Hi,
I have created a short tutorial for a dual WAN dual OpenVPN failover scenario. I could not edit the wiki so I am posting it here.
== Dual VPN Howto ==
Objective: Open two VPN Tunnels, one through main WAN and one through LTE Backup, automatic failover to LTE when WAN fails
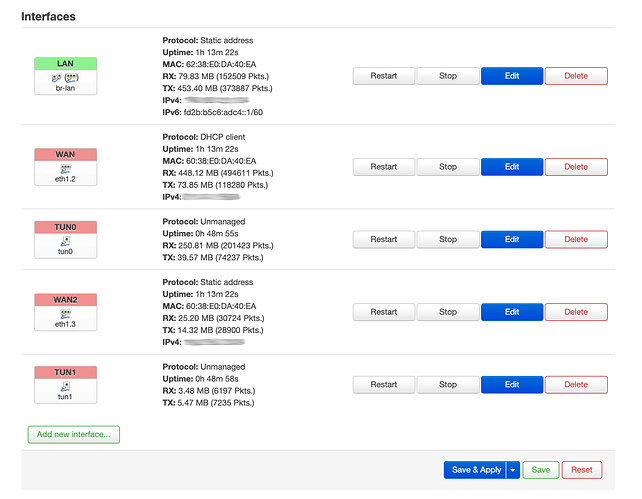
=== Create second WAN Port ===
In LUCI->Network->Switch create second VLAN
In LUCI->Network->Interfaces create WAN2 Interface, add to VLAN, add to Firewall wan Zone
If you disable WAN you should now be able to use WAN2 to reach the internet from LAN. If both are enabled the WAN with the lower gateway metric wins.
Through ssh you can use "ping -I eth1.2 8.8.8.8" and "ping -I eth1.3 8.8.8.8" to check whether both WAN ports work.
=== Create two TUN interfaces ===
Create TUN0 and TUN1 interfaces, both unmanaged, bring up on boot, firewall wan zone
=== Create two VPN connections ===
Create two VPN connections for your VPN provider. In the config add the following to make VPN1 use tun0 and VPN2 tun1. We also need to bind to the local IP address on WAN and WAN2 and we need to prevent routes from getting pushed. To debug run "logread -f" per SSH and see the OpenVPN output.
/etc/openvpn/vpn1.ovpn:
client
dev tun0
proto udp
local <wan ip addr>
pull-filter ignore redirect-gateway
remote <vpn1 ip 1>
remote <vpn1 ip 2>
remote <vpn1 ip 3>
...
/etc/openvpn/vpn2.ovpn:
dev tun1
proto udp
local <wan2 ip addr>
pull-filter ignore redirect-gateway
remote <vpn2 ip 1>
remote <vpn2 ip 2>
remote <vpn2 ip 3>
...
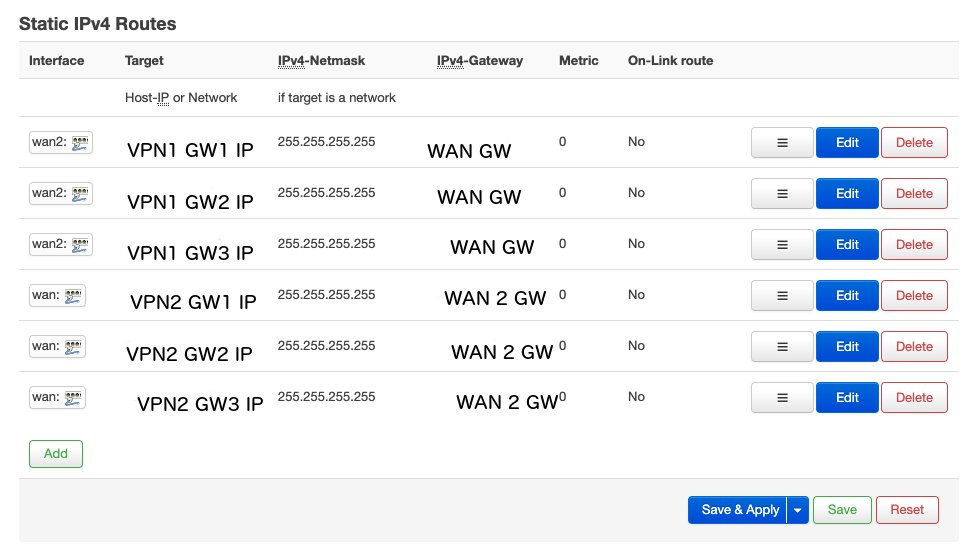
=== Set static routes ===
You should now be able to use both VPNs. You can start both and use "ping -I tun0 8.8.8.8" and "ping -I tun1 8.8.8.8" to see whether it works. But all traffic for tun1 gets routed through WAN not WAN2, therefore we need static routes to make traffic destined for VPN2 go through WAN2.
Take the remotes from the VPN config and route them through the appropriate interface in LUCI->Network->Static Routes.
Now if you start both VPNs and unplug WAN and do "ping -I tun1 8.8.8.8" it works, but "ping -I tun0 8.8.8.8" does not. If you unplug WAN2 and plug in WAN it is the other way around. Congratulations both VPNs work and traffic for the VPN1 remote gets routed through WAN and VPN2 through WAN2
If both VPNs are running the routes should look like this:
root@OpenWrt:~# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
default 0.0.0.0 UG 10 0 0 eth1.2
default 0.0.0.0 UG 20 0 0 eth1.3
10.50.0.0 * 255.255.0.0 U 0 0 0 tun1
10.52.0.0 * 255.255.0.0 U 0 0 0 tun0
<vpn1 ip 1> 255.255.255.255 UGH 10 0 0 eth1.2
<vpn1 ip 2> 255.255.255.255 UGH 10 0 0 eth1.2
<vpn1 ip 3> 255.255.255.255 UGH 10 0 0 eth1.2
<vpn2 ip 1> 255.255.255.255 UGH 20 0 0 eth1.3
<vpn2 ip 2> 255.255.255.255 UGH 20 0 0 eth1.3
<vpn2 ip 3> 255.255.255.255 UGH 20 0 0 eth1.3
<WAN2> * 255.255.255.0 U 20 0 0 eth1.3
<LAN> * 255.255.255.0 U 0 0 0 br-lan
<WAN1> * 255.255.255.0 U 10 0 0 eth1.2
=== MWAN3 ===
Now install and configure MWAN3. My config looks like this:
root@OpenWrt:~# cat /etc/config/mwan3
config globals 'globals'
option mmx_mask '0x3F00'
option rtmon_interval '5'
config rule 'default_rule'
option dest_ip '0.0.0.0/0'
option proto 'all'
option sticky '0'
option use_policy 'vpn_failover'
config interface 'tun0'
option enabled '1'
option initial_state 'online'
option family 'ipv4'
list track_ip '8.8.8.8'
list track_ip '8.8.4.4'
option track_method 'ping'
option reliability '1'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '2'
option down '3'
option up '3'
option interval '3'
option recovery_interval '3'
option failure_interval '3'
config interface 'tun1'
option enabled '1'
option initial_state 'online'
option family 'ipv4'
list track_ip '8.8.8.8'
list track_ip '8.8.4.4'
option track_method 'ping'
option reliability '1'
option count '1'
option size '56'
option max_ttl '60'
option check_quality '0'
option timeout '2'
option down '3'
option up '3'
option interval '3'
option failure_interval '3'
option recovery_interval '3'
config member 'tun0_m3_w3'
option interface 'tun0'
option metric '3'
option weight '3'
config member 'tun1_m5_w10'
option interface 'tun1'
option metric '5'
option weight '10'
config policy 'vpn_failover'
list use_member 'tun0_m3_w3'
list use_member 'tun1_m5_w10'
option last_resort 'unreachable'