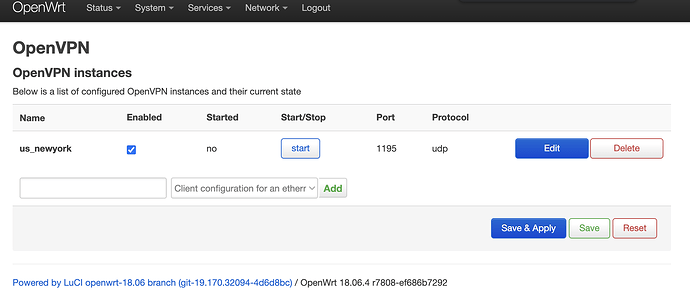
Hello,
I am a novice user of Openwrt and I am trying to enable ExpressVPN on my device using the following article
https://forum.openwrt.org/t/expressvpn-in-openvpn-on-openwrt-success/97986/3
but everytime i press the START button, the VPN does not connect and I get the following error messages from the system log.
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 1: config: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 2: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 3: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 4: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 5: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 6: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 7: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 8: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 9: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 10: list: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 11: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 12: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 13: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 14: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 15: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 16: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 17: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 18: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 19: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 20: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 21: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 22: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 23: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 24: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 25: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 26: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 27: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 28: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 29: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 30: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 31: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 32: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 33: option: not found
Mon Jan 16 21:44:38 2023 daemon.err uhttpd[2122]: /etc/init.d/openvpn: line 34: option: not found
Can someone please help me understand what i am doing wrong?
Thank you very much in advance.