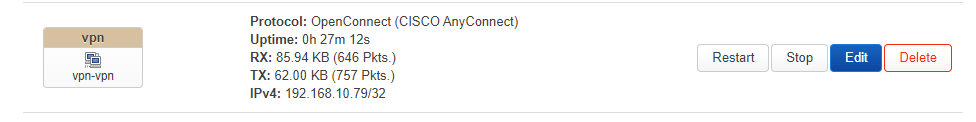
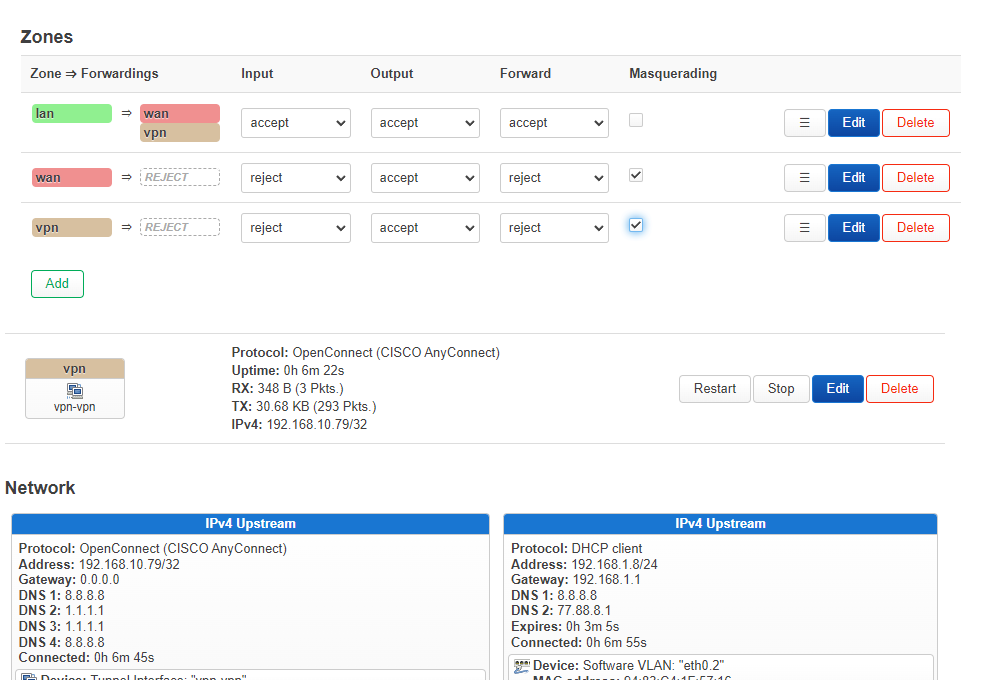
Hello. I have a problem connecting to the Internet when using openconnect (CISCO AnyConnect)." The connection to the server is up, but there is no Internet.
Initial data, ocserv server v.1.2.3, authentication by login and password, letscrypt certificates are installed on the computer, the CiscoAnyconnect client on Windows connects correctly, on the Android phone too, but there is a problem on openwrt.
OpenWrt 22.03.5
openconnect 9.01-1
luci-proto-openconnect git-23.093.42704-230ba69
System log
Thu Jan 4 19:25:18 2024 user.notice openconnect: executing 'openconnect 'https://xkmxw.webhop.me:443' '-i' 'vpn-vpn' '--non-inter' '--syslog' '--script' '/lib/netifd/vpnc-script' '--protocol' 'anyconnect' '--servercert=pin-sha256:dmOEtRuGpEnurJ9y9UmmEzDJ1PhmQnhwpzh6Y1J8RvM=' '--no-system-trust' '-u' 'any_user' '--passwd-on-stdin''
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Server certificate verify failed: signer not found
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Connected to HTTPS on xkmxw.webhop.me with ciphersuite (TLS1.3)-(ECDHE-SECP256R1)-(RSA-PSS-RSAE-SHA256)-(AES-256-GCM)
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): XML POST enabled
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Please enter your username.
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): POST https://xkmxw.webhop.me/auth
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Please enter your password.
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): POST https://xkmxw.webhop.me/auth
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Got CONNECT response: HTTP/1.1 200 CONNECTED
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): CSTP connected. DPD 90, Keepalive 32400
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): No DTLS address
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Set up UDP failed; using SSL instead
Thu Jan 4 19:28:06 2024 daemon.notice netifd: vpn (2258): Configured as 192.168.10.79, with SSL connected and DTLS disabled
Thu Jan 4 19:28:07 2024 daemon.notice netifd: Interface 'vpn' is now up
The interface shows the connection as working. An address from the required range was assigned
Here is my network config
root@OpenWrt:/etc/config# cat network
config interface 'loopback'
option device 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd08:78fc:0b73::/48'
config device
option name 'br-lan'
option type 'bridge'
list ports 'eth0.1'
config interface 'lan'
option device 'br-lan'
option proto 'static'
option netmask '255.255.255.0'
option ip6assign '60'
option ipaddr '10.10.10.1'
config interface 'wan'
option device 'eth0.2'
option proto 'dhcp'
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 6t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 6t'
config interface 'vpn'
option proto 'openconnect'
option vpn_protocol 'anyconnect'
option username 'any_user'
option password 'secret'
list dns '8.8.8.8'
list dns '1.1.1.1'
option delegate '0'
option port '443'
option server 'https://xkmxw.webhop.me'
option serverhash 'pin-sha256:dmOEtRuGpEnurJ9y9UmmEzDJ1PhmQnhwpzh6Y1J8RvM='
option defaultroute '0'
firewall
root@OpenWrt:/etc/config# cat firewall
config defaults
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
option synflood_protect '1'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
list network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option mtu_fix '1'
list network 'wan'
option masq '1'
config forwarding
option src 'lan'
option dest 'wan'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-IPSec-ESP'
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option name 'Allow-ISAKMP'
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config zone
option name 'vpn'
option output 'ACCEPT'
option forward 'REJECT'
list network 'vpn'
option input 'REJECT'
option mtu_fix '1'
config forwarding
option src 'lan'
option dest 'vpn'
ip show
root@OpenWrt:/etc/config# ip address show
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP qlen 1000
link/ether 94:83:c4:1f:57:16 brd ff:ff:ff:ff:ff:ff
inet6 fe80::9683:c4ff:fe1f:5716/64 scope link
valid_lft forever preferred_lft forever
5: br-lan: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 94:83:c4:1f:57:16 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.1/24 brd 10.10.10.255 scope global br-lan
valid_lft forever preferred_lft forever
inet6 fd08:78fc:b73::1/60 scope global noprefixroute
valid_lft forever preferred_lft forever
inet6 fe80::9683:c4ff:fe1f:5716/64 scope link
valid_lft forever preferred_lft forever
6: eth0.1@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 94:83:c4:1f:57:16 brd ff:ff:ff:ff:ff:ff
8: wlan0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue master br-lan state UP qlen 1000
link/ether 94:83:c4:1f:57:16 brd ff:ff:ff:ff:ff:ff
inet6 fe80::9683:c4ff:fe1f:5716/64 scope link
valid_lft forever preferred_lft forever
9: vpn-vpn: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN qlen 500
link/[65534]
inet 192.168.10.79/32 brd 255.255.255.255 scope global vpn-vpn
valid_lft forever preferred_lft forever
inet6 fe80::8bd7:d972:5bf9:db14/64 scope link flags 800
valid_lft forever preferred_lft forever
10: eth0.2@eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc noqueue state UP qlen 1000
link/ether 94:83:c4:1f:57:16 brd ff:ff:ff:ff:ff:ff
inet 192.168.1.8/24 brd 192.168.1.255 scope global eth0.2
valid_lft forever preferred_lft forever
inet6 fe80::9683:c4ff:fe1f:5716/64 scope link
valid_lft forever preferred_lft forever
routes
root@OpenWrt:/etc/config# ip route show
default via 192.168.1.1 dev eth0.2 src 192.168.1.8
10.10.10.0/24 dev br-lan scope link src 10.10.10.1
192.168.1.0/24 dev eth0.2 scope link src 192.168.1.8
192.168.10.0/24 dev vpn-vpn scope link
I would be grateful for any help.