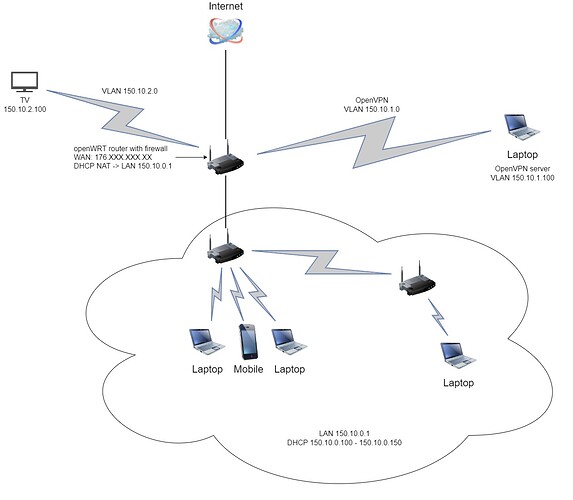
Hello,
I was trying to configure the connection through vpn, but no luck. Anyone knows how to configure the firewall on the openwrt to make it work?
I have to confess it is difficult to understand why the traffic is not forwarded they way I am doing it.
openvpn server is installed on Debian 10.
openvpn server (laptop) network settings
root@debian:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group defaul t qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: enp5s0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc pfifo_fast state D OWN group default qlen 1000
link/ether 00:23:5a:8d:1a:c0 brd ff:ff:ff:ff:ff:ff
3: wlp4s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:24:2c:44:6f:02 brd ff:ff:ff:ff:ff:ff
inet 150.10.1.100/24 brd 150.10.1.255 scope global dynamic noprefixroute wlp 4s0
valid_lft 43136sec preferred_lft 43136sec
inet6 fe80::90f9:7ed2:266:76b8/64 scope link noprefixroute
valid_lft forever preferred_lft forever
root@debian:~# ip r
default via 150.10.1.1 dev wlp4s0 proto dhcp metric 600
150.10.1.0/24 dev wlp4s0 proto kernel scope link src 150.10.1.100 metric 600
open vpn server config
cat /etc/openvpn/server/vpn-stage.conf
mode server
proto udp4
server 150.10.1.0 255.255.255.0
dev tun
persist-key
persist-tun
user nobody
group nogroup
ca /etc/ssl/private/vpn-stage/ca.crt
cert /etc/ssl/private/vpn-stage/vpn-stage.crt
key /etc/ssl/private/vpn-stage/vpn-stage.key
dh /etc/ssl/private/vpn-stage/dh.pem
tls-crypt /etc/ssl/private/vpn-stage/ta.key 0
plugin /usr/lib/x86_64-linux-gnu/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
tls-version-min 1.2
cipher AES-256-GCM
auth SHA256
tls-cipher TLS-ECDHE-ECDSA-WITH-AES-256-GCM-SHA384:TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384:TLS-DHE-RSA-WITH-AES-256-GCM-SHA384
keepalive 10 120
reneg-sec 86400
push "redirect-gateway autolocal"
push "route 150.10.0.0 255.255.255.0"
route 150.10.0.0 255.255.255.0 150.10.1.1
push "dhcp-option DNS 150.10.1.1"
status /var/log/openvpn/openvpn-status.log
verb 5
auth-nocache
openwrt firewall settings:
root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option masq '1'
option mtu_fix '1'
option network 'wan wan6 tun0'
option input 'REJECT'
option forward 'REJECT'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fc00::/6'
option dest_ip 'fc00::/6'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
option enabled '0'
config rule
option name 'Allow-IPSec-AH'
option src 'wan'
option dest 'lan'
option proto 'ah'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config rule
option src 'lan'
option target 'REJECT'
option name 'Turn-off-internet LAN'
option weekdays 'Sun Mon Tue Wed Thu Fri Sat'
option start_time '23:00:00'
option dest 'wan'
option stop_time '06:00:00'
config rule
option src 'TV'
option target 'REJECT'
option name 'Turn-off-internet TV'
option weekdays 'Sun Mon Tue Wed Thu Fri Sat'
option start_time '00:00:00'
option dest 'wan'
option stop_time '06:00:00'
config rule
option src 'TV'
option name 'TV DHCP and DNS'
option dest_port '53 67 68'
option target 'ACCEPT'
config rule
option name 'Allow-OpenVPN-Inbound'
option dest_port '1194'
option target 'ACCEPT'
option proto 'udp'
option src_port '1194'
option dest_ip '150.10.1.100'
option src '*'
option dest 'VPN'
config include
option path '/etc/firewall.user'
config zone
option forward 'REJECT'
option output 'ACCEPT'
option input 'REJECT'
option name 'TV'
option network 'VLAN_TV'
config forwarding
option dest 'wan'
option src 'TV'
config zone
option input 'ACCEPT'
option output 'ACCEPT'
option name 'VPN'
option network 'VLAN_VPN'
option forward 'REJECT'
config forwarding
option dest 'wan'
option src 'VPN'
config forwarding
option dest 'VPN'
option src 'lan'
config forwarding
option dest 'wan'
option src 'lan'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'VPN'
option proto 'tcp udp'
option src_dport '1194'
option dest_ip '150.10.1.100'
option dest_port '1194'
option name 'OVPN'
DHCP config
root@OpenWrt:/etc/config# cat /etc/config/dhcp
config dnsmasq
option domainneeded '1'
option localise_queries '1'
option rebind_protection '1'
option rebind_localhost '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option nonwildcard '1'
option localservice '1'
option strictorder '1'
option allservers '1'
option sequential_ip '1'
list server '9.9.9.9'
list server '149.112.112.112'
config dhcp 'lan'
option interface 'lan'
option start '100'
option limit '150'
option leasetime '12h'
list dhcp_option '6,149.112.112.112,9.9.9.9'
list dhcp_option '6,9.9.9.9,149.112.112.112'
config dhcp 'wan'
option interface 'wan'
option ignore '1'
config odhcpd 'odhcpd'
option maindhcp '0'
option leasefile '/tmp/hosts/odhcpd'
option leasetrigger '/usr/sbin/odhcpd-update'
option loglevel '4'
config dhcp 'VLAN_IoT'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'VLAN_IoT'
config dhcp 'VLAN_Guest'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'VLAN_Guest'
config dhcp 'VLAN_TV'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'VLAN_TV'
config dhcp 'VLAN_VPN'
option start '100'
option leasetime '12h'
option limit '150'
option interface 'VLAN_VPN'
NETWORK
root@OpenWrt:/etc/config# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd7f:1d41:10dd::/48'
config interface 'lan'
option proto 'static'
option ipaddr '150.10.0.1'
option netmask '255.255.255.0'
option ip6assign '60'
option type 'bridge'
option ifname 'eth1.4'
config interface 'wan'
option ifname 'eth0'
option proto 'dhcp'
option peerdns '0'
option dns '9.9.9.9 149.112.112.112'
config interface 'wan6'
option ifname 'eth0'
option proto 'dhcpv6'
option reqprefix 'auto'
option reqaddress 'none'
option auto '0'
option delegate '0'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option vid '1'
option ports '0t 1'
config switch_vlan
option device 'switch0'
option vlan '2'
option vid '2'
option ports '0t 2'
config interface 'VLAN_TV'
option type 'bridge'
option proto 'static'
option ifname 'eth1.3'
option ipaddr '150.10.2.1'
option netmask '255.255.255.0'
option dns '94.140.14.15 94.140.15.16'
config switch_vlan
option device 'switch0'
option vlan '3'
option vid '3'
option ports '0t 3'
config switch_vlan
option device 'switch0'
option vlan '4'
option vid '4'
option ports '0t 4'
config interface 'VLAN_VPN'
option type 'bridge'
option proto 'static'
option ipaddr '150.10.1.1'
option netmask '255.255.255.0'
option ifname 'eth1.1'
Attached network diagram