What I am missing? I followed the instructions in the doc and I am not able to connect.
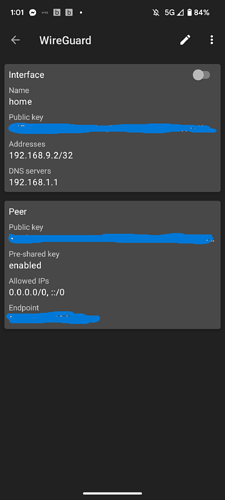
Pulled the QR Code on my phone
[Peer]
In the wg client on the phone, I set the ip address as 192.168.9.2/32
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
config globals 'globals'
config device
config interface 'lan'
config interface 'WAN'
config interface 'vpn'
config wireguard_vpn 'wgclient'
mk24
December 4, 2022, 2:47pm
2
That looks like it should work.
I'm assuming the server is also your main router. You will need to open port 51820 UDP on the router and make sure the ISP allows incoming connections direct to your house without NATing them. The WAN IP status must match the IP reported by "whats my IP" sites and also be the IP entered in DNS if you are using DDNS.
When testing turn off the WiFi in the phone so it is linking from outside via the cellular network. It generally won't work to test from inside the LAN.
Yes, the server is my router. I assume you mean port forward on the firewall?
Correct, wireless is turned off on the phone and still not connecting
mk24
December 4, 2022, 3:43pm
4
Open the port, don't forward it. Wireguard is an internal service in the router, not a machine on the LAN.
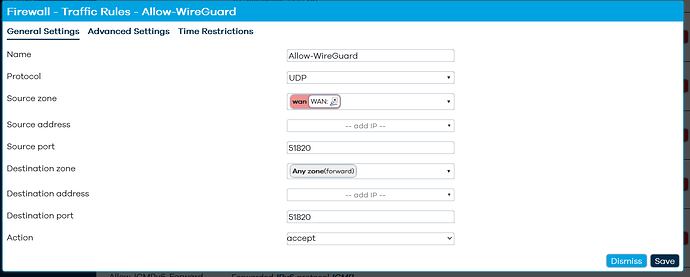
This is a Traffic Rule. Give it a name, choose UDP only, choose wan as the Source Zone, Any Zone as the Destination, and enter 51820 as the Destination Port. Leave the other fields blank / unspecified.
3 Likes
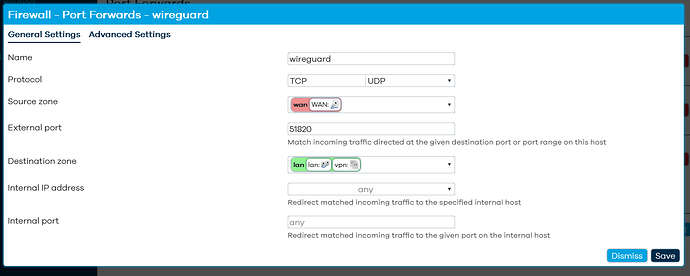
There already was a traffic rule. Still not able to connect.
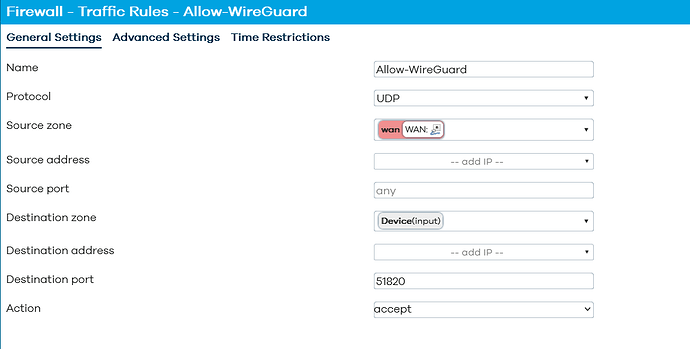
@mk24 correctly identified one key issue with your firewall. But I would make the destination zone “this device”. Remove the source port. There should only be a destination port. Also Make sure there are no other rules acting on that port.
Your phone needs an interface address - it is likely empty currently. Manually edit the wg config on your phone and add 192.168.9.2 into the interface address field.
On the router, you need to enable the route allowed ips option in the peer configuration section.
You need the wireguard network to be assigned to a firewall zone. You can simply add it to the lan zone, but make sure that has been done.
finally, it is important to verify that your isp is providing you with a public ip address. Look at the ipv4 upstream address shown on the main status page of the router and compare that to the result from googling “what’s my ip”. If they do not match, it means you don’t have a public ip and you won’t be able to connect if in doubt, post the first two octets of the address you see on the router (the parts in bold: aaa.bbb .ccc.ddd).
@psherman I made the change to the traffic rules and no other rules are acting on that port.
Check the phone and it reads out as 192.168.9.2/32
enabled route allowed ips in the peer configuration
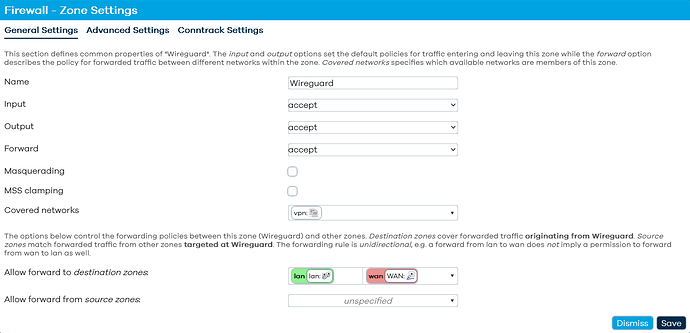
Is this the correct config for the firewall zone?
what's my ip and what is reporting on the router are the same ip address
If you want internet access via your wg tunnel for the phone, you need to also allow forwarding from the vpn zone > wan zone.
You don’t appear to have associated the actual network interface to that firewall zone e, but otherwise it is fine.
And you will probably need to set a dns server in the phone wireguard interface definition. It can be your routers lan address or a public dns like 8.8.8.8
I am not following. Are you talking about adding wan to the allow forward to destination zones or adding wan to the allow forward from source zones?
I did add my routers lan address to the phone wireguard interface.
I appreciate all the help
You want to have the following configuration:
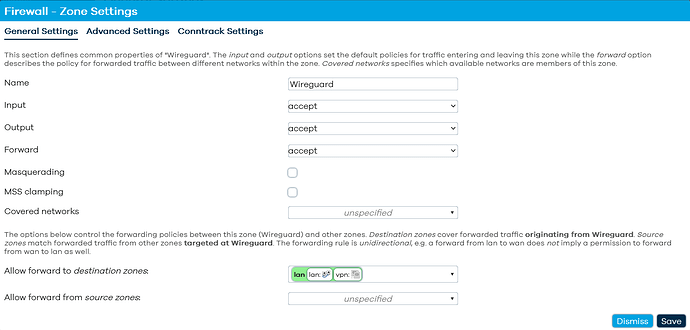
wireguard network "vpn" associated with the fireawall zone "Wireguard"
Zone forwarding ("allow forward to destination zones"): lan, wan
By this, hopefully you did this only in the DNS field.
Like this under the interface?
Here is my phones config
Is this what you meant for zone forwarding?
Yes, that's what I was talking about.
Does it work? Be sure to restart the router before you test.
Still no joy. This is frustrating
Any suggestions?
let's see the latest configs in text form:
Please copy the output of the following commands and post it here using the "Preformatted text </> " button:
cat /etc/config/network
cat /etc/config/firewall
also, please show your phone's wireguard config.
Sure thing
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd8d:7220:16c4::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
option delegate '0'
config interface 'WAN'
option proto 'dhcp'
option device 'eth1'
option peerdns '0'
list dns '1.1.1.1'
list dns '1.0.0.1'
config interface 'vpn'
option proto 'wireguard'
option private_key 'redacted'
option listen_port '51820'
option peerdns '0'
list dns '192.168.1.1'
list addresses '192.168.9.1/24'
config wireguard_vpn
option description 'Phone'
option public_key 'redacted'
option private_key 'redacted'
option preshared_key 'redacted'
list allowed_ips '192.168.9.2/32'
option route_allowed_ips '1'
option endpoint_host 'redacted'
option endpoint_port '51820'
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone 'lan'
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone 'wan'
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
list network 'wan'
list network 'wan6'
list network 'WAN'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'plex2022'
option src 'wan'
option src_dport '32400'
option dest_ip '192.168.1.243'
option dest_port '32400'
config redirect
option dest 'lan'
option target 'DNAT'
option name 'torrents'
option src 'wan'
option src_dport '64974'
option dest_ip '192.168.1.123'
config rule 'wg'
option name 'Allow-WireGuard'
option src 'wan'
option dest_port '51820'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'Wireguard'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'vpn'
config forwarding
option src 'Wireguard'
option dest 'lan'
config forwarding
option src 'Wireguard'
option dest 'wan'
Remove the lines marked with [remove] below
then restart the router.
on the phone:
Make sure that the endpoint on the phone is resolving to the public ip on your openwrt wan.
I removed the lines and rebooted the router.
Still not connecting
what is the output of wg show
just this
root@OpenWrt:~# wg show
interface: vpn
public key: redacted
private key: (hidden)
listening port: 51820