To Upgrade Your AdGuardHome Install :
Some claim that you can upgrade from AdGuardHome WEBGUI - it has never worked
for me while running OpenWRT. No need to fear - here is how to upgrade when new EDGE
Version pops up. Hopefully, if you initially Setup Exroot for your AdGuardHome Install
( that means on a USB Stick ) then all you have to do is grab the new
installation by doing exactly what you did when
you first installed AdGuardHome. With Exroot - you do not have to worry about
any space issues - this is why we recommend Exroot to begin with.
1 - Download the correct AdGuard Home package for your router's processor.
2 - Create a folder to extract the archive into - and use WinRAR, 7Zip, PeaZip or
some such file archiver to unzip AdGuardHome_linux_your_router.tar.gz
3 - You will now have a decompressed folder named " AdGuardHome " .
4 - Then issue this command below :
# /etc/init.d/AdGuardHome stop
5 - Fire up WINSCP - open /opt/ directory on the right side of
the application - then Drag & Drop the AdGuardHome
decompressed folder from the directory you had it in on your desktop.
If you know how to use SCP on OpenWRT ( Linux ) you may use
that method here as well.
6 - After you drag and drop new AdGuardHome into the /opt/ directory
( overwriting the old installation ) - then enter these commands :
a - # /etc/init.d/AdGuardHome restart
b - # /etc/init.d/dnsmasq restart
You have now upgraded your AdGuardHome Install on OpenWRT.
Peace Stay Safe and God Bless All Always
PS - I started this journey in order to learn how to use DNS-over-QUIC, or DoQ.
In full disclosure I exclusively use DNS-over-QUIC upstream servers with AdGuardHome.
Also, I used Encryption for DNS OVER TLS bootstrap servers.
So - the whole damn thing ( my DNS ) is encrypted. Special thanks to mercygroundabyss
for his devotion to this project, his time and patience for all with inquiries, and most of all his
kindness and thoroughness in demeanor and practice.
BTW, I certainly will not at all miss having to update the SPKI PIN Keys
for DOT SERVERS in the Stubby yaml configuration file.
Bonus Feature:
For Those Who Care To PIMP Their AdGuardHome WEBGUI
You must install Stylish Addon To Use AdGuardHome Dark Theme
Firefox addon : https://addons.mozilla.org/en-US/firefox/addon/stylish/
Chrome extension : https://tinyurl.com/yntw4wyw
Go here - For Stylish Dark Themes :
I use XENORCHISM -
You must enter your LAN IP ADDRESS IN " Customize Settings " Box prior to installation
If you enabled Encryption with a valid SSL certificates chain for your domain - then enter
your Full Domain Name in " Customize Settings " Box prior to installation instead of LAN IP.
As per this example, Full Domain Name in
" Customize Settings " Box see below :
freedom.babybaby.mywire.org
You may then access AdGuardHome WEBGUI on port 443 - here is example from above :
https://freedom.babybaby.mywire.org:443 - with Encryption Enabled
you will see " green padlock " when logging in / your certificate pulls double duty
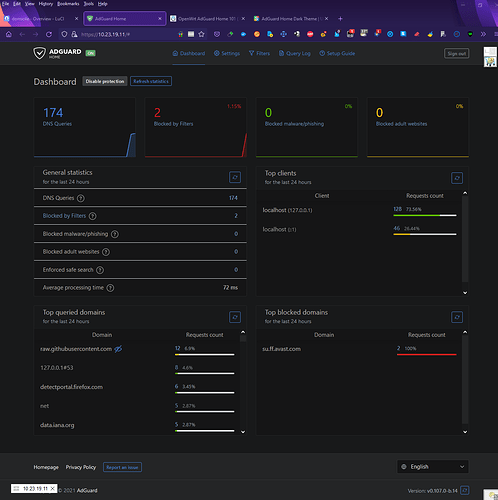
Here Is What You Get After Install :